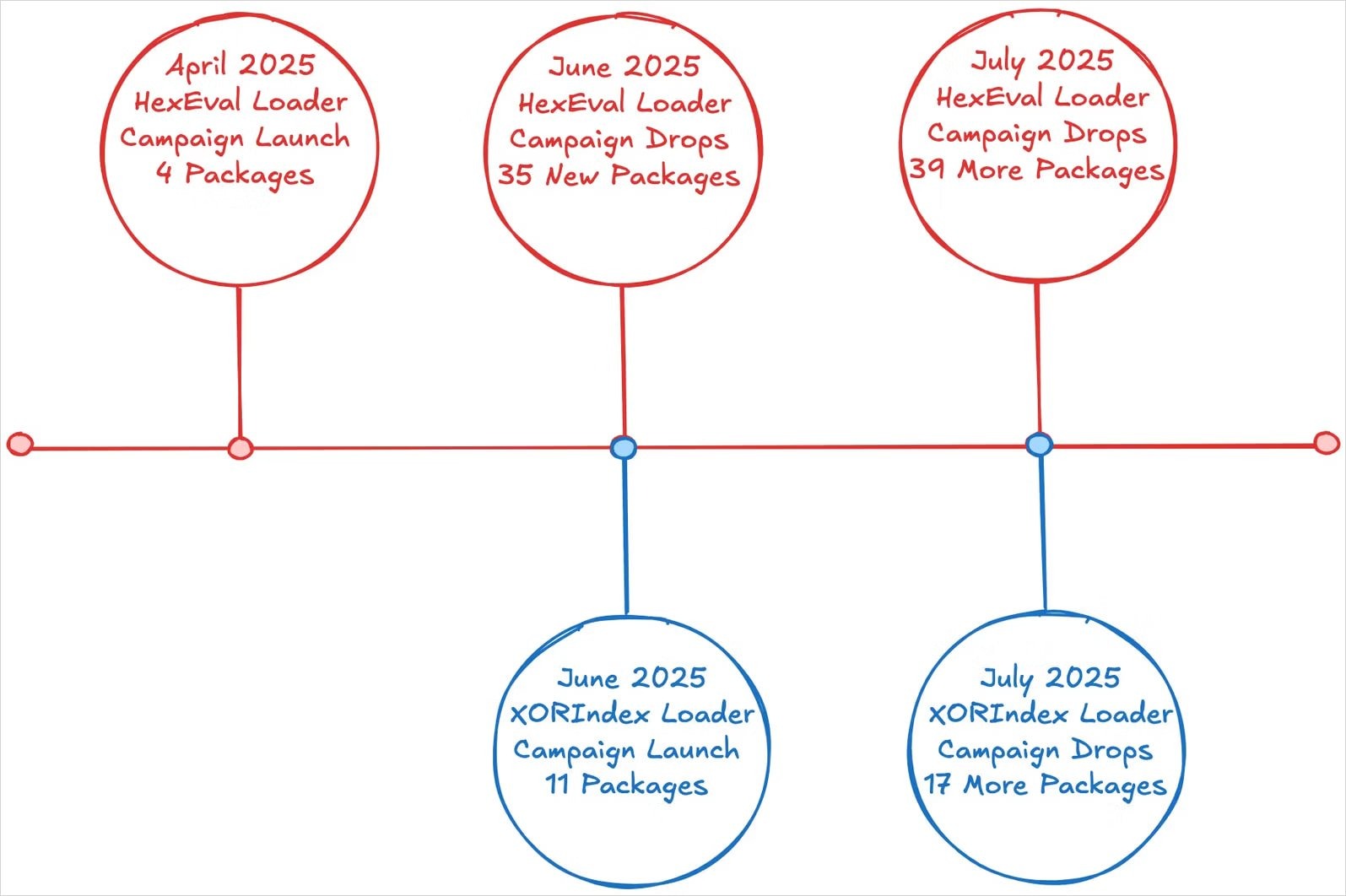
North Korean hackers have deployed 67 malicious packages on npm, through which a new malware loader called XORIndex was distributed. In total, the packages accounted for over 17,000 downloads.
Experts at Socket, who discovered these packages, suggest that the activity is part of an ongoing malicious campaign called Contagious Interview, targeting developers.
It is also noted that this campaign is a continuation of malicious activity that has been ongoing since April of this year. Last month, the same threat actors introduced 35 packages into npm, which infected developers’ devices with infostealers and backdoors.
The mentioned Contagious Interview campaign has been active since at least December 2022, and the main targets of the attackers are software developers. The hackers make fake job offers, which ultimately result in infecting their systems with malware. The hackers’ goals may vary: from collecting confidential information that allows them to hack companies, to stealing cryptocurrency assets.
Some of the 67 packages uploaded to npm mimicked the names of legitimate projects and libraries, such as:
- vite-meta-plugin;
- vite-postcss-tools;
- vite-logging-tool;
- vite-proc-log;
- pretty-chalk;
- postcss-preloader;
- js-prettier;
- flowframe;
- figwrap;
- midd-js and middy-js.
After installing any of these packages on the victim’s machine, a postinstall script was executed, launching XORIndex — a new tool which appears to be used by attackers in conjunction with the malware loader known as HexEval Loader.
XORIndex collects host data to profile the victim, and then transmits the data to a hardcoded command-and-control server address hosted within Vercel’s infrastructure, a company specializing in cloud application development.
In response, the attackers’ server provides one or more JavaScript payloads, which are executed on the victim’s system using eval(). These payloads are typically the BeaverTail and InvisibleFerret backdoors, which are associated with North Korean hackers and the Contagious Interview campaign.
Ultimately, the malware provides its operators with access to compromised machines, facilitates data exfiltration, and can be used to deliver additional payloads.
According to researchers, North Korean hackers employ both old and new tools with subtle modifications to evade detection, and each time npm removes the malware, they return using new accounts and package names.
“Defenders should expect new iterations of these loaders to appear in fresh packages, often with minor modifications that allow them to evade detection,” researchers warn.
