Salesforce representatives said they do not intend to negotiate or pay a ransom to the attackers behind a series of large-scale attacks involving the theft of the company’s customer data. The hackers are currently trying to extort 39 companies whose data was stolen from Salesforce.
Last week, the group Scattered Lapsus$ Hunters (an alliance of members from the hacker groups Scattered Spider, LAPSUS$, and Shiny Hunters) launched a data leak site listing 39 organizations affected by data breaches related to Salesforce.
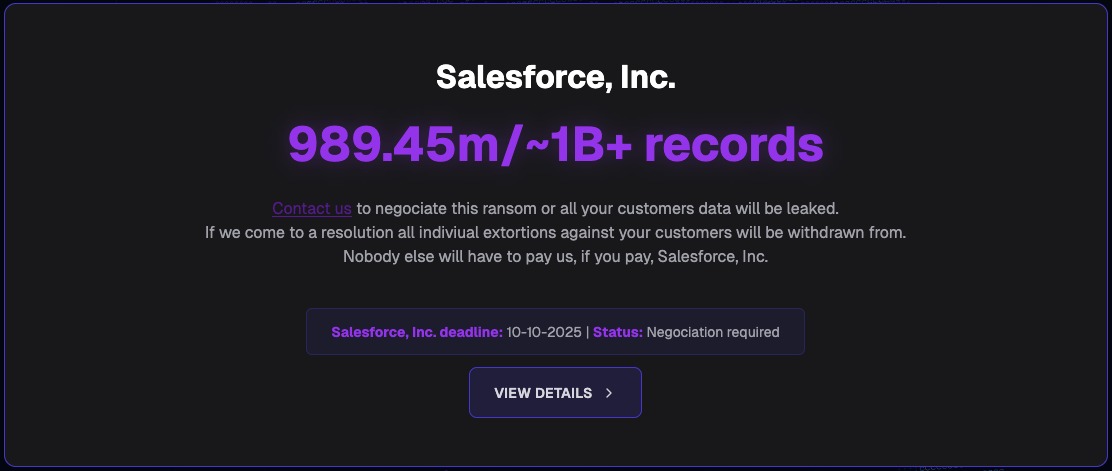
Each entry contains sample data stolen from Salesforce accounts and warns affected companies to contact the hackers by October 10, 2025, to prevent the public disclosure of all the stolen information.
Scattered Lapsus$ Hunters are attempting to extort numerous well-known brands and organizations, including: FedEx, Disney and Hulu, Home Depot, Marriott, Google, Cisco, Toyota, Gap, McDonald’s, Walgreens, Instacart, Cartier, Adidas, Saks Fifth Avenue, Air France and KLM, TransUnion, HBO Max, UPS, Chanel, and IKEA.
“We strongly urge you to make the right decision. Your organization will be able to prevent a data leak, regain control of the situation, and all operations will remain as stable as before. We strongly encourage the individuals responsible for decision-making to engage in this process, as we are offering a clear and mutually beneficial opportunity to resolve the issue,” the hackers write.
The attackers also posted a separate entry on their website addressed to Salesforce. The hackers demanded a ransom from the company to prevent the leak of all affected customers’ data (a total of about 1 billion records containing personal information).
“If you meet our demands, we will abandon any active and pending negotiations with your clients. If you pay, your clients will no longer be attacked and will not receive ransom demands from us,” the attackers say, addressing Salesforce.
Moreover, the extortionists are threatening the company, stating that after publishing the data they will help law firms file civil and commercial lawsuits against Salesforce, and they also warn that the company failed to protect its customers’ data in accordance with the requirements of the European General Data Protection Regulation (GDPR).
As Bloomberg now reports, this week Salesforce sent emails to its clients stating that it does not intend to pay a ransom or negotiate with the hackers. The company also warned that, “according to reliable information,” the attackers do indeed plan to publish the stolen data soon.
Recall that the data theft from Salesforce took place as part of two separate campaigns. The first began in late 2024. At that time, the attackers used social engineering (usually posing as tech support employees) to convince staff at various companies to connect a malicious OAuth application to their corporate Salesforce instances. After a successful connection, the attackers used the access they had obtained to download and steal data, and then extorted the companies.
Companies hit by such attacks and nearly identical breaches include Google, Adidas, airline Qantas, the insurer Allianz Life, several LVMH brands (Louis Vuitton, Dior and Tiffany & Co), the Cisco.com website, fashion house Chanel, Danish jewelry company Pandora, and others.
The second campaign began in August 2025. In this case, the hackers used OAuth tokens stolen from SalesLoft Drift to access customers’ CRM systems and exfiltrate information.
The attacks conducted through SalesLoft primarily aimed to steal support tickets, which can contain credentials, API tokens, authentication tokens, and other information that enables penetration into organizations’ internal infrastructure and cloud services.
Many large companies reported that this supply chain attack affected their systems. Among those affected: cybersecurity companies Zscaler, Proofpoint and Palo Alto Networks, SaaS platforms Workiva, PagerDuty and Exclaimer, the company Cloudflare, and so on.
On the data leak site set up by the hackers, most of the posted data belonged to victims of the first campaign, which used social engineering.
As noted by Bleeping Computer, the ransomware gang’s site is currently unavailable — the domain has switched to surina.ns.cloudflare.com and hans.ns.cloudflare.com, which were previously used by the FBI during domain seizures. However, the FBI has not yet commented on the situation.
