warning
Collecting personal information without consent violates the law. All information in this article is provided for informational purposes only. The author and the editorial team do not bear any responsibility for any consequences resulting from the use of the information presented in this publication.
Zehef
The Zehef utility is a Python-based tool designed for gathering information about an email address. It checks the address’s reputation across various sources and identifies potentially linked social media accounts. This tool is incredibly useful for verifying whether the email has appeared anywhere and, with a bit of luck, obtaining usernames for social media and other service accounts.
info
We will be installing all the tools on Kali Linux. However, the installation process is unlikely to be significantly different on other distributions.
To install Zehef, simply clone the repository and install the dependencies.
git clone https://github.com/N0rz3/Zehef.git
cd Zehef
pip install -r requirements.txt
Launching:
python3 zehef.py <email>
The output layout seems like an attempt was made to make it visually appealing, but it ended up lacking information. You have to sift through the entire output to gather all the interesting details, and there’s quite a lot of intriguing content.
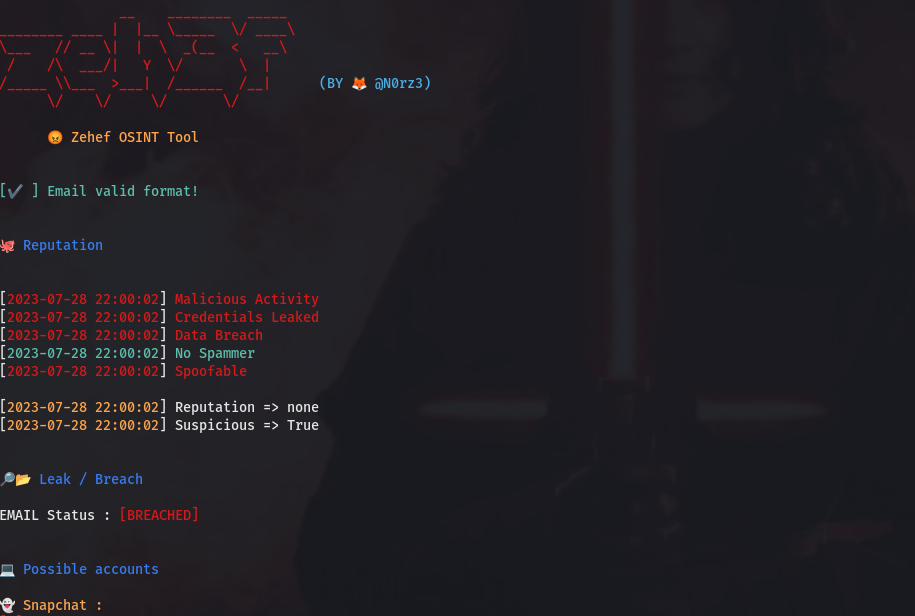
We see that our test email address is associated with several accounts, and it’s also registered on Twitter/X, GitHub, and a few adult websites.
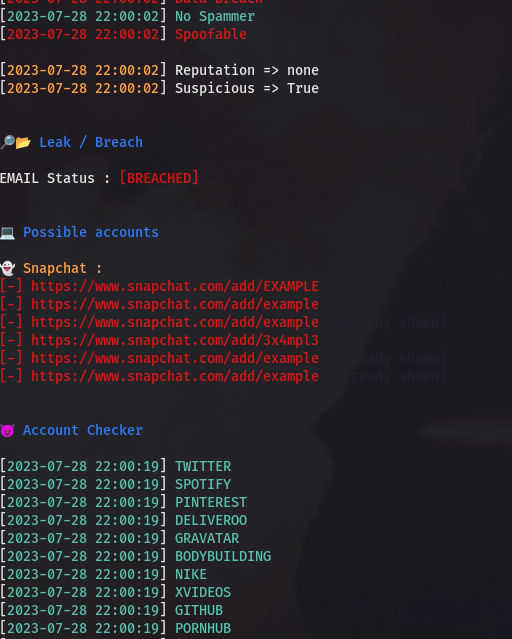
Like any somewhat complex program, Zehef can sometimes throw errors. If you encounter an error like the one in the screenshot below, simply remove the TikTok search code, and everything should work properly.
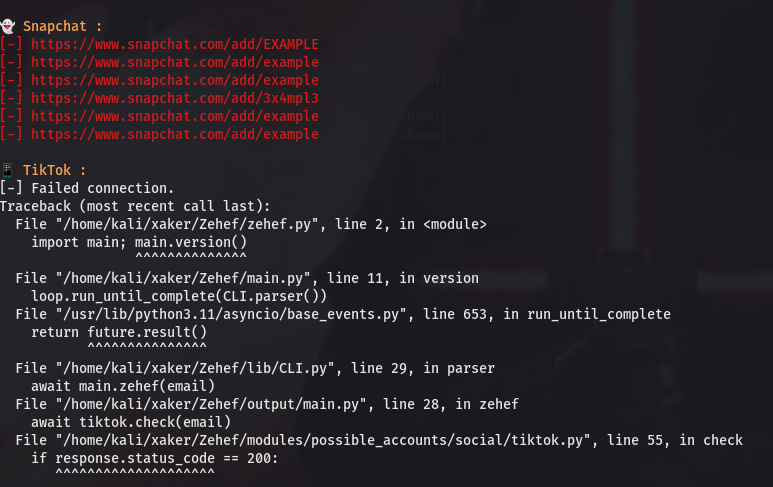
You need to delete this file:
Zehef/modules/possible_accounts/social/tiktok.py
Also, delete the highlighted sections of code shown in the screenshots below from Zehef/.
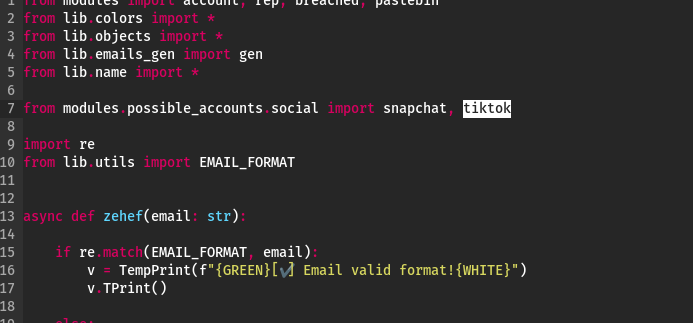
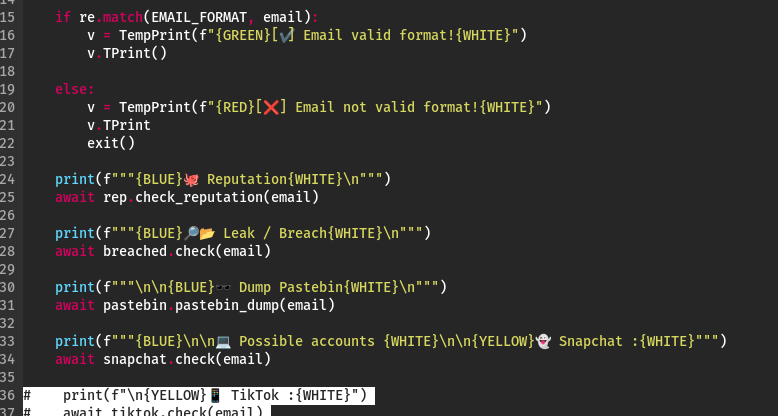
An alternative option is to simply comment out the buggy sections, which is what I did.
NetSoc_OSINT
This script is written in Bash and is designed to extract as much information about a user as possible from various social networks without requiring any authentication. Here’s how it works: you select one of the available networks and operate strictly within the limits of what’s publicly accessible for that platform. The result is highly precise data extraction! What I appreciate most is that the script doesn’t require obtaining API tokens from third-party accounts or inputting them into configuration files.
The following services are supported:
- Instagram;
- TikTok;
- Twitter/X;
- Twitch;
- Telegram;
- GitHub.
Everyone can work with both public and private accounts.
The setup is straightforward. The script is just a single file with no dependencies (except that you’ll need Bash). Download the repository, make it executable, and you’re good to go.
git clone https://github.com/XDeadHackerX/NetSoc_OSINT
cd NetSoc_OSINT
chmod 777 netsoc_osint.sh
bash netsoc_osint.sh
You can set the language first, and then you’ll be directed to the tool’s main menu. From there, you can choose the social network you’re interested in.
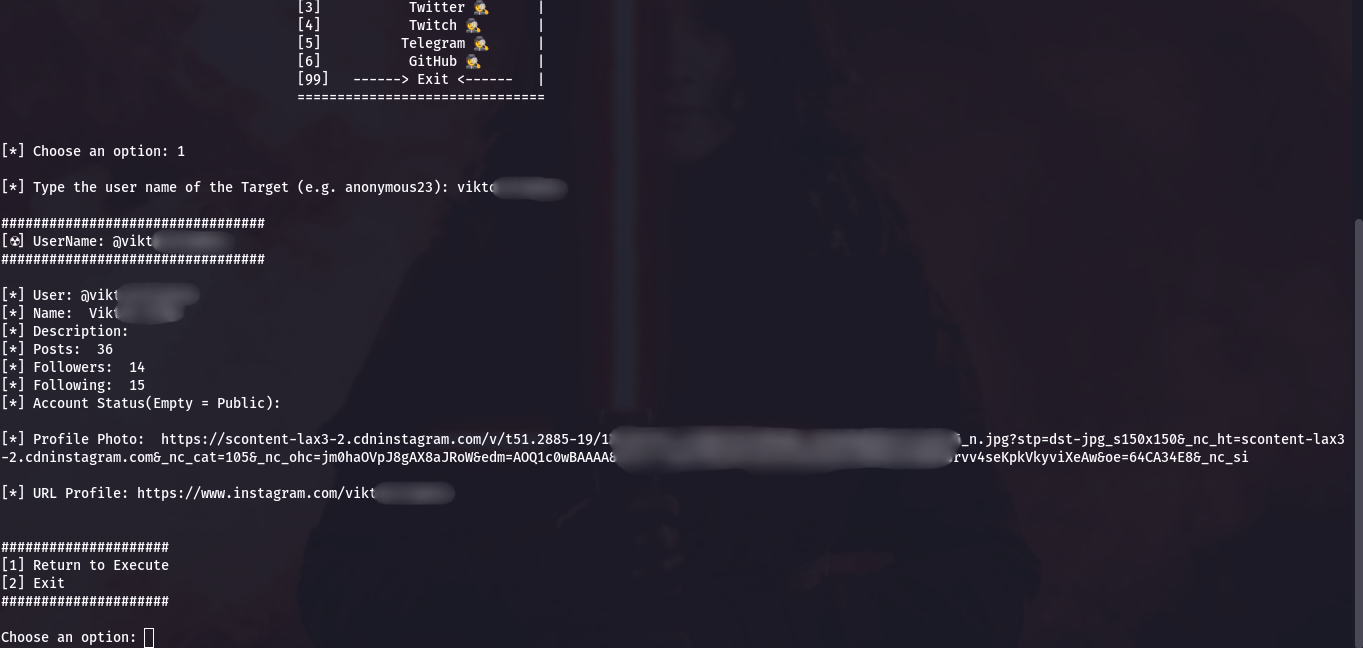
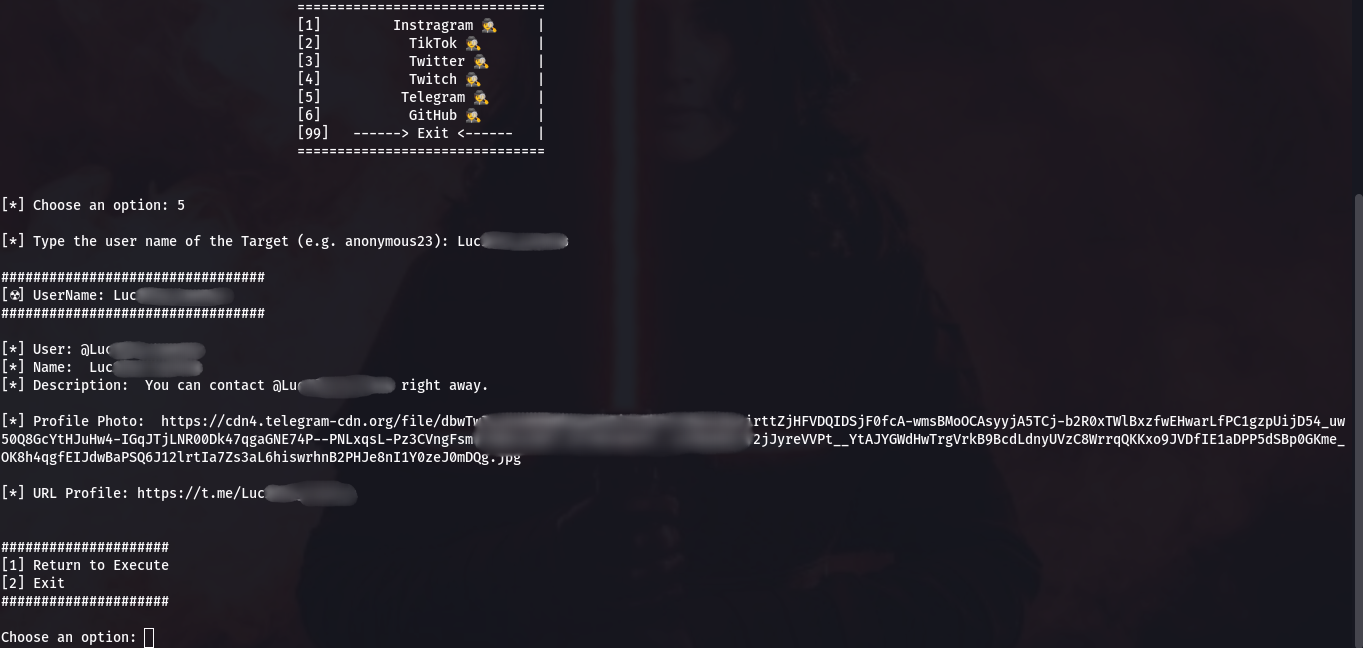
As a demo, I’ll show you how to search on Instagram, Telegram, and GitHub. Let’s start with Instagram: enter the username of the person you’re looking for and check out the results.
The results for Telegram, unfortunately, look rather sparse: you can essentially view everything yourself on any client. Even the account ID isn’t displayed, which is quite disappointing. However, you can download the avatar if you happen to need it for some reason.
There is much more information available about GitHub now, and it’s convenient that it can be accessed entirely. There’s definitely value in using it.
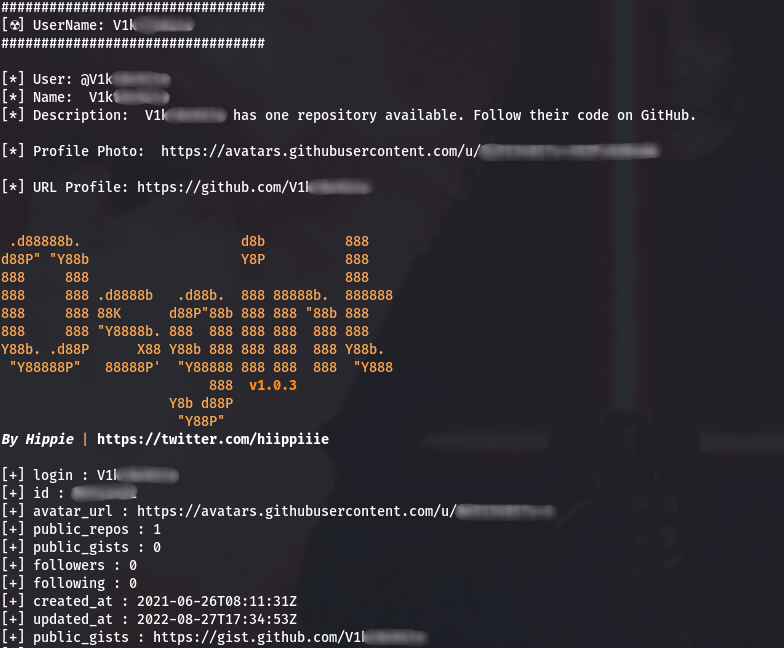
Overall, the tool provides quite comprehensive information (within the limits of what the service itself can offer) and does so without requiring any API keys for access.
Snoop Project
The Snoop Project is a promising tool, particularly useful in the CIS countries. It can search through more than 3,000 websites. I couldn’t even name a tenth of these, yet it can extract at least a bit of information from each one! A major advantage is its cross-platform capability. Snoop can be easily used on Linux, Windows, and even Android (with the help of Termux).
To install, visit the releases page of the tool, select the most recent release, and download the archive for your platform.
mkdir Snoop
wget https://github.com/snooppr/snoop/releases/download/V1.3.8_7_July_2023/Snoop.for.GNU_Linux.rar
unrar e Snoop.for.GNU_Linux.rar Snoop
It’s somewhat surprising that the author distributes the Linux binary in a RAR archive. That’s something you might only encounter in Russia.
You end up having to run something that’s more like a “black box” with unclear contents, rather than a script you can open and verify. That’s not a good practice!
But we’re working in a virtual machine, so we have nothing to fear. Let’s grant execution permissions and proceed:
chmod +x snoop_cli
./snoop_cli -f username
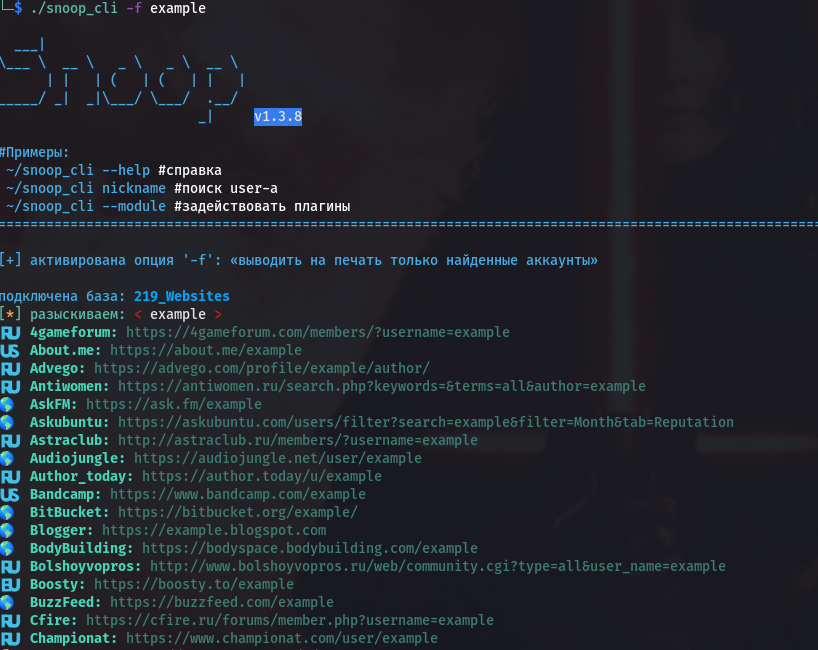
The search results are displayed not only in the terminal but also as an HTML file, making it easy to organize and sort through the information.
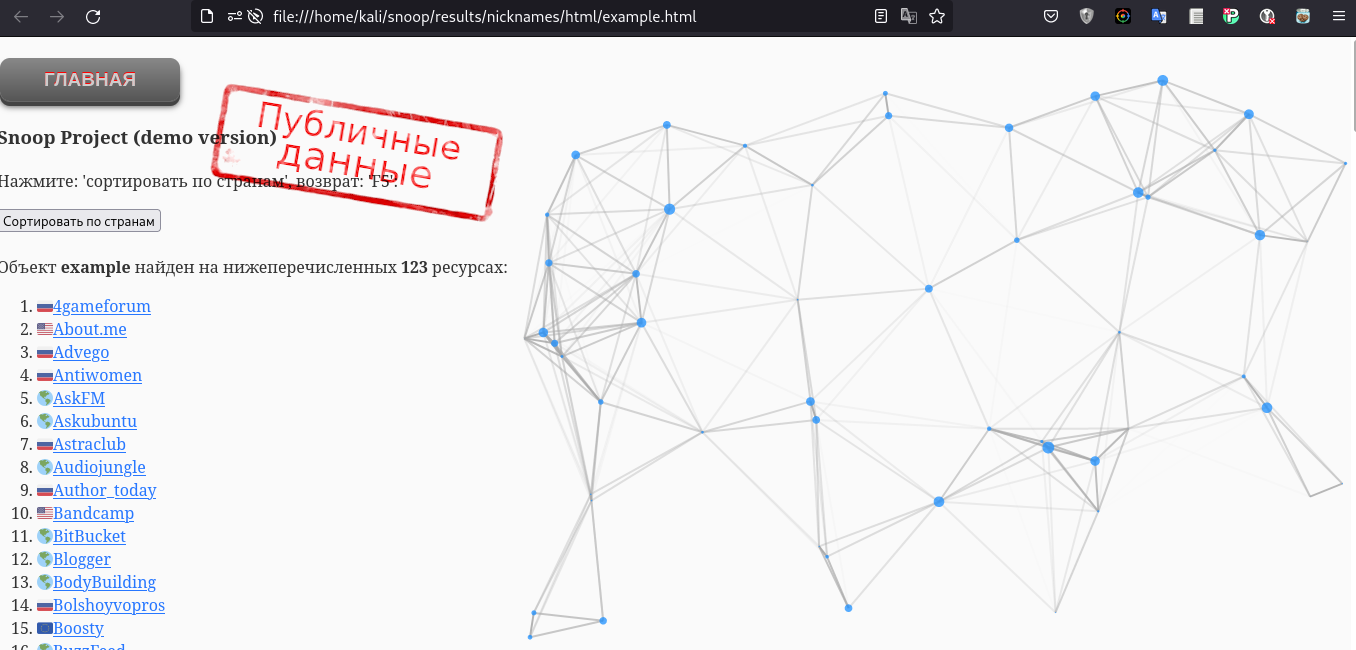
The tool is impressive, despite some quirks, and it definitely has a place in various investigations.
Toutatis
Toutatis can extract more information from an Instagram account than what is visible to a regular user. This script can even retrieve contact details such as email addresses and the last two digits of phone numbers. While it’s not a vast amount of data, it can be useful for verifying if a known phone number is associated with a specific account.
You’ll only need pip for the installation. I strongly recommend installing version 1.3, as other versions have turned out to be problematic.
pip install toutatis==1.3
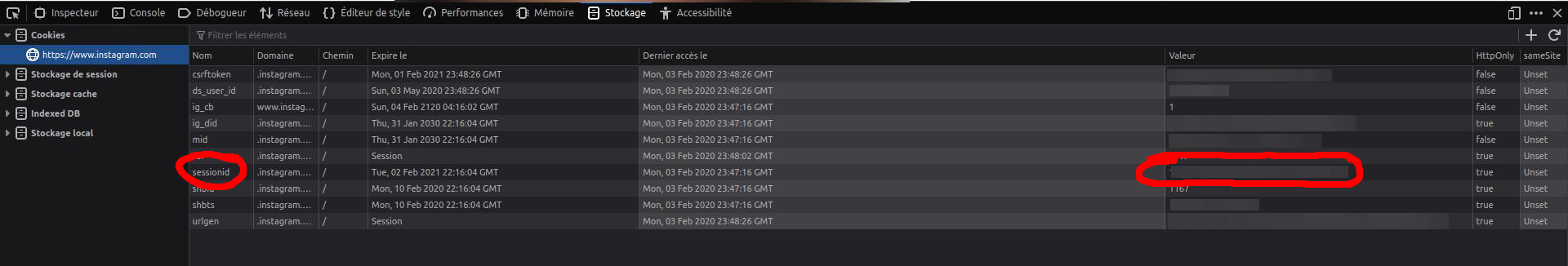
Next, we’ll need an Instagram session cookie to proceed. Log into a specially created account and copy the sessionid cookie using any convenient method. For example, press F12 in Chrome, go to the Storage tab, and you’ll find the sessionid under the Cookies section.
Copy it and insert it into the execution command using the -s argument.
toutatis -u <username> -s <sessionid>
Replace < with the username of the account you’re interested in.
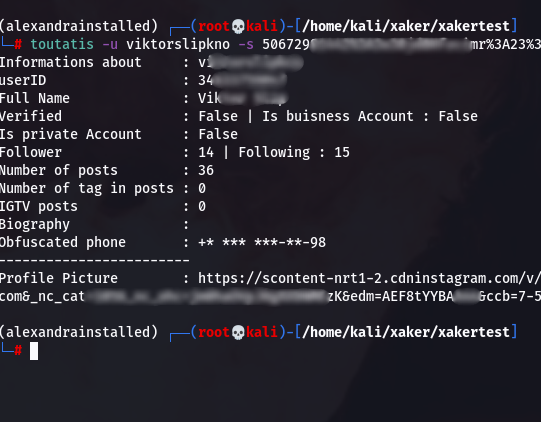
Toutatis works excellently, though it’s a bit inconvenient that you have to manually obtain the session ID. It would be even better if it could do this automatically.
Octosuite
Octosuite is a tool designed for gathering information about users, repositories, and organizations on GitHub. You can use this script to obtain data on developers, commits, issues, and more — all for free, without requiring registration or SMS verification. It’s particularly useful for those looking to integrate a wide variety of interesting tools into their username analysis pipeline but aren’t sure how to access GitHub data.
Installation is incredibly simple using pip:
pip install octosuite
The Octosuite command help is available with the -h option.
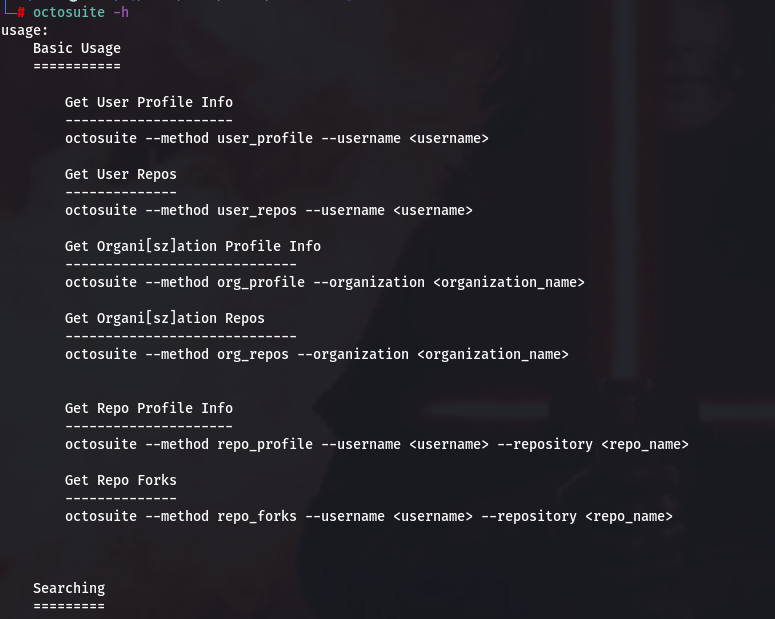
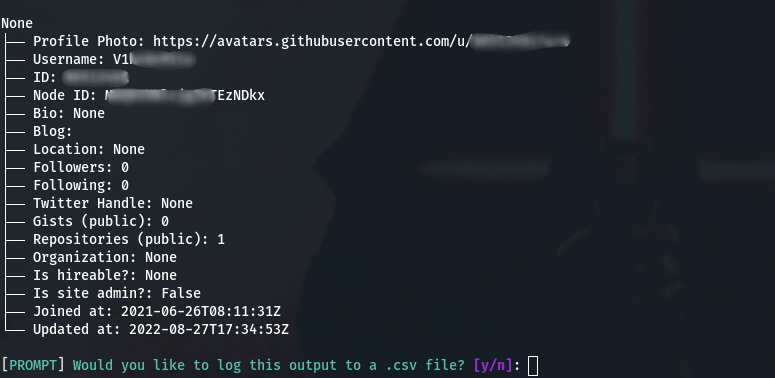
For demonstration purposes, I entered my username as an argument to see what it would output:
octosuite --method user_profile --username username
Certainly, Octosuite also offers other features, such as the ability to view a list of user repositories, detailed information about each specific repository including its forks, and much more.
Key Takeaways
Today’s five tools will be a great addition to your OSINT toolkit, even if they can’t fully replace the more advanced paid solutions. However, some of them can enhance the larger tools by covering smaller sources they might miss. This can be quite useful!
And of course, if you know of any other great programs related to our topic, feel free to share them in the comments!
