Most modern websites have an authentication form, and in its lower part you can often see buttons enabling you to sign in via various social networks. This login mechanism is based on the OAuth protocol, and today you’ll learn its structure and main vulnerabilities. At the…
CONTINUE READING 🡒 Puzzle solving. Writing custom JavaScript deobfuscator
Today, I am going to demonstrate that JavaScript obfuscation can be removed even in situations when sophisticated deobfuscators are useless. You will learn an effective research technique that can be applied to obfuscated code and write your own deobfuscator.
CONTINUE READING 🡒 Self-defense for hackers. Catching intruders at the network level
This article presents a number of simple but effective computer self-defense techniques that will help you to detect hackers who have penetrated into your local network. You will learn to identify penetration traces and catch intruders using special scripts. Let’s start with…
CONTINUE READING 🡒 Dumping at nanolevel. How I reinvented SafetyKatz to dump LSASS…
This article discusses the covert use of the NanoDump utility from memory (i.e. the simulated attacker doesn’t have a C&C ‘beacon’ on the attacked network node) and compares such an application of NanoDump with the use of SafetyKatz.
CONTINUE READING 🡒 Multistep SQL injection attacks: Operating principle and impact
SQL injections (SQLi) are among the most popular vulnerabilities in the pentesting community. Too bad, such attacks are increasingly rare nowadays since modern security tools easily detect them. By contrast, an injection triggered when data transfer occurs between services is much…
CONTINUE READING 🡒 Victory over “bads”: using Victoria to recover data and reset…
Recovering deleted files is not a problem; there are dozens of utilities for this. But what if the drive is damaged, has an erroneous geometry description, or is password protected at the controller level? Then the Victoria utility comes to the rescue. It is written in assembler, takes up…
CONTINUE READING 🡒 Console Android. 50 ADB Commands Everyone Should Know
There are many tools available for working with a smartphone connected via USB cable or Wi-Fi. Advanced tools allow you to move files, install and uninstall software, view contacts, take screenshots, and even send SMS, but no graphical tool can match the power that…
CONTINUE READING 🡒 We cover our tracks. How to make Windows forget everything
Lists of open files and USB devices, browser history, DNS cache – all this helps to find out what the user was doing. We have compiled step-by-step instructions on how to remove traces of your activity in different versions of Windows, Office and popular browsers. At the end…
CONTINUE READING 🡒 From the Dead in 80 seconds. Bringing the bricked smartphone…
Most of the articles in the X-Mobile section are devoted to hacks and tweaks that require rooting, modifying the firmware, or replacing it with a custom one. However, not every reader is ready to subject their smartphone to such operations, fearing that they can turn the device into…
CONTINUE READING 🡒 A darknet trip. Take the greenest places .onion
The word “darknet” has almost become a cliché for everything that is taboo, difficult to access, and potentially dangerous. But what is a real darknet? We’re offering you another study sharing everything we’ve been able to dig up lately. This time – with…
CONTINUE READING 🡒 Linux in 30 minutes. A Beginner’s Guide to Choosing and…
It doesn’t matter which operating system you prefer to have on your desktop, Linux is literally everywhere today: on servers, on hardware like Raspberry Pi, on smart devices, on computers in government institutions… Well, even in Windows, you can now run LinuxLinux to make it easier, for…
CONTINUE READING 🡒 Python via Telegram! Writing five simple Telegram bots in Python
In this article, we are implementing a simple but extremely useful project in Python — a bot for Telegram. Bots are small scripts that can interact with the API to receive messages from the user and send information to different chats and channels.
CONTINUE READING 🡒 Python from absolute zero. Working with OS, learning regular expressions…
Today, we will work with the OS file system — we will learn how to navigate through directories, open and change files. Then, we’ll master the powerful spells called “regular expressions,” learn the intricacies of creating and calling functions, and finally write a simple SQL vulnerability scanner.…
CONTINUE READING 🡒 Python from absolute zero. Learning to work with strings, files,…
One day, Crocodile Gena and Cheburashka were asked to write an essay on the topic ’How I spent my summer.’ The problem was that the friends drank beer all summer. Gena, who can’t lie, wrote it that way, so Cheburashka had to replace some…
CONTINUE READING 🡒 Python from absolute zero. Learning to code without boring books
If you think a hacker doesn’t need programming, you’re deeply mistaken! Yes, you can rock Kali Linux and use premade programs, copy code from forums, and blindly download scripts from GitHub. But your skill limit until you learn to write and understand…
CONTINUE READING 🡒 More than 60 malicious NPM packages are stealing user data
Socket’s Threat Research Team discovered an active campaign involving dozens of malicious npm packages that collect and leak information from victims’ systems.
CONTINUE READING 🡒 MathWorks affected by ransomware attack
MathWorks, Inc., an American corporation specializing in mathematical computing software, was affected by a ransomware attack resulting in service interruptions.
CONTINUE READING 🡒 Bring Your Own Vulnerable Driver! Meet BYOVD – one of…
Many notorious hacker groups (e.g. North Korea’s Lazarus) use the BYOVD attack to gain access to kernel space and implement complex advanced persistent threats (APTs). The same technique is employed by the creators of the Terminator tool and various encryptor operators. This paper discusses BYOVD operating…
CONTINUE READING 🡒 Packages intentionally destroying data discovered in NPM
Socket experts discovered in npm (node package manager) eight malicious packages that were downloaded from the repository more than 6,200 times over the last two years. All these packages could destroy data on users’ workstations.
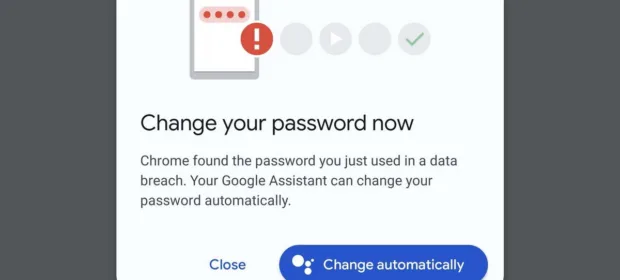
CONTINUE READING 🡒 Chrome will change compromised user passwords automatically
Google developers announced a new feature in the Chrome browser enabling its built-in password manager to change compromised credentials automatically.
CONTINUE READING 🡒