Last week, Oracle warned customers about a critical 0-day vulnerability in E-Business Suite (CVE-2025-61882) that allows arbitrary code to be executed remotely without authentication. It has now come to light that the Clop hacking group has been actively exploiting this vulnerability in attacks since August 2025.
0-day under attack
A vulnerability was discovered in the Oracle Concurrent Processing component of Oracle E-Business Suite (the BI Publisher Integration module) and received a CVSS score of 9.8. The high score is due to the lack of required authentication and the ease of exploitation.
Oracle representatives reported that the 0-day affects Oracle E-Business Suite versions 12.2.3–12.2.14 and released an emergency update. At the same time, the company emphasized that before installing the patch, customers must first apply the October 2023 Critical Patch Update.
Since a public PoC exploit existed for the vulnerability and it had already been used in attacks, Oracle administrators were advised to install the update as soon as possible.
As reported by Charles Carmakal, CTO of the cybersecurity firm Mandiant, the CVE-2025-61882 issue and a number of other bugs patched in the July update were used by the Clop hacking group to steal data from Oracle E-Business Suite servers as far back as August 2025.
In addition, even before the patch was released, experts from Mandiant and Google Threat Intelligence Group (GTIG) warned that they were tracking a new malicious campaign linked to Oracle E-Business Suite. At that time, several unnamed companies received emails from the attackers. In these messages, representatives of Clop stated that they had stolen data from Oracle E-Business Suite and demanded a ransom, threatening to publish the stolen information otherwise.
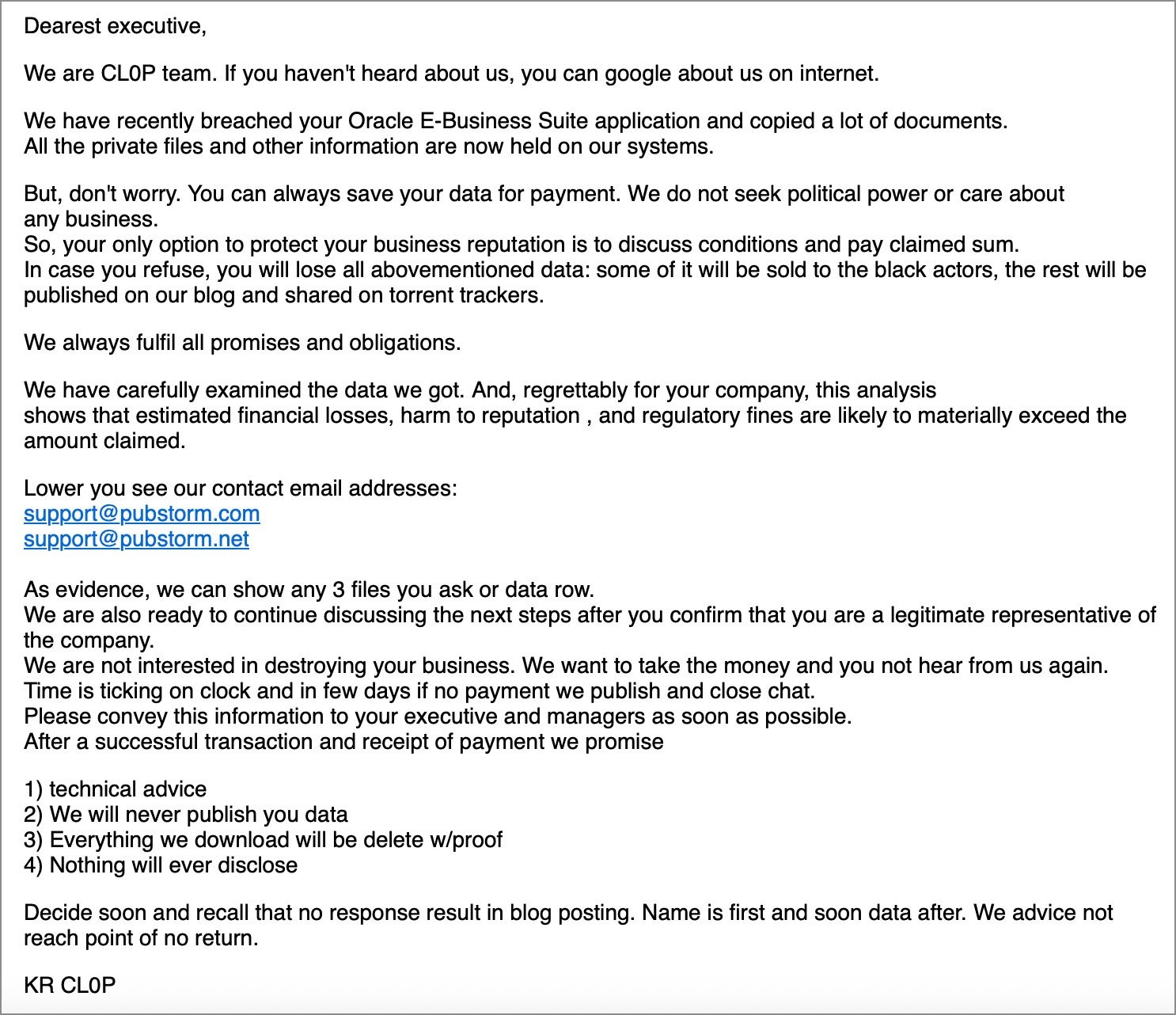
Analysts at CrowdStrike confirm that they first observed Clop attacks targeting CVE-2025-61882 in early August of this year. According to the researchers, other groups may also have been involved in the attacks.
“CrowdStrike Intelligence, with moderate confidence, believes that GRACEFUL SPIDER is likely involved in this campaign. We cannot rule out the possibility that CVE-2025-61882 is being exploited by multiple threat groups. The first known exploitation occurred on August 9, 2025; however, investigations are ongoing, and this date may change,” the specialists say.
Exploit
As noted by Bleeping Computer, although the Clop group is behind the data theft and exploitation of the 0-day, information about this vulnerability was first published by the Scattered Lapsus$ Hunters group (an alliance of members of the hacker groups Scattered Spider, LAPSUS$, and Shiny Hunters), which posted two files mentioning Clop on Telegram.
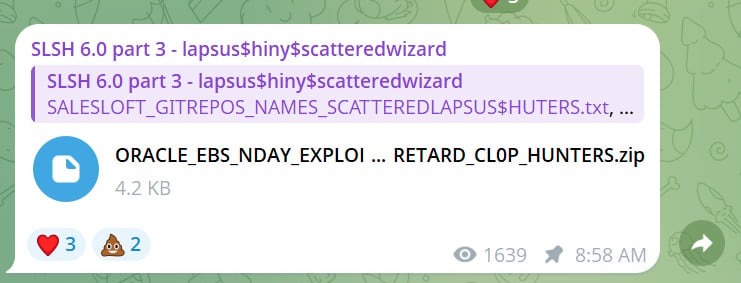
One of them (GIFT_FROM_CL0P.7z) contained Oracle source code, allegedly related to support.oracle.com. Later, Scattered Lapsus$ Hunters claimed that this code was stolen during the Oracle Cloud breach in February 2025.
The second file (ORACLE_EBS_NDAY_EXPLOIT_POC_SCATTERED_LAPSUS_RETARD_CL0P_HUNTERS.zip) allegedly contained the exploit itself for Oracle E-Business Suite used by Clop. The archive included a readme.md file and two Python scripts — exp.py and server.py. These scripts are used to exploit vulnerable Oracle E-Business Suite installations: they either execute an arbitrary command or open a reverse shell by connecting to the attackers’ servers.
It is still unclear how Scattered Lapsus$ Hunters gained access to the exploit and how they are connected to Clop. The hackers themselves claim that one of the people they shared the exploit with might have passed it on or sold it to Clop.
“It was my exploit, as in the case with SAP, which was later stolen by CCP. I was upset that another one of my exploits was being used by another group in an inept way, so we leaked it. No complaints against Clop,” a member of the group said.
As researchers at watchTowr Labs discovered after reverse-engineering an exploit leaked online by Scattered Lapsus$ Hunters and dated May 2025, CVE-2025-61882 is in fact a chain of vulnerabilities that allows attackers to achieve unauthenticated remote code execution with just a single HTTP request.
