Darktrace researchers have discovered a new DDoS botnet that infects misconfigured Docker containers and then sells access to customers so they can launch attacks themselves.
The botnet has been dubbed ShadowV2, and researchers report that it disrupts the traditional DDoS-as-a-service model by using a Python-based command server hosted on GitHub CodeSpaces, along with a sophisticated attack toolkit that combines traditional malware with modern DevOps technologies.
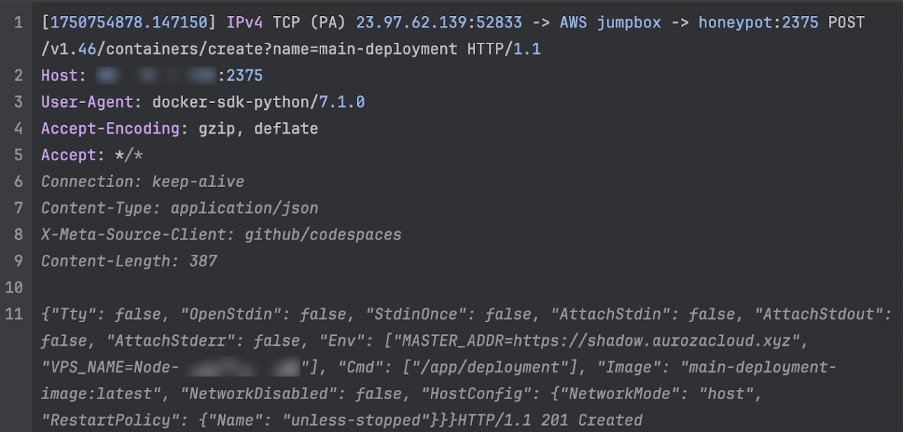
The infection chain begins with a Python script hosted in GitHub CodeSpaces that allows attackers to interact with Docker to create containers. The adversaries target internet-exposed Docker daemons running on AWS instances.
Instead of using images from Docker Hub or downloading a prebuilt image, the attackers create a regular setup container. They then deploy various tools inside it, create a new image of the customized container, and deploy it as the working container.
Instead of using images from Docker Hub or downloading a prebuilt image, the attackers create a simple setup container. They then install various tools in it, build a new image of the customized container, and deploy it as the working one.
Researchers explain that the container acts as a wrapper around a binary written in Go, which is not detected by the engines featured on VirusTotal (although two versions of the malware were uploaded there on June 25 and July 30, respectively).
Malware analysis showed that it launches multiple threads with configurable HTTP clients that use Valyala’s open-source fasthttp library, which supports high-performance HTTP requests. The malware uses these clients to carry out an HTTP flood attack.
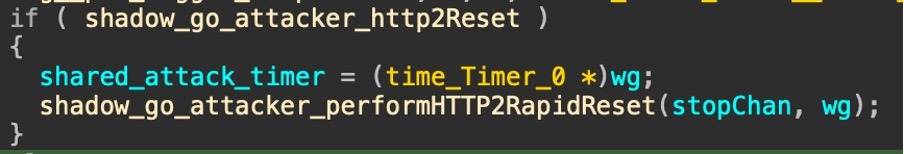
The malware also uses several defense-evasion mechanisms: HTTP/2 rapid reset, forged forwarding headers with random IP addresses, and techniques to bypass Cloudflare’s Under Attack Mode (UAM).
The malware’s command server is protected by Cloudflare, but researchers believe it is likely running in GitHub Codespaces. A misconfiguration allowed analysts to obtain a copy of the server’s API documentation and discover all API endpoints.
The discovery of a user-facing API with an authentication system, multiple privilege levels, and restrictions on attack types indicates that ShadowV2 operates under a DDoS-as-a-service (DDoS as a service) model rather than as a typical botnet.
“ShadowV2 operators don’t launch attacks themselves — they’ve built a platform where clients rent access to the infected network and run their own DDoS campaigns,” Darktrace explains.
This hypothesis is supported by the fact that, to launch an attack, users must provide the endpoint with a list of compromised systems that will be used in the DDoS.
“The API and a full-fledged interface turn this botnet into a true platform. This changes detection approaches — you should now look not for indicators on hosts, but for suspicious activity: unusual Docker API calls, automated container operations, systematic outbound connections from ephemeral nodes. Defenders should view ShadowV2 as a commercial product with a development roadmap — track modular updates, abuses of cloud services, and new rental models rather than isolated campaigns,” the experts conclude.
