If you want to protect yourself from viruses, you need an antivirus, right? Not necessarily. Antivirus programs have many shortcomings, so if you use your head and are willing to rely on your own judgment, you can…
CONTINUE READING 🡒 Law Enforcement Dismantles Diskstation Group That Attacked NAS Devices
Law enforcement reported the dismantling of the Romanian ransomware hacker group Diskstation, which had previously successfully encrypted the systems of several companies in Italy, paralyzing their businesses.
CONTINUE READING 🡒 Malware XORIndex Discovered in 67 npm Packages
North Korean hackers have deployed 67 malicious packages on npm, through which a new malware loader called XORIndex was distributed. In total, the packages accounted for over 17,000 downloads.
CONTINUE READING 🡒 British Police Arrest Four Individuals Involved in Attacks on Retailers
The UK’s National Crime Agency (NCA) arrested four individuals suspected of involvement in attacks on major retailers in the country, including Marks & Spencer, Co-op, and Harrods.
CONTINUE READING 🡒 Cyber Intelligence Tools: Extracting Data from Instagram, Telegram, GitHub, and…
Open-source intelligence (OSINT) is not only a fascinating activity in its own right but also an essential skill that can be highly valuable in real investigations. Seasoned investigators typically use specialized tools, which we will discuss in…
CONTINUE READING 🡒 Self-defense for hackers. Detecting attacks in Active Directory
This article explains how to find out that a hacker is operating in your domain, how to automate the detection process, and how to repel attacks in Active Directory.
CONTINUE READING 🡒 Vulnerability in Railway Protocol Allows Train to Be Stopped Using…
Back in 2012, independent cybersecurity researcher Neil Smith reported to the U.S. government about a vulnerability in a communication standard used in trains. However, the issue has not yet been resolved, and the researcher’s concerns were dismissed…
CONTINUE READING 🡒 FileFix Technique Used for Delivering Interlock Malware
The ransomware hacking group Interlock is distributing a Remote Access Trojan (RAT) through compromised websites. The hackers use FileFix attacks to deliver the malware.
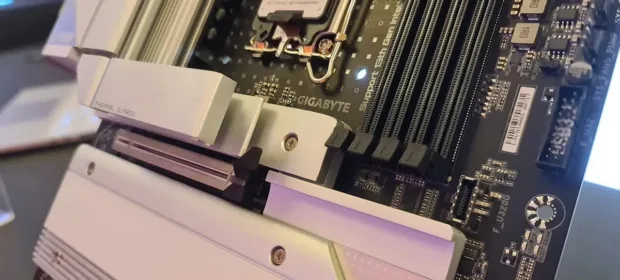
CONTINUE READING 🡒 Gigabyte Motherboards Vulnerable to UEFI Malware
Many models of Gigabyte motherboards utilize vulnerable UEFI firmware, which allows for the installation of bootkits that are invisible to the operating system.
CONTINUE READING 🡒 Exploring Endless OS: A Package-Free Linux Distribution
What does an average Linux distribution look like? Typically, it's a system assembled like a modular kit from thousands of packages, plus various desktop customizations, possibly its own installer and configuration system. In any case, almost all…
CONTINUE READING 🡒 Hackers Exploit Critical RCE Vulnerability in Wing FTP Server
Hackers began exploiting a critical vulnerability in Wing FTP Server just one day after technical details about the issue were published.
CONTINUE READING 🡒 eSIM Vulnerabilities Allow Card Cloning and User Spying
AG Security Research researchers have discovered vulnerabilities in the eSIM technology used in modern smartphones. The issues impact the eUICC software package by Kigen, which is used by billions of devices.
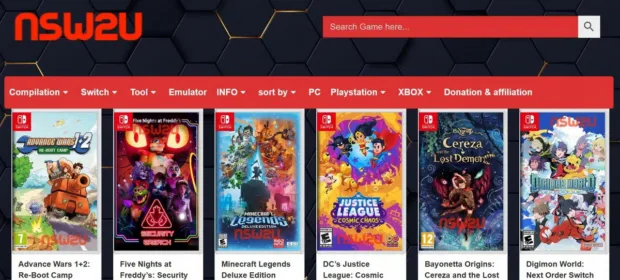
CONTINUE READING 🡒 FBI Shuts Down Websites Distributing Pirated Games
The Federal Bureau of Investigation (FBI) seized the domain names of several websites associated with pirated games. Notably, NSW2U[.]com, which Nintendo has been battling for many years, was shut down.
CONTINUE READING 🡒 Google Gemini May Direct Users to Phishing Sites
Google Gemini for Workspace can be used to create brief email summaries that appear legitimate but contain malicious instructions and messages directing users to phishing sites.
CONTINUE READING 🡒 How to Collect Telegram Chat Member Names for Data Analysis
Recently, I delved into the fascinating world of parsing Telegram chats and was surprised by how many repetitive questions people have, the lack of understanding among those who need parsing, and the number of scams and abuses…
CONTINUE READING 🡒 GPUHammer: Rowhammer Attack Adapted for Nvidia Graphics Cards
Nvidia recommends users activate System Level Error-Correcting Code (ECC), as graphics cards with GDDR6 memory are vulnerable to the Rowhammer attack.
CONTINUE READING 🡒 WordPress Plugin Developer for Gravity Forms Hacked, Backdoor Installed
The popular WordPress plugin Gravity Forms suffered from a supply chain attack. As a result, installers from the official website were infected with a backdoor.
CONTINUE READING 🡒 Understanding the Linux Boot Process: From Power-On to Desktop
The best way to understand how an operating system works is to trace its boot process step by step. It is during this boot process that all the mechanisms that get the OS up and running are…
CONTINUE READING 🡒 OAuth from top to bottom. Vulnerability chains and authentication attacks
This article discusses OAuth misconfigs. Normally, most of them are harmless, but under certain conditions, such misconfigs can entail severe consequences, including hacked admin accounts. Today you will learn how to search for vulnerability chains in OAuth.
CONTINUE READING 🡒 A Hacker’s Toolkit: 13 Essential Linux Utilities for System Administrators
True Linux warriors engage with the command line daily, and some practically live in it. In this collection, I've gathered tools that will make this lifestyle smoother, more efficient, and even a bit more enjoyable. These utilities…
CONTINUE READING 🡒