warning
All information is provided for informational purposes only. Neither the editorial staff nor the author call for the use of the knowledge gained for practical purposes and shall be liable for any possible harm caused by the materials of this article.
Search engines
Tor Browser meets us with the built-in DuckDuckGo search engine. Privacy-wise, it’s a great choice, but it only searches for DDGs on the open Internet, so we don’t need it in our searches.
However, the darknet of their search engines is almost more than the clarinet. Among the most popular: Ahmia, Candle and Torch. There were still good search engines called Grams and Fess, but for unknown reasons they are now unavailable. Each of them produces different results for the same queries, so it is better to bookmark all three resources.
info
In this article we will focus on what is available in .onion, so if you want to follow the links, you will need Tor Browser.
The first one I usually use is Candle, which is not the most famous search engine, but it does not advertise third-party resources and the relevance of the results is, I feel, higher than that of the same Torch. On the other hand, even irrelevant references are sometimes interesting.
Torch, as its name presages, constantly links to resources related to drug trafficking. He also completely does not understand the Cyrillic alphabet and has managed to damage his reputation by advertising the most shady websites.
The Ahmia search engine differs in that it is available both on the darknet and in the clarinet. The relevance of the search results is not very high (subjectively): like Torch, it often provides links that are not related to the search topic in any way.
However, if we decided to explore the mysterious world of the darknet, then search engines will help little – there are too few resources available for indexing. Sometimes the search engine can even lead to the wrong place by providing a link to a fake project.
Catalogs — Tor cards
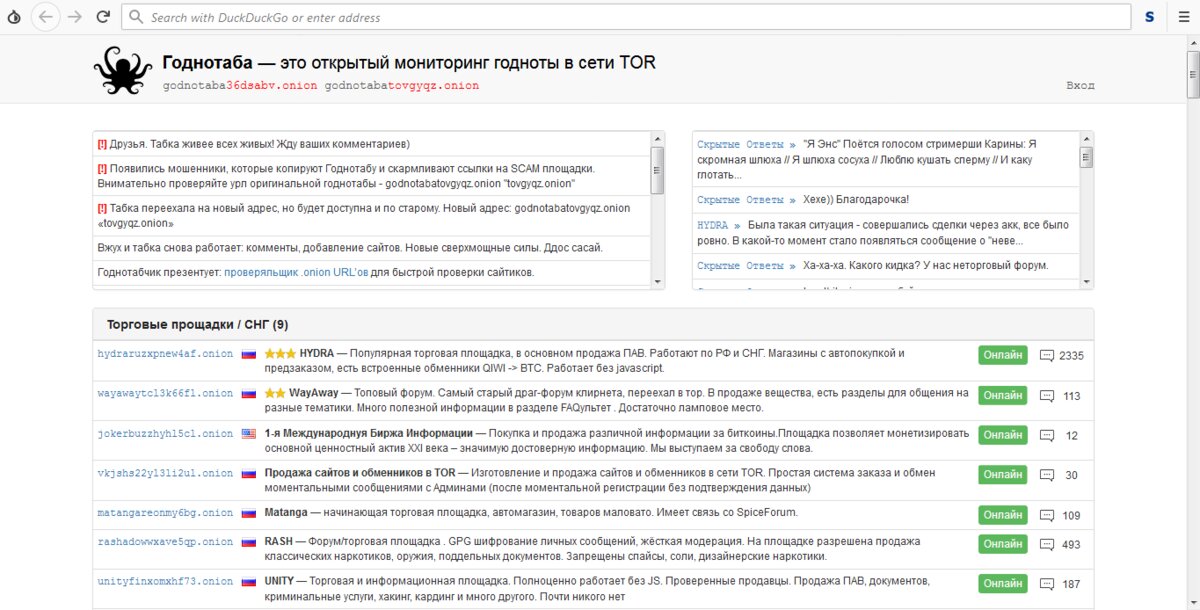
I recommend starting your search with the links catalogs. There too, of course, will be garbage and outdated links, but there is not much choice. Of the English speakers, The Hidden Wiki is the most well-known resource; in Russian, «Godnotaba». In addition, there are several dozen other reference collections — see, for example, OnionDir and Oneirun.
warning
Beware of fakes! Popular collections of links are often forged, replacing resource addresses. Godnotabah also has counterfeits, so pay attention.
Darknet Educational
Rampant piracy and cheap book readers have made buying books unnecessary for many. But copyright holders are unlikely to accept this. Therefore, there are fewer links to download books in the clientet. It’s not the same thing on the Dark Internet: you can choose «Flibusta» or «Verbal Wealthier». There’s so much to choose from, it feels like everything’s there.
Darknet – friend of torrents
Back in the early to mid-zero torrents, no one thought to ban them. People rocked books, movies, games, TV shows and even textbooks and sometimes they didn’t even think they were breaking the law. This situation is gradually changing, but the darknet is becoming a new haven for piracy.
Torrent trackers and search engines like RuTor and The Pirate Bay must have onion links that allow users to ignore bans and restrictions.
Online stores that do not accept cards
Let’s move on to illegal stores, for which the onion chain is famous. What’s typical, most of them are related to the drug trade, but you can’t get the words out of the song, you’ll have to walk through them. Buying drugs online is now routine: every old lady in the yard already knows what kind of treasures suspicious young people are looking for.
warning
The production, sale, and shipment of narcotic and psychotropic substances shall be prosecuted (Articles 228– of the Criminal Code of the Russian Federation). The author and the editorial team are not responsible for the materials published through the links. By following them, you act at your own risk.
In case you haven’t heard of these dark cases, I’ll explain in a nutshell. The buyer first uses an exchanger to get bitcoins, then goes to the store with them and purchases the desired substances. He is given an address and a photo of a bookmark, which is to be found.
Dictionary of Terms
- A warehouse is a person who stores large amounts of drugs and sells them through master troves – bookmarks with large amounts of stuff for the trove.
- Kladmen takes the master treasure, packs the stuff into smaller treasures.
- Grover is the man who manufactures the drug. As a rule, production is arranged in garages, basements, abandoned factories and similar places.
- Operator means the person responsible for keeping the store connected to the customer. The operator’s task is to solve all the issues that have arisen, interacting with the audience. In other words, project support.
Mastodons of the drug business in Russia are Hydra and WayAway services. Of course, there are other stores, such as Matanga or Darkcon. But beginners do not start to be trusted immediately, and it is not easy to learn about them.
In the West, the most popular and largest stores are Dream Market and Free Market.
info
The mortgage system is used mainly in Russia and the CIS. In America (and the West in general), people are instead finding ways to mail or (much less often) deliver by quadcopter.
RAMP
A year and a half ago, RAMP opened a list of the largest and most influential Russian stores on the darknet. It was a forum for communication between customers and sellers. In the summer of 2017, RAMP ceased to function, which puzzled many former users. Its closure was widely discussed in other forums, and someone even tried to conduct a journalistic investigation.
As a result, someone claiming to be a former RAMP moderator opened RAMP 2.0. However, it quickly turned out to be a mess: after collecting deposits from sellers and buyers, RAMP 2.0 disappeared following its predecessor. By the way, one could reasonably have guessed that this would happen: the moderator named Existence long before the fall of RAMP lost his PGP key, and diving cameras managed to get their hands on it and later began to pose as Existence. Ironically, Existence was responsible for the safety of the platform.
Hydra
RAMP was quickly replaced by a forum called Hydra. His administration is doing everything so far to hold onto the lead. Not only does the platform maintain its Telegram channel, where it shares bookmarking techniques and global drug news with subscribers, but Hydra recently purchased YouTube ads, which caused considerable public outrage. Hydra has calmly experienced DDoS attacks and has so far remained afloat.
Everything here is almost like on the Ramp, except the interface is a little better. Hydra allows users to communicate on the forum and provides personal exchangers for buying bitcoins. Qiwi is also accepted for payment: buying drugs seems to be no different from any other transaction in this system.
The Hydra administration is closely engaged in PR and organizes promotions, sometimes questionable. For example, on Hydra, you can try your luck by playing roulette – lottery tickets are purchased from a bitcoin wallet tied to the account.
At the same time, before the fall of the Ramp, users called Hydra “salt”, because, in contrast, there is a whole trade in “spices” and “salts” on Hydra, which cause tremendous damage to human health.
By the way, Hydra also has an address in the clarinet, which, of course, has long been blocked by Roskomnadzor.
What else happens on trading platforms
Drugs are not the only thing sold on the listed sites. For example, “Hydra” offers users SIM cards and cards issued for “drops” (shell persons), modems, routers, VPN services, debit cards and many other things that drug traffickers actively use.
Also, in every shadow store there is a section with vacancies, where “headhunters” recruit “cladmen” – anonymous couriers, “warehouses”, grovers and operators. The latter job opening is less common than clerks, whose demand is huge due to a rabid turnover of staff.
Hacking forums
For many, the darknet ends at drug sites, but this is only one of the first stops on our journey through the dark side of the Internet. There are other platforms on the dark internet where a user will get a life ban for trying to hire a person into the drug business. Let’s see what are the biggest hacker and carder forums on the Russian darknet.
www
Notable among the English-speaking forums is DaMaGeLaB.IN, with its users researching and discussing hacking, coding, Malvari and other IS-related topics.
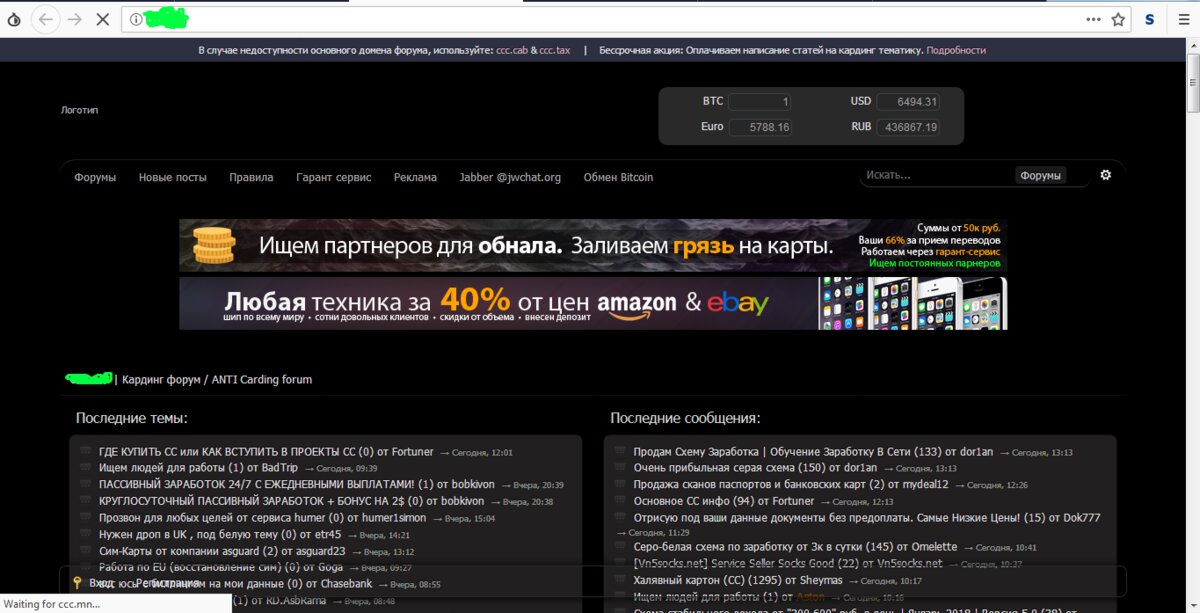
WWH-CLUB
WWH is the largest of the Russian card forums. He has an address in the clarinet, which is still available even from Russian IP.

One of the features of the platform is the provision of educational services. For a certain amount (of about a thousand dollars), forum “mentors” promise to teach any novice the art of carding, help with all questions and instruct on a “happy and rich” life.
Registration on WWH used to find a ton of useful information related to information security. Individual posts even included lectures on carding that were held on Jabber (and sometimes Skype). But open and free registration has led to the domination of trolls and “schoolchildren”, as they call inadequate or unreliable users. Therefore, since recently, the administration has closed all cream from new users. Access to private sections now costs 20 US dollars. WWH left a couple of sections open, but there’s usually no useful information there.
Verified
Among Russian carders, Verif is one of the most respected long-term residents. It, like the WWH, has become a textbook of carders and a place for communication, seeking information and the people needed for shadow work.
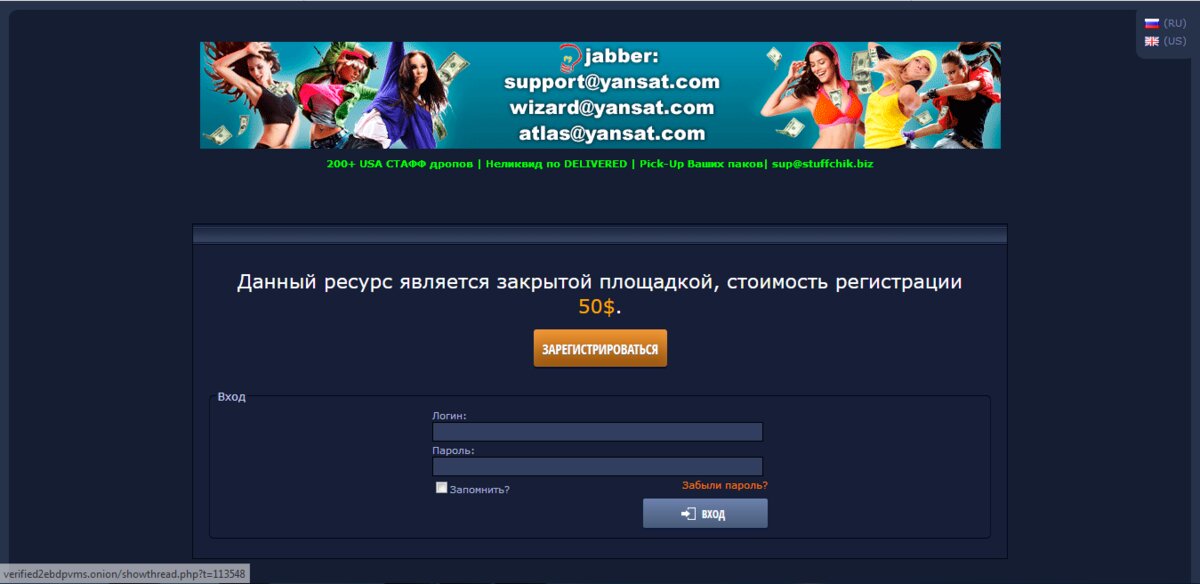
Registration on the forum costs 50 US dollars and it is impossible to register for free. But even after paying for access, it is problematic to operate on Verife, because carders are always viewed with fear. One of the old-timers must first vouch for the beginner – only then he can start doing something on the forum. That is, even if the user has acquired full access to the forum, they will not be able to conduct business without a surety or deposit.
Exploit.in
This forum is mainly devoted to hacker topics. Unlike Verif, registration on the Exploit is still free, but to access the forum, a user must provide the administration with a link to their accounts on other boards. Accounts must have a reputation and registration of one year or more, otherwise the administration will deny users access.
Exploit.in is respected in the Russian darknet, and Western colleagues sometimes look here. The core population are carders that offer their services, from creating websites to providing botnets.
The resource is available in the clarinet, it also has a Jabber server, which is respected by users at least as much as the forum itself.
CrdClub
It is one of the oldest forums dedicated to carder. Registration is free, access to all sections is provided. The forum, like Exploit, can be divided into two big parts: Russian speaking and English speaking.

Here are hundreds of articles dedicated not only to carding, but also to skam, hacking, and social engineering.
Probiv
If in posts on Exploit, WWH, and Verified the authors often say that they “do not work in the RU and CIS” (which means an unwillingness to carry out dark business in the territory of the native or nearby state), then “Punching” is popular precisely among fraudsters working in Russia and the CIS.

A distinctive feature of the forum is that it is almost entirely dedicated to “punches”, that is, for a certain amount, you can find information about a certain person on the forum: from credit history to passport data. Immediately, you can also find trading in “earnings schemes”: a person provides the administration with a document with an online (or offline) earnings manual, after checking the material, it is published in a certain forum branch and sold to users. The price range for such “earnings schemes” ranges from a couple thousand rubles to several million. It all depends on the potential profit.
Popular services and products
All of the above forums readily offer jobs to specialists. The popularity of different types of job openings varies depending on the forum’s orientation: WWH searches for skilled carders, “Exploit” needs coders, and “Punching” mainly searches for LLC drops and microloans.
And of course, trade is thriving everywhere: you can buy someone else’s credit card details on WWH, a botnet or website on Exploit, and Punch will provide passport data, hacked accounts, and more for shadow activities.
Association
Some platforms have still not decided on the main direction and offer only a little. Others are intended for anonymous communication only. Let’s go to some popular places.
Runion
Runion is a unique place where everything on the Russian darknet is represented. Here they offer to buy weapons and drugs, talk about political topics and learn about the work of special services. The Runion administration recently launched a drug-trafficking platform called Solaris (although it is completely deserted).
If you dig into the forum topics, you can learn how to dispose of a corpse, smuggle prohibited substances across the border or even change your identity – Runion will provide the right information and the right people. However, we do not advise anyone to try using these services. This is extremely dangerous not only because of problems with the law, but also because anyone can hide behind the mask of an anonymous person.
Also on the forum you can buy interesting manuals on network security. However, such things are also found in other forums. Arms trafficking is also not uncommon on the dark internet. Not much has changed since [our last study], however(https://xakep.ru/2016/10/05/darknet-services).
Before Runion, there was another similar forum, and even the name was similar – RuOnion. However, it closed and no one knows the reasons.
Chat with stranger
Interacting with a stranger in the age of Tinder, Badoo and other specialized services is no longer something supernatural. However, Chat with stranger has an important difference – neither the interlocutor nor the service owners know anything about you. Usually there are only 40–50 people online, but you can easily wait for someone to appear. Alas, these are not always adequate individuals who are eager to communicate on the proposed topics, but this too can have its charm.
“NS-Forum”
This is a forum dedicated to the topic of National Socialism. It shows like-minded people sharing books, ideas and stories of their lives. If Runion is part forum, part trading platform, then this is exclusively communication. Some sections literally make your hair stand on end, so if you are against any violence, you better bypass this forum.
There is, however, a useful part on information security. For example, how to install Tails, which VPN to choose, how to encrypt a flash drive, and so on. But if Runion and Exploit are concerned about these things in connection with illegal activities and fraudulent schemes, then NS-Forum provides them for ideological reasons. In addition, some members of the movement are in trouble with the law and try to conceal their activities.
Other places to communicate
The list of chats and forums does not end there – there is even a Facebook mirror in .onion, but it can hardly save you from punishment for reposting. There is also, for example, Tor4 forum where users share their trip reports (that is, descriptions of how they feel about taking drugs) and discuss the effects of a substance on the body.
There are also much more frightening forums on the darknet: pedophiles, sadists, terrorists, but for obvious reasons the Hacker will not publish links to their websites. If you really want to find something like this, open the catalogs using the links at the top of this article and search. But try not to stay there too long and protect your mental health! Besides, we still have to go through the economic part of the darknet.
Dark Internet money: wallet or onion!
The darknet usually comes either for completely anonymous communication or (much more often) to do dark things. That’s why there’s a proliferation of money changers, cash services, and drop services. But before you do anything with money, you have to put it somewhere.
Back in 2016, forums were wondering – is bitcoin anonymous? And can it be used for dirty business? Unfortunately for shadow businesses, the cryptocurrency turned out to be anonymous. Increasingly, the police are seen in the news detaining another coder or hacker who kept his money in bitcoins. But any problem is first and foremost a challenge, and on the dark internet they love them.
For example, Rahakott functions like a regular bitcoin wallet, but already has a mixer built in. How does it work? A person sends him a certain amount (suppose two bitcoins), he sends money to other wallets in small installments, and then collects money on another wallet located on Rahakott. It turns out that it is almost impossible to trace the transaction, because the amounts come in small installments from hundreds of different addresses.

Such mixers are considered much more reliable than just wallets, and their services are popular. But not all of them work as promised by the owners, and some do not transfer money at all, keeping it. There are, by the way, just mixers without built-in wallets, like MixerMoney or Blender.
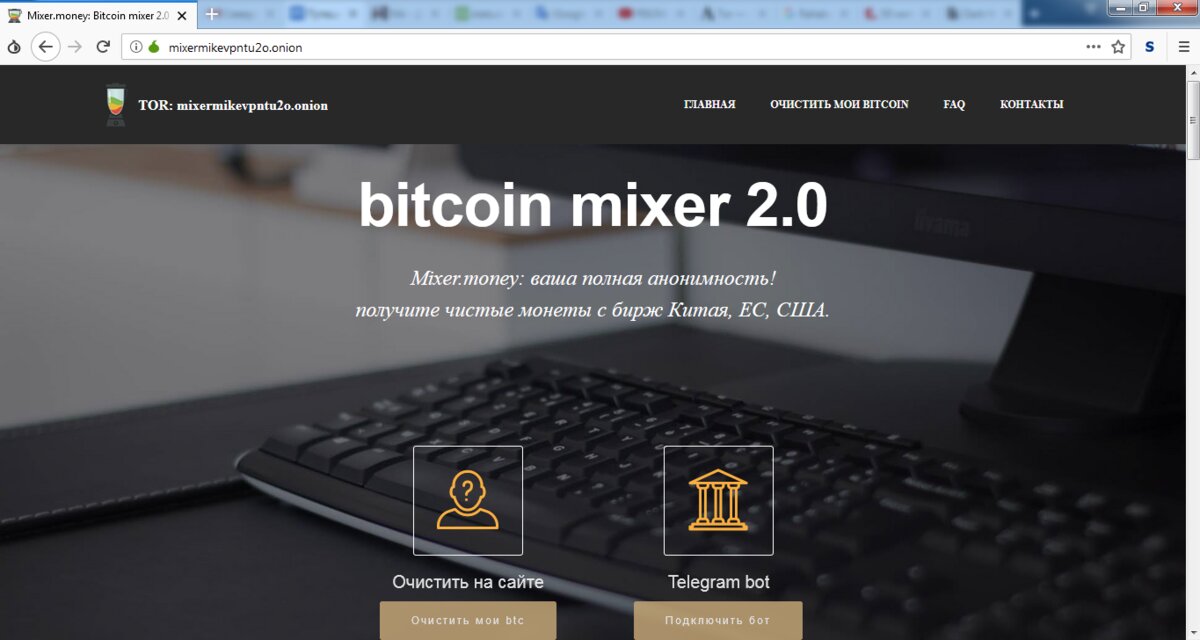
The link between bitcoins and cash (or electronic) money is exchangers. Darknet, like the clarinet, has a huge number of them. WWH or Exploit has a lot of advertising links. As a rule, the same sites provide cash out services, meaning a person just sends their bitcoins, and receives cash through couriers or a bookmark. Examples of such exchangers are Konvert and 24xbtc.
If you intend to use such services, remember that you act at your own risk: in many forums, you often find comments about the fact that one or another exchanger “sucked up” (that is, started cheating customers and taking money for himself). In general, he goes dark and skem – the concepts are inseparable.
Onion bench
After money and success, popularity usually brings different problems. But if popular actors are only imitated, then popular websites on the darknet are simply forged in order to profit from ignorance of users.
For example, if you type the word Hydra into the Candle search engine, there are fakes at the top of the search results. It’s like a real Hydra, but instead of a bookmark address, the user will get an empty address (where they won’t find anything) or just a ban.
Within the forum itself, guarantors are insured against this: they act as intermediaries in the transaction and transfer money to the seller only when the buyer confirms receipt. But if the forum is fake, then the guarantor will be fake.
Such forums, as a rule, are very easy – links to them get caught in the search engines output both on the darknet and on the clerknet. If you see a terrific deal like a new iPhone for half price, earn a million schemes worth several thousand rubles, “bays” (that is, transferring money from a stolen card) and other tempting offers, then it is most likely to the bench.
The guarantor at fraud sites is usually one person who, after receiving the right amount, will simply ban the victim without giving any reason. Although sometimes the administration can come up with something to make it look more organic.
There are many exchangers on the darknet that act on a similar principle: they just take cryptocurrency and don’t give it away. The surest way not to get caught by the fraudster is not to use links from unverified sources (only from verified directories) and always check the resource address, because at first glance you can not distinguish it.
End of the adventure
Every year websites appear, move and disappear en masse on the darknet. Yes, most of them are devoted to selling forbidden or skam, but there are places that allow you to communicate on exciting topics or read stories from the lives of strangers. In general, it is a cold and uncomfortable place, but also extremely interesting. What exactly will get your attention depends on you.
