The outlet 404 Media drew attention to a leak posted on the GrapheneOS forums. An anonymous insider using the handle rogueFed published screenshots from a closed Cellebrite briefing for law enforcement. The images show which Google Pixel…
CONTINUE READING 🡒 Author: HackMag
Zimperium: Over 760 malicious NFC apps for Android active in…
Experts at Zimperium warn of a rise in NFC malware for Android in Eastern Europe. Over the past few months, researchers have discovered more than 760 such apps using NFC attacks to steal users’ payment data.
CONTINUE READING 🡒 New version of the Android Trojan DeliveryRAT can be used…
Researchers at F6 have analyzed an updated version of DeliveryRAT. The trojan disguises itself as popular food delivery apps, marketplaces, banking services, and parcel-tracking apps. The new version adds a number of features, including carrying out DDoS…
CONTINUE READING 🡒 TEE.fail attack bypasses confidential computing protections on Intel and AMD…
A group of researchers has presented the TEE.Fail attack, which allows extracting keys and other secret data from the protected regions of Intel (SGX, TDX) and AMD (SEV-SNP) processors. These regions, called Trusted Execution Environments (TEE), are…
CONTINUE READING 🡒 Brash vulnerability crashes Chromium-based browsers
A serious vulnerability in the Blink engine can disable many Chromium-based browsers in a matter of seconds or even trigger a crash of the entire system. Security researcher Jose Pino dubbed the issue Brash and released a…
CONTINUE READING 🡒 Bypassing Firewalls with DNS Tunneling: Testing Five Popular Tools
When a firewall has completely cut off network access but you urgently need to move data, DNS tunneling can come to the rescue. The connection will be extremely slow, but it’s enough to reach into an organization’s…
CONTINUE READING 🡒 Issue allowing arbitrary code execution fixed in Fastwel PLCs
The Russian company Fastwel has released updates for its CPM723-01 and CPM810-03 programmable logic controllers, fixing nine vulnerabilities (scoring 8.3 to 9.4 on the CVSS 4.0 scale) discovered by Positive Technologies researchers.
CONTINUE READING 🡒 Herodotus Trojan bypasses defenses by typing like a human
ThreatFabric specialists report on a new banking trojan, Herodotus, which is being used in attacks against users in Italy and Brazil. The malware specializes in device takeover and attempts to mimic human behavior to bypass behavioral analysis…
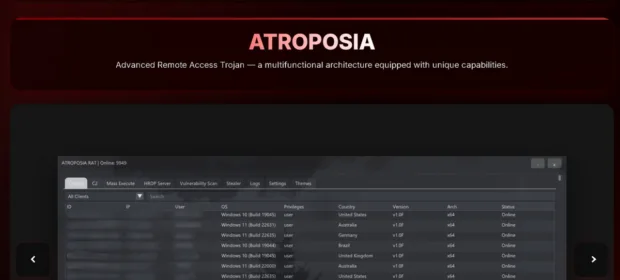
CONTINUE READING 🡒 Atroposia malware ships with a built-in vulnerability scanner
Varonis researchers discovered the Atroposia malware-as-a-service (MaaS) platform. For $200 per month, its customers get a remote access trojan (RAT) with extensive capabilities, including: remote desktop, file system control, data theft (including credentials, clipboard contents, and cryptocurrency…
CONTINUE READING 🡒 PhantomRaven Campaign: Over 100 Infostealer Packages Uploaded to the npm…
Since August 2024, as part of the PhantomRaven campaign, 126 malicious packages have been uploaded to npm, which have been downloaded more than 86,000 times in total. The campaign was discovered by experts at Koi Security, who…
CONTINUE READING 🡒 BlueNoroff Uses AI in Attacks on Blockchain Project Executives
Researchers at Kaspersky Lab reported new targeted attacks by the BlueNoroff group. The malicious GhostCall and GhostHire campaigns have been observed since April 2025, and their targets include cryptocurrency and Web3 organizations in India, Turkey, Australia, and…
CONTINUE READING 🡒 The ChatGPT Atlas browser’s omnibox is vulnerable to jailbreaking
Researchers from NeuralTrust discovered a vulnerability in OpenAI’s ChatGPT Atlas agent browser. This time, the attack vector is tied to the omnibox — the field where users enter URLs or search queries. It turns out that a…
CONTINUE READING 🡒 Chrome 0‑day exploitation tied to Hacking Team malware and Operation…
Kaspersky researchers have for the first time discovered the use of Dante spyware in real‑world attacks, developed by the Italian company Memento Labs (formerly Hacking Team). They were able to track the malware’s activity through an analysis…
CONTINUE READING 🡒 A vulnerability in ChatGPT Atlas allows injecting malicious instructions into…
Security researchers from LayerX discovered a vulnerability in OpenAI’s newly released ChatGPT Atlas browser. The issue allows attackers to inject malicious instructions into the AI assistant’s memory and execute arbitrary code.
CONTINUE READING 🡒 Ransomware operators’ revenues are falling as victims refuse to pay
The share of companies that agree to pay a ransom after ransomware attacks has fallen to a historic low — only 23% of victims accepted the attackers’ terms in the third quarter of 2025, report analysts at…
CONTINUE READING 🡒 Google says there was no leak of 183 million Gmail…
For the second time in recent months, Google has had to refute reports of a massive leak of Gmail users. The claims were sparked by publications about a “hack of 183 million accounts” that spread across the…
CONTINUE READING 🡒 Cloud Atlas group invited agricultural companies to a crop production…
In 2025, F6 specialists are recording increased activity by the Cloud Atlas group, which is targeting Russian and Belarusian companies. Researchers reported that ahead of the forum “Grain and Oilseeds 2025: Feed Vector,” which will take place…
CONTINUE READING 🡒 X asks users to re-register their passkeys or their accounts…
The social network X (formerly Twitter) warned users that by November 10 they must re-register their hardware security keys and passkeys used for two-factor authentication (2FA). If they don’t do this in time, access to their accounts…
CONTINUE READING 🡒 How to Build an Electroneum Cryptocurrency Miner in Java
These days even your grandma has heard of cryptocurrencies; reputable schools are running mining courses, and antivirus tools are increasingly flagging websites or games as being infected with miners. It’s time to get hands-on, figure out what…
CONTINUE READING 🡒 Hackers are exploiting outdated WordPress plugins at scale
Wordfence warns about a large-scale malicious campaign in which attackers are exploiting critical vulnerabilities in the popular WordPress plugins GutenKit and Hunk Companion. The company has blocked 8.7 million attempts of such attacks against its customers in…
CONTINUE READING 🡒