Google representatives announced that starting in 2026, only apps from verified developers can be installed on certified Android devices. This measure is aimed at combating malware and financial fraud, and will apply to apps installed from third-party sources.
The requirement will apply to all “certified Android devices,” that is, devices on which Play Protect is enabled and Google apps are preinstalled.
Back in 2023, similar requirements appeared in the Google Play Store, and the company claims this led to a sharp decrease in the number of malicious apps and fraud cases. Therefore, these requirements will now become mandatory for any apps, including those distributed through third-party app stores and via sideloading, that is, installation from external sources (when the user manually installs an APK file on the device).
Google likens the new requirements to an ID check at the airport.
“Think of it as an ID check at the airport — it confirms the traveler’s identity but is separate from screening their baggage. We will verify the developer’s identity, but we will not inspect the contents of their app or its origin,” the company writes.
In this way, Google wants to combat “convincing fake apps” and make it harder for attackers who start distributing another piece of malware shortly after Google removes the previous one.
It is reported that a recent analysis found that third-party sources, from which apps are installed via sideloading, contain 50 times more malware than apps available on the Google Play store.
At the same time, Google emphasizes that “developers will retain the same freedom to distribute their apps directly to users via third-party sources or to use any app store they prefer.”
To implement the new initiative, a separate, streamlined Android Developer Console will be created, intended for developers who distribute their apps outside the Google Play Store. After verifying their identity, developers will need to register their apps’ package name and signing keys.
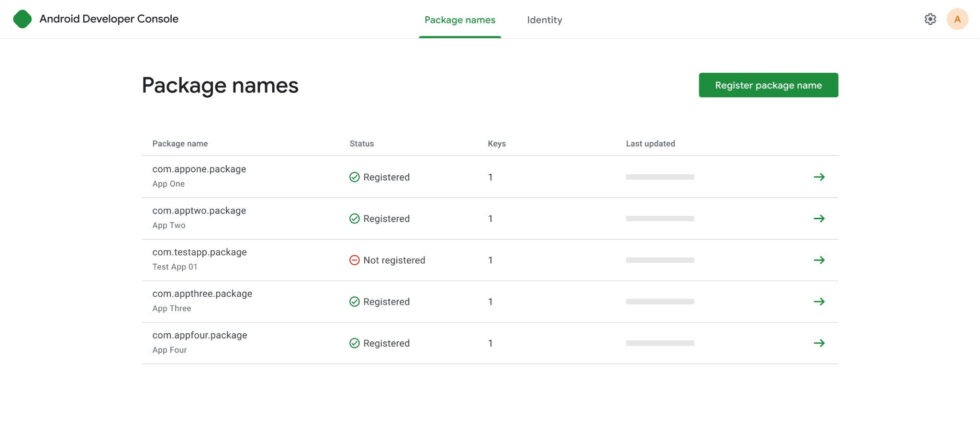
Those who distribute apps through the Google Play store “likely already meet verification requirements through the existing Play Console process,” where organizations are required to provide a D-U-N-S number (Data Universal Numbering System — a unique nine-digit identification number for legal entities).
Testing of the new verification system will start in October of this year, and the first Android developers will gain access to it. It will become available to everyone in March 2026.
The verification requirement will first take effect in September 2026 in Brazil, Indonesia, Singapore, and Thailand. Google explains that these countries are “particularly affected by such forms of fraudulent apps.” Then, in 2027, developer verification will be applied worldwide.
