An Android banking trojan and RAT called Klopatra masquerades as an IPTV and VPN app and has already infected more than 3,000 devices. The malware is a trojan capable of monitoring the device’s screen in real time, intercepting input, simulating gesture navigation, and is equipped with a stealth VNC (Virtual Network Computing) mode.
Experts from Cleafy, who discovered the malware, note that the trojan is not linked to any documented Android malware families and appears to be a project of a Turkish hacking group.
Klopatra is designed to steal banking credentials via overlays, exfiltrate clipboard contents and intercept keystrokes, drain victims’ accounts via VNC, and collect information about cryptocurrency wallet apps.
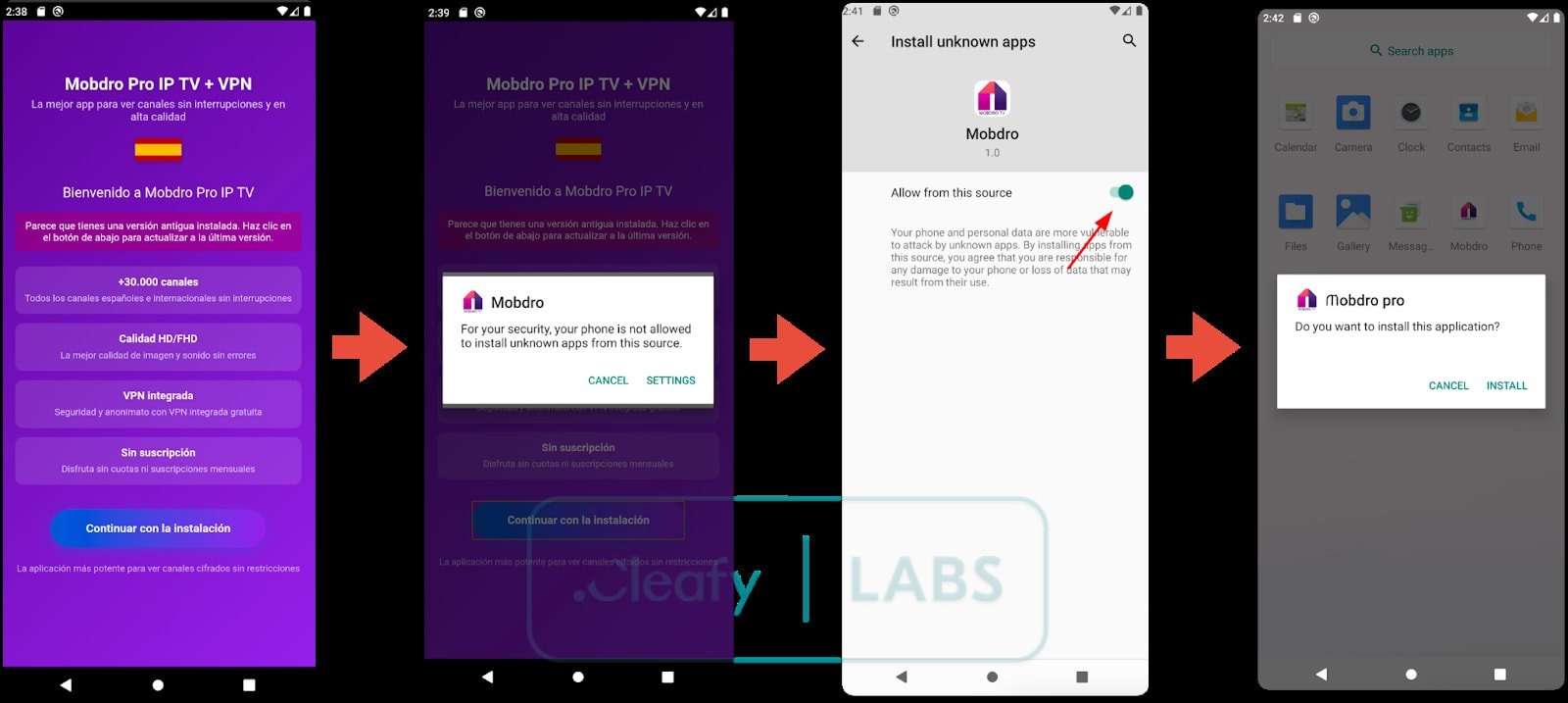
The malware infiltrates victims’ devices via a dropper app called Modpro IP TV + VPN, which is distributed outside the official Google Play store.
Klopatra uses Virbox (a commercial product that complicates reverse engineering and analysis), employs native libraries to reduce Java/Kotlin traces, and also encrypts strings using NP Manager.
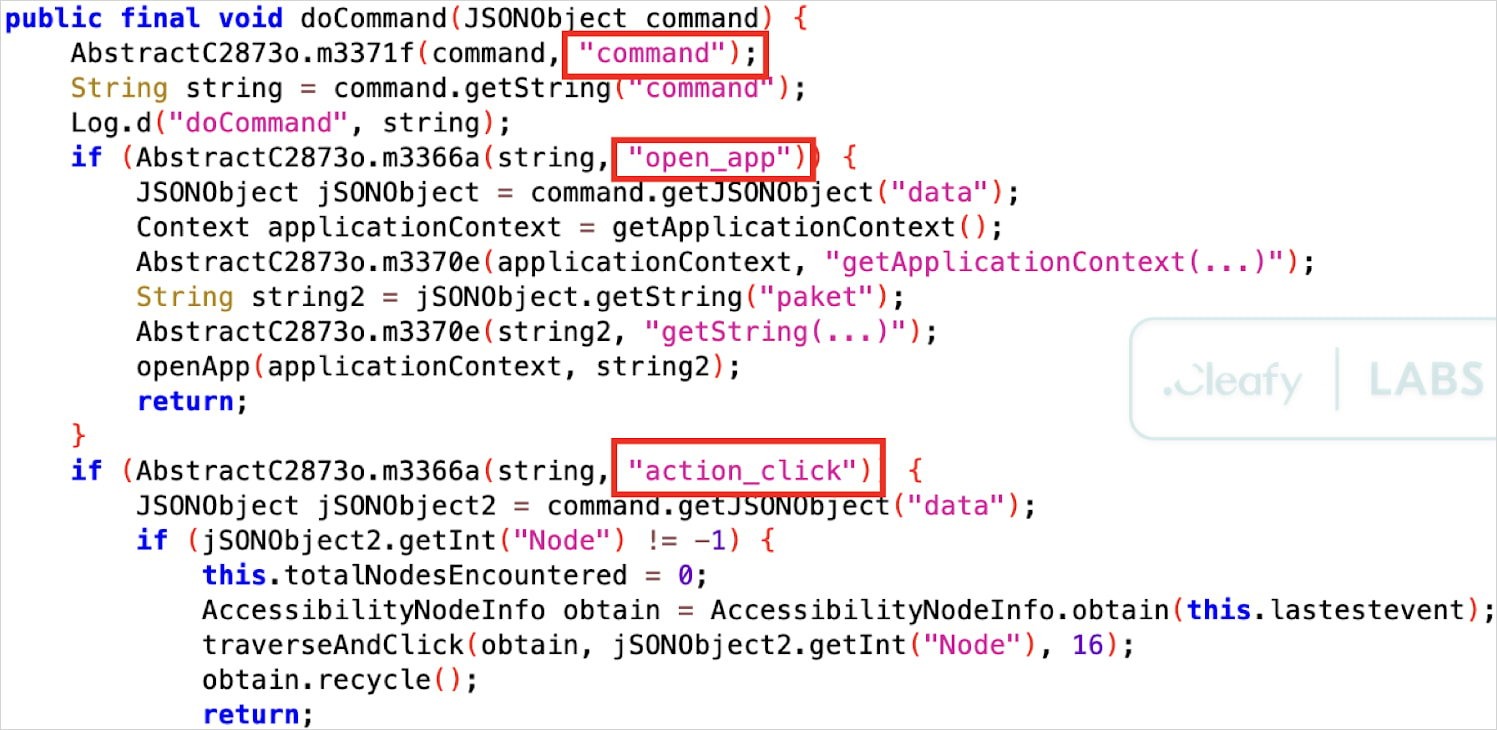
The banking trojan abuses the Android Accessibility service to grant itself additional permissions, intercept user-entered data, simulate taps and gestures, and monitor the victim’s device screen to obtain passwords and other confidential information.
One of the key features of the malware is a black-screen VNC mode that allows Klopatra operators to perform actions on the infected device. Meanwhile, to the user, everything looks as if the device is inactive and its screen is locked.
This mode supports all the remote actions required to perform banking transactions manually, including simulating taps at specified screen locations, swipes up and down, as well as long presses.
To choose the ideal moment to activate VNC mode, the malware checks whether the device is charging and whether the screen is off, so the user won’t suspect anything.
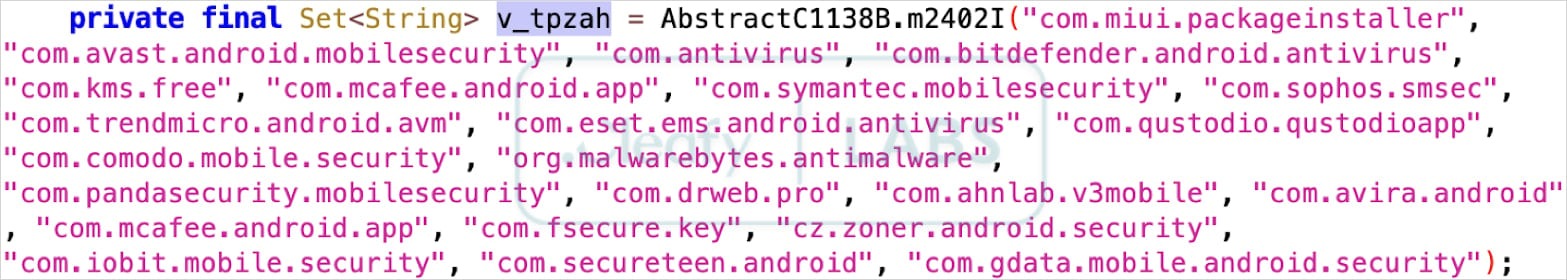
To avoid detection, Klopatra contains a hardcoded list of package names for popular Android antivirus apps and attempts to remove them.
Researchers at Cleafy have discovered several command-and-control servers for the malware. They are believed to be linked to two distinct campaigns that have already resulted in over 3,000 unique infections.
According to researchers, Klopatra has been active since March 2025, and about 40 different builds of the trojan have been released during this period, indicating active development and rapid evolution of the new banking trojan.
