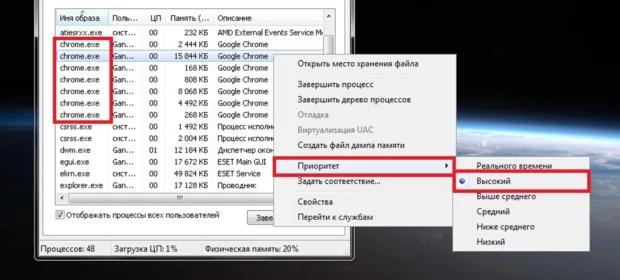
This isn’t a new topic, but it might still be useful to someone. How can you automatically launch processes with high or low priority without using third-party tools—just doing it yourself? I’ll demonstrate on Windows 7, but…
CONTINUE READING 🡒 Active Directory Audit: How to Find Inactive User Accounts by…
Once a domain has more than a few hundred users, keeping track of everyone gets tough. If the domain structure is complex and managed by multiple admins, it’s even harder. Throw in departures, promotions, lateral moves, and…
CONTINUE READING 🡒 Root Access on Recent Android Versions: What You Need to…
We cataloged the most common ways to get superuser access on current Android builds; unpacked the differences between SuperSU, phh SuperUser, Magisk, KingRoot, and KingoRoot; tested various methods of hiding root; examined Android 7’s security model and…
CONTINUE READING 🡒 Wi‑Fi USB Flash Drive Teardown: Capabilities and What’s Inside
We examined the internals of a Wi‑Fi–enabled USB drive and took a close look at how it operates. Appearances were deceiving, and our test results overturned our initial assumptions about the device. Below is our unedited, unsanctioned…
CONTINUE READING 🡒 What Data Google Has on You—and How to Export It…
As everyone knows, Google stores a vast amount of data about its users, a point it’s constantly criticized for. In response, Google built a tool that lets you export and download all your data. The service is…
CONTINUE READING 🡒 Monitor and Control: How to Audit and Track Everything on…
Are you sure you’re on top of everything happening on your system? Maybe you’re already using a monitoring stack like Prometheus or Zabbix, but do you know how to generate your own detailed reports on system and…
CONTINUE READING 🡒 Hunting Raccoon Stealer: How a Malware Developer’s OPSEC Failure Exposed…
In most cases, actors get unmasked because the malware author makes a basic OPSEC mistake. That’s what happened this time: the Trojan’s developer not only exposed himself but also gave away all his customers—much to the delight…
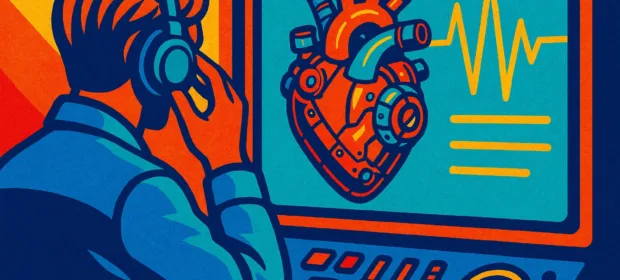
CONTINUE READING 🡒 Listen to your heart. Writing an account hijacking utility
Today, you will write a program that intercepts user credentials, transmits them to a remote host in real time, makes it possible to start multiple RDP sessions, and breaks competing connections. In fact, all you have to do is modify the Mimikatz code.
CONTINUE READING 🡒 Crypto Mining FAQ: What to Mine Today, How to Mine…
You hear the word “mining” everywhere these days—even from people far outside the IT world. Crypto exchanges are seeing unprecedented price swings, and in July the combined market cap of cryptocurrencies topped $100 billion. The hype is…
CONTINUE READING 🡒 Android: 8 Universal ROMs, Modern Click Bots, App Hacking, and…
In this issue: universal Android 8 ROMs, multi-headed trojans and chatbots, clickbots, abusing Android notifications, breaking into apps via trusted components, and of course a quick network pentest—how to make apps trust us. We didn’t forget coding…
CONTINUE READING 🡒 Android for Linux Users: Integrating Your Smartphone with Linux
Android and Linux distributions aren’t just related OSes—they share the same kernel and are very similar under the hood. Most Linux commands work on Android; you can install bash, write scripts, and even run servers. Set up…
CONTINUE READING 🡒 ReactOS: Why Trojans Run on the Windows Alternative but Microsoft…
On display in our cabinet of curiosities today is an unusual specimen—a twenty‑year‑gestating OS embryo learning to take its first steps. For now it can only stand and move gingerly, but it’s already trying to communicate with…
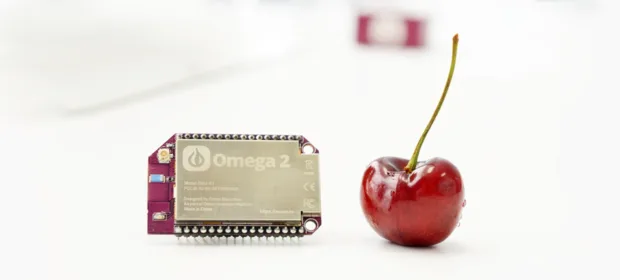
CONTINUE READING 🡒 Hands-on with the Omega2: What a Tiny, Low-Cost Linux Microcomputer…
Every maker eventually hits a point where basic microcontrollers just don’t cut it anymore, but dropping cash on a Raspberry Pi feels hard to justify. That’s where the modestly named Onion Omega2 comes in. It’s comparable to…
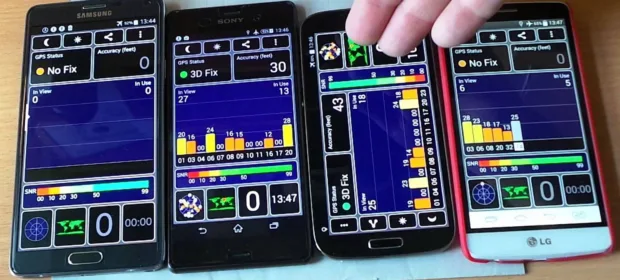
CONTINUE READING 🡒 How to Test and Improve GPS Signal Quality on Android
If you often find your phone struggles to get an accurate GPS fix, don’t rush to blame the navigation app. The problem is usually with GPS signal reception and satellite acquisition. You can test the receiver’s performance…
CONTINUE READING 🡒 Android SQLite Database: Quick Integration Guide
Android apps can store large amounts of data in a private, app-specific database—hidden from prying eyes. You’ll be surprised how useful this is and, more importantly, how easy it can be.
CONTINUE READING 🡒 Top 5 Web-Based Emulators for Classic Operating Systems and Retro…
Modern computers and browsers have reached impressive performance levels. Ten years ago, an interactive web app felt like a marvel; now JavaScript powers not just games, but even full-fledged emulators of vintage computers. We’ve picked a few…
CONTINUE READING 🡒 Automating x64dbg. How to transform a debugger into a hacker…
Why automate x64dbg? Because an automated debugger enables you to create custom tools for standard debugging tasks: unpack files, search for signatures, intercept or substitute function outputs on the fly, and even perform fuzzing in RAM! Let’s see how this can be done.
CONTINUE READING 🡒 3 Reasons to Skip the Latest Android Updates
For power users and app developers, Android has long been a very comfortable platform. Open-source code, rich capabilities, and the absence of heavy-handed control from Google made an Android smartphone a true pocket computer. But times change,…
CONTINUE READING 🡒 Hiding Sensitive Data in Android Apps: Techniques for Storing and…
At some point, almost every developer has had to hide data inside an app. This could be encryption keys used to decrypt parts of the program, API endpoint URLs, or strings you’d rather conceal to make a…
CONTINUE READING 🡒 How to Reduce Mobile Data Usage on Android: Practical Tips…
Cellular networks are delivering ever-faster Internet access, and mobile devices keep consuming more data. But mobile Internet is still far from cheap: plenty of users are still on plans capped at 4 GB, and when you travel,…
CONTINUE READING 🡒