The gaming peripherals manufacturer Endgame Gear has reported that malware was embedded in the tool for configuring the OP1w 4k v2 mouse on the company’s official website from June 26 to July 9, 2025.
Reports of malware in the configuration tool for the OP1 appeared on Reddit about two weeks ago.
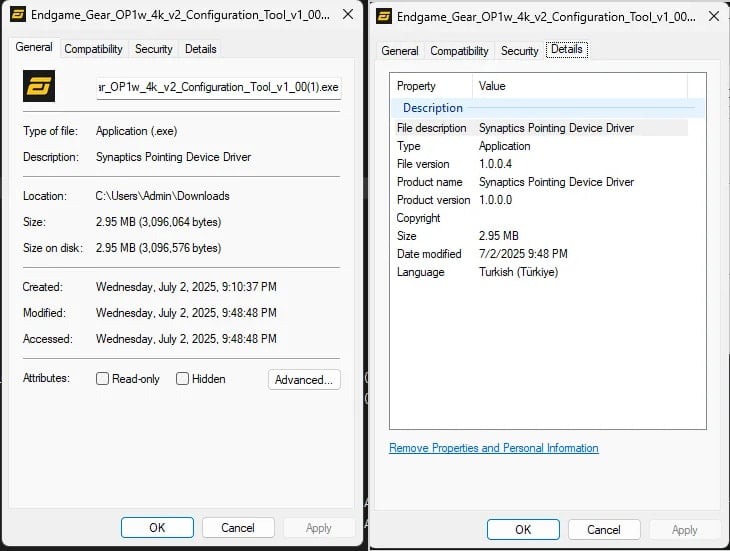
Users reported several key differences indicating that the company’s website hosted a trojanized installer. They noted the driver’s size had increased to 2.8 MB (compared to 2.3 MB in the “clean” version) and the fact that the file properties listed “Synaptics Pointing Device Driver” instead of “Endgame Gear OP1w 4k v2 Configuration Tool”.
After being uploaded to VirusTotal, the malware was identified as the XRed backdoor. However, representatives of Endgame Gear state that the analysis of the malicious payload is not yet complete.
Last week, the company confirmed that the tool Endgame_Gear_OP1w_4k_v2_Configuration_Tool_v1_00.exe hosted on their website was indeed infected with malware. However, Endgame Gear did not explain how exactly this happened.
A malicious file was published on the page endgamegear.com/gaming-mice/op1w-4k-v2, and the manufacturer emphasizes that everyone who downloaded the utility from this page during the specified period was infected. Meanwhile, users who downloaded the utility from the main downloads page (endgamegear.com/downloads), via GitHub, and Discord were not affected, as a “clean” version was distributed through these channels.
It has been reported that the malware has now been removed.
Endgame Gear recommends that users who have downloaded the malicious version of the tool delete all files from the C:\ProgramData\Synaptics folder and re-download the safe version from this page.
Since the malware has keylogger functionality, can open remote shell access to the system, and steal data, affected users are advised to conduct a full system scan using antivirus software and ensure that all remnants of the infection are eliminated.
Additionally, it is recommended to change the passwords for all important accounts, including online banking, email services, and work profiles.
Endgame Gear reports that in the future, the company will eliminate separate download pages and will add SHA-hash verification and digital signatures for all files, allowing users to confirm their integrity and the authenticity of the source.
It is worth noting that back in February 2024, analysts from eSentire warned that XRed could disguise itself as a Synaptics Pointing Device Driver. At that time, the malware was also distributed through trojanized software that was supplied with USB-C hubs sold on Amazon.