warning
In many smartphones, an unlocked bootloader will not allow you to perform an over-the-air update.
In 90% of cases, unlocking the bootloader will entail deleting all data from the smartphone, including the memory card.
Busting myths
Lets talk about what it means to “turn a smartphone into a brick” and what other pitfalls may await the user on the way to changing the system and installing custom firmware. What glitches can be caught in this case and is it possible to kill a smartphone by reflashing it incorrectly? Will you lose the warranty forever or can the smartphone be returned to its previous state? Can custom firmware really let the owner of the smartphone down at the most inopportune moment and are they worth it?
Myth 1. Improper flashing can kill a smartphone
A fall from the fifth floor can kill a smartphone, but not reflashing. The main problem faced by anyone who wants to flash a smartphone is that during the installation of the firmware, a failure can occur, which will cause it to not work, and the smartphone will actually turn into a brick.
All this is true, but only on paper. To understand why, it is enough to understand how the smartphone flashing process works and what system components are used. To be able to install third-party firmware on a smartphone, you need to unlock the bootloader (not in all cases), get root and install a custom recovery console (ClockworkMod or TWRP) capable of installing firmware with any digital signature.
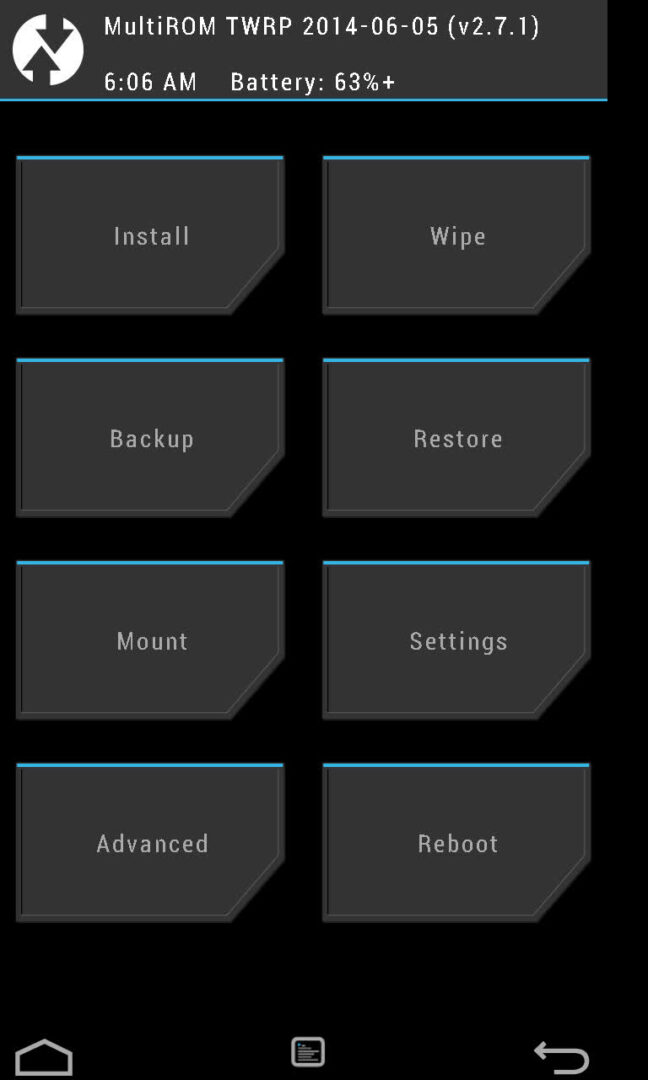
The recovery console is stored in a separate partition of internal NAND memory and is not related to the installed operating system in any way. After installing the modified version of the console, it will be possible to flash custom firmware or even another OS (Firefox OS, for example). If the firmware fails during the firmware installation, the smartphone will not be able to boot it, but the recovery console will remain in place, and all you need to do is boot back into recovery and reinstall the firmware.
In addition, any custom recovery console contains a backup/restore function that allows you to make a backup copy of the main firmware and restore it unchanged (with all applications, settings and data) in case something goes wrong. In fact, the smartphone can be returned to its original state.
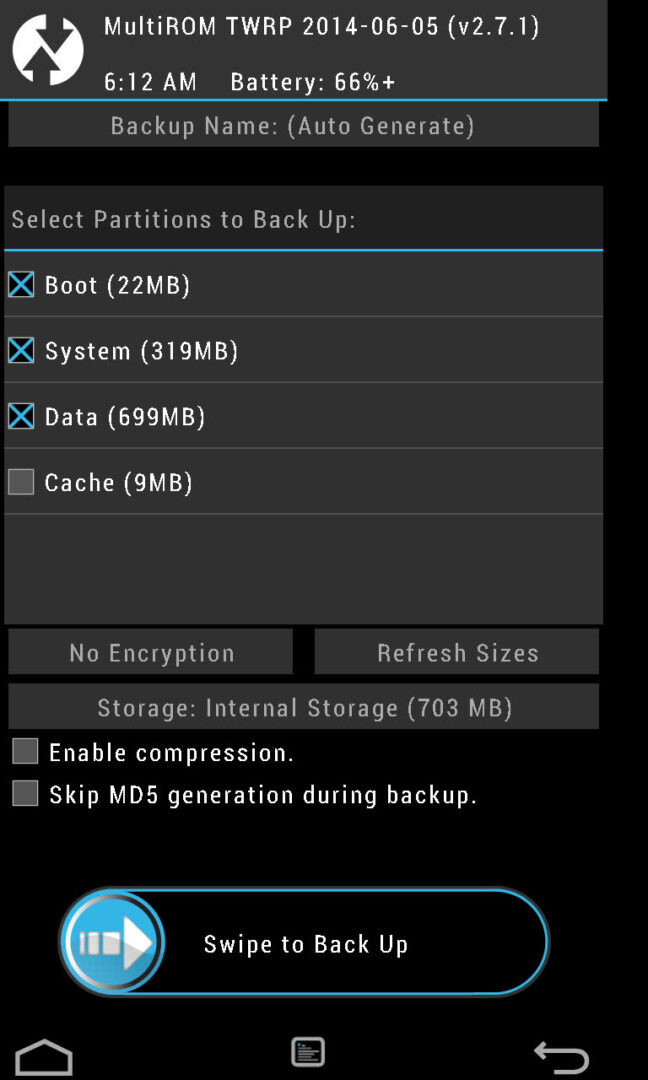
You may ask: what happens if there is a failure during the installation of the Recovery Console itself? Nothing, in this case it will be the opposite situation, when the operating system itself will remain in place, and the console will be lost. To deal with it, you just need to reflash recovery directly from Android.
Hypothetically, you can imagine a situation where both the firmware and the recovery console will be killed (although this is quite difficult to do), but even in this case, the primary bootloader will always remain in place, flashed into the permanent memory of the smartphone. To restore the firmware with it, just connect your smartphone to a PC and flash it using fastboot or a specialized tool from the device manufacturer (Odin, for example).
Conclusion: it is impossible to kill a smartphone by installing third-party firmware. Either recovery or the primary bootloader will always remain in place.
Myth 2. Custom firmware is unreliable
Firmware is different. On the vastness of the World Wide Web, you can find a huge number of Android builds for every taste and color, and most of them are really slag that can lead to instability in the operation of the smartphone and loss of some functionality. Therefore, the first thing to remember is that you should only deal with serious custom firmware developed by large teams of experienced developers. First of all, these are CyanogenMod, Paranoid Android, AOKP, OmniROM and MIUI.
Second. There are two types of firmware: officially supported and ported by third-party developers. CyanogenMod, for example, has an official version for the Nexus 4 smartphone, but does not have one for the Motorola Defy. But for Defy there is an unofficial port of CyanogenMod 11 from a developer with the nickname Quarx. Their difference is that the CyanogenMod team is responsible for the support and proper operation of the former, while the Quarx team is personally responsible for the support and proper operation of the latter. Official versions of the firmware are usually fully operational, but the correctness of the latter depends on a third-party developer.
And the third. There are stable and development versions of the firmware. Stable versions of CyanogenMod have an index of M (CyanogenMod 11.0 M7, for example). This version of the firmware usually does not contain bugs. Developed versions (in the case of CyanogenMod, these are daily nightly builds) may contain bugs and are therefore not recommended for everyday use.
Conclusion: if you install a stable official version of the “normal” firmware on your smartphone, the risk of encountering bugs is minimal. Everything else is for experimenters.
Myth 3. A rooted smartphone can crash
Rooting software does four simple things: it runs an exploit that allows it to root the system, mounts the /system partition in write mode, copies the su binary required to root it in the future to the /system/xbin directory, and installs the SuperSU or SuperUser application, which will take control every time an application requests root rights with su.
info
On Linux, ADB and Fastboot can be installed separately from the Android SDK. В Ubuntu: sudo apt-get install android-tools-fastboot. In Fedora: sudo yum install android-tools.
To prevent the Knox system from interfering with root applications, it can be disabled using the following command from the terminal: su pm disable com.sec.knox.seandroid.
None of these steps can crash or kill the smartphone. The only thing that can happen is that the exploit will cause a segmentation error and the smartphone will reboot, after which it will continue to work normally.
Myth 4. Software that requires root rights can brick a smartphone
In theory, an application with root rights can do anything with the firmware of a smartphone, including erasing it completely. Therefore, you need to be extremely careful with such software. The software that we talk about on the pages of the magazine is completely safe and tested on its own skin. In addition, for all the time I have been using Android smartphones (and this is since version 1.5), I Not once I have not encountered a situation where software with root support would kill a smartphone.
Software distributed through Google Play usually fully complies with the declared characteristics, and if it led to a brick or left a backdoor in the bowels of the smartphone, it would not last even a week in the store. In any case, you need to follow the “trust but verify” rule and carefully read the instructions for using root applications.
Myth 5. Root privileges make the smartphone vulnerable to viruses
It is not root privileges that make a smartphone vulnerable to viruses, but bugs used to obtain them. Rooting tools and viruses can exploit the same Android vulnerabilities to gain root privileges, so the mere fact that a device is rooted does not change anything. A well-written virus will not ask for rights in the standard way, giving away its presence, instead it will use the same vulnerability to obtain them covertly.
Moreover, having root, you get the opportunity to install a fresh version of Android (in the form of a custom firmware), in which these bugs have already been fixed. Also, do not forget that most custom firmware allows you to disable root or create whitelists of applications that can use these rights.
Myth 6. If I get root and install custom firmware, I will lose my warranty
The guarantee is lost not from the very fact of obtaining root, but because of its detection by the service center. Most devices can be rooted using the Universal Unroot app or by reinstalling the stock firmware using the manufacturers official app.
There are, however, two exceptions to this rule. The first is the Knox system, pre-installed on new Samsung smartphones and tablets such as the Galaxy S4, S5, Note 3 and Note 10.1. Knox provides an increased level of security for Android by responding to any firmware modifications and the installation of third-party kernels and firmware. In the event that the user performs these actions, the system sets a trigger that confirms the fact of modification. The trigger is implemented in hardware (eFuse chip), so you will not be able to reset it to its initial position. On the other hand, it is not entirely clear whether the service center will refuse to repair the device on this basis. Secondly, the eFuse chip is also installed on some other devices (such as LG smartphones), and it also allows you to accurately determine whether the smartphone has been rooted or reflashed.
If we talk about custom firmware, everything is more complicated here. Usually, the flashing operation requires unlocking the bootloader, and this can be done either with the help of special exploits or with the help of the smartphone manufacturers web service. In any case, the unlocked bootloader will definitely indicate that the smartphone did not belong to a blonde.
On some smartphones, it is possible to lock the bootloader back, but you should find out about this separately, and also keep in mind that the newly locked bootloader is likely to receive the Re-locked status, and not Locked, as it was originally (this happens on HTC smartphones, for example). The only exceptions here are smartphones and tablets of the Nexus line, the bootloader of which can be blocked and unlocked in three clicks without any dancing with a tambourine, and no one will find fault with anything.
Conclusions
Rooting and flashing a smartphone are absolutely safe operations that cannot brick a smartphone for purely technical reasons. The only exception is an attempt to hack the bootloader in order to unlock it. In this case, the eFuse chip (if the smartphone has one) may work and block the ability to turn on the smartphone.
Fortunately, today smartphone manufacturers either prefer not to block the ability to turn on a smartphone with a hacked bootloader (setting a trigger indicating the fact of such an action, as Knox does), or implement a special web service that allows you to painlessly unlock the bootloader with the loss of the smartphone warranty, which saves users from the need to take risks by breaking the bootloader.
Problems that may arise during flashing
So, now lets talk about what problems can arise when getting root and flashing and how to deal with them.
Scenario one: after an unsuccessful flashing, the smartphone stopped booting
Unsuccessful flashing can be caused by several factors: the battery is dead, and the firmware is only half full, the firmware turned out to be faulty or intended for a different smartphone model. In the end, there was simply not enough space on the smartphone, which can happen when trying to install a fresh version of Android on a three- or four-year-old smartphone.
Outwardly, all these problems usually manifest themselves either in endless resets of the smartphone to the initial logo of the manufacturer, or in the so-called boot loop, when the boot animation spins on the screen for more than five to ten minutes. There may also be problems with the screen (multi-colored ripples) and a non-working touch screen, which also prevent the use of the smartphone.
In all these cases, it is enough to do one simple thing: turn off the smartphone by long pressing the power button, then turn it on with the volume down button held down (some smartphones use a different combination), and after you get to recovery, reinstall the firmware (Install zip from sdcard → Chooze zip from sdcard) or restore the backup (Backup and restore → Restore). Everything is easy and simple.
Scenario Two: Firmware Works, but Recovery Is Not Available
This can happen after a failed installation or update of the Recovery Console. The problem manifests itself in the fact that after restarting the smartphone and turning it on with the volume down button pressed, a black screen appears, after which the smartphone either resets or hangs.
Solving this problem is not easy, but very simple. You can install the recovery console on the vast majority of smartphones using the TWRP Manager, ROM Manager or ROM Installer applications. They themselves determine the model of the smartphone, download and flash the necessary recovery, without requiring a reboot. If you can not restore the console with their help, just find instructions on the Internet for installing recovery on your device.
Scenario three: neither firmware nor recovery is available
To be honest, it is difficult for me to imagine such a scenario, but, as practice confirms, it is quite realistic. There are two ways to get out of this situation: use fastboot to upload recovery to your smartphone or use a tool from the manufacturer to install stock firmware. The second method will be discussed in more detail in the next section, and I will talk about fastboot here.
Fastboot is a tool that works directly with the primary bootloader of the device and allows you to upload firmware, recovery and unlock the bootloader to the smartphone (in devices of the Nexus line). Many smartphones and tablets have fastboot support, but some manufacturers block the ability to use it. So you will have to consult the Internet about its availability.
To access fastboot, you will need Drivers and the Android SDK. When they are installed, open the command line, go to the SDK installation directory, then to the platform-tools directory, turn off the smartphone, turn it on with the volume buttons held down (both) and connect it with a USB cable to the PC. Next, you need to find the recovery image in .img format for your device and run the command:
$ fastboot flash recovery image.imgOr even force the smartphone to download recovery without actually installing it:
$ fastboot boot image.imgIn the same way, you can sew Official Firmware Update:
$ fastboot update update filezipYou can find the right recovery for your device either on TWRP website, or in the XDA-Developers and 4PDA forums.
Returning the smartphone to its original state
In this section, I will talk about ways to get your smartphone back to clean drain, no matter what condition it is in. These instructions can be used both to build a smartphone and to remove traces of rooting and flashing. Unfortunately, I can not talk about all the possible models, so I will focus on four of the most popular flagships: The Nexus 5 (which I call the benchmark), the Galaxy S5, the LG G2, and the Sony Xperia Z2.
Nexus 5 and other Google phones
Returning Nexus devices to their original state is easier than any other smartphone or tablet. In fact, it is so simple that there is nothing to talk about. In fact, all you need to do is install the ADB/fastboot drivers (you do not even need them on Linux), download the firmware archive and run the script. Step by step, the whole operation looks like this:
- Download and install ADB Driver Installer hence.
- Download and install the Android SDK.
- Download the archive with the firmware for the desired device from of the Google website.
- Turn off the device, turn it on with the volume buttons (both) held down and connect with a USB cable.
- Unpack the archive with the firmware and run the script flash-all.bat (Windows) or flash-all.sh (Linux) and wait for the operation to finish.
- Run the command prompt, go to the directory with the Android SDK, then platfrom-tools and execute the fastboot oem lock command to lock the bootloader.
For those who are curious about what a script does, here is a list of commands:
fastboot flash bootloader bootloader-DEVICE-NAME-VERSION.imgfastboot reboot-bootloaderfastboot flash radio radio-DEVICE-NAME-VERSION.imgfastboot reboot-bootloaderfastboot flash system system.imgfastboot reboot-bootloaderfastboot flash userdata userdata.imgfastboot flash recovery recovery.imgfastboot flash boot boot.imgfastboot erase cachefastboot flash cache cache.imgGalaxy S5
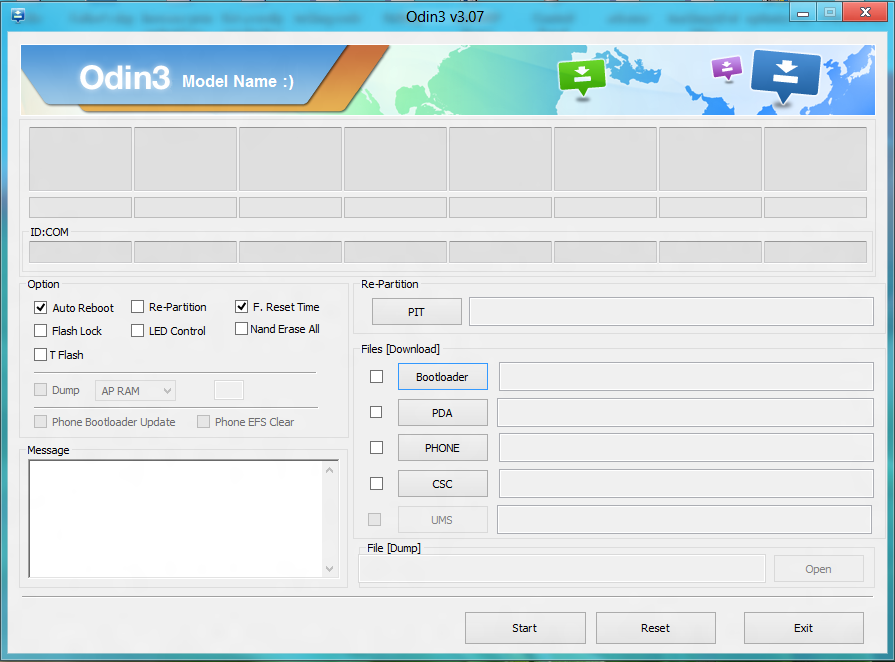
With the Galaxy S5 smartphone, things are a bit more complicated, but overall quite simple. This time, you will need the Samsung Odin application, with the help of which the smartphone will be flashed. Steps:
- Reset the smartphone to factory settings.
- Download and install the latest version of Samsung USB drivers hence.
- Download and install the latest version of Odin hence.
- Go to the samfirmware.com website, enter the SM-G900F model in the search, find the firmware marked Russia, download and unpack.
- Turn off the smartphone and turn it on with the volume down and “Home” buttons pressed, wait five seconds until a warning message appears.
- Press the volume up button to put your smartphone in Odin mode.
- Connect the smartphone using a USB cable.
- Start Odin, press the PDA button and select the file with the tar.md5 extension inside the directory with the unpacked firmware.
- Press the Start button in Odin and wait for the flashing process to finish.
As I said before, this operation will return the smartphone to its original state, but it will not reset the trigger installed by the Knox system (if it was in the standard firmware). Therefore, the service center may refuse to repair.

LG G2
Restoring the LG G2 to factory condition will also not cause much trouble. The number of steps in this process is somewhat larger, but they do not require special training and knowledge in themselves. So, what to do to get the G2 back to the factory firmware:
- Download and install ADB Driver Installer hence.
- Download the official firmware (Europe Open 32G or Europe Open) hence.
- Download and install LG Mobile Support Tool, as well as FlashTool (goo.gl/NE26IQ).
- Turn off your smartphone, press the volume up button and insert the USB cable.
- Expand the FlashTool archive and run the UpTestEX.exe file.
- In the window that opens, select Select Type → 3GQCT, Phone Mode → DIAG, select the firmware downloaded in the second step in the Select KDZ file option.
- Click the CSE Flash button at the bottom of the screen.
- In the window that opens, click Start.
- In the next window, select the country and language and click Ok.
- Wait for the firmware to finish, and then turn the smartphone off and on.
That is all. But keep in mind that, just like with Samsung, the smartphone will still have Rooted status, and there is no fixing it.
Sony Xperia Z2
Now lets talk about how to return the Sony Xperia Z2 smartphone to its factory state. As in the previous two cases, you will need stock firmware and an official flashing utility. You run the utility on your PC, connect your smartphone with a USB cable, and start the update process. Step by step, it all looks like this:
- Download and install ADB Driver Installer hence.
- Reset the smartphone to factory settings.
- Download and install the Flash Tool with official website Sony and the latest firmware hence.
- Copy the firmware file to the C:/Flashtool/Firmwares directory.
- Turn off the smartphone and turn it on with the volume down and “Home” keys pressed.
- Connect the smartphone to the PC using a USB cable and launch the Flash Tool.
- Click the lightning button in the Flash Tool. In the window that opens, select Flashmode, double-click on the firmware in the list that opens.
Conclusions
Flashing a smartphone, and even more so obtaining root access, are not at all such scary and dangerous operations as they may seem at first glance. If you do everything right and do not resort to tools that unlock the smartphone bootloader bypassing the manufacturers tools, you will not be able to brick the smartphone. Yes, in some cases you will have to tinker to return everything to its place, but what is better – to use a locked smartphone, which does not allow you to do even half of the things that it is capable of, or to get full control over the device? After all, reinstalling Windows on a PC does not scare anyone.
