The developers of the LastPass password manager warned users about a large-scale phishing campaign that began in mid-October 2025. The attackers are sending emails with fake Emergency Access requests to their password vaults, allegedly tied to users’ deaths.
According to experts, the financially motivated hacking group CryptoChameleon (aka UNC5356) is behind this campaign. The group specializes in stealing cryptocurrency and already targeted LastPass users in April 2024.
The new campaign has proved to be larger in scope and more technically sophisticated—now the attackers are targeting not only master passwords but also passkeys.
CryptoChameleon uses a specialized phishing kit targeting crypto wallets on Binance, Coinbase, Kraken, and Gemini. In its attacks, the group actively leverages fake login pages for Okta, Gmail, iCloud, and Outlook.
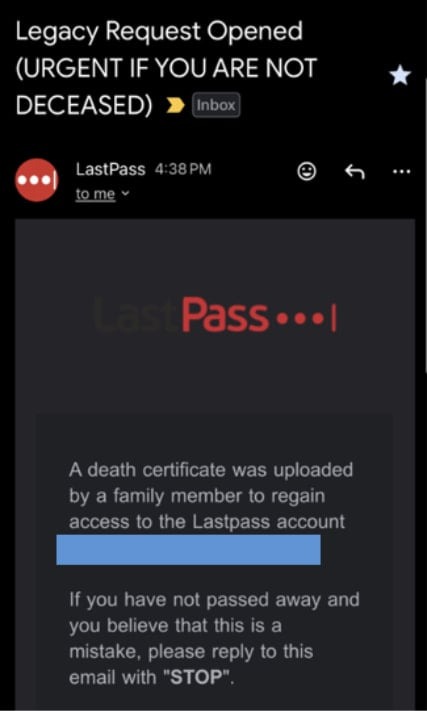
In a new campaign, scammers are abusing LastPass’s Emergency Access feature. The password manager includes an inheritance mechanism that allows trusted contacts to request access to a vault in the event of the account owner’s death or incapacity. After such a request is made, the account owner receives a notification, and if they do not cancel the operation within a specified period of time, access to the account is granted automatically.
In their emails, the phishers claim that a family member has supposedly requested access to the victim’s vault by uploading a death certificate. To make it more convincing, the message includes a fake request ID. The recipient is urged to immediately cancel the request, if they are alive, by following the provided link.
Of course, such links lead to the fraudulent site lastpassrecovery[.]com, where the victim is prompted to enter their master password.
Researchers note that in some cases, the attackers even called victims, posing as LastPass employees, and convinced them to enter their credentials on the phishing site.
A distinctive feature of this campaign is its focus on stealing passkeys. For this purpose, the attackers use specialized domains such as mypasskey[.]info and passkeysetup[.]com.
A passkey is a modern passwordless authentication standard based on the FIDO2/WebAuthn protocols. Instead of conventional passwords, the technology uses asymmetric cryptography. Modern password managers (including LastPass, 1Password, Dashlane, and Bitwarden) can store and synchronize passkeys across devices. And, as practice shows, attackers have quickly adapted to these changes.
LastPass users are advised to remain vigilant and pay close attention to any emails related to inheritance or emergency access requests. The developers remind users to always check URLs before entering credentials and emphasize that legitimate LastPass representatives will never call users asking them to enter their password on any website.
