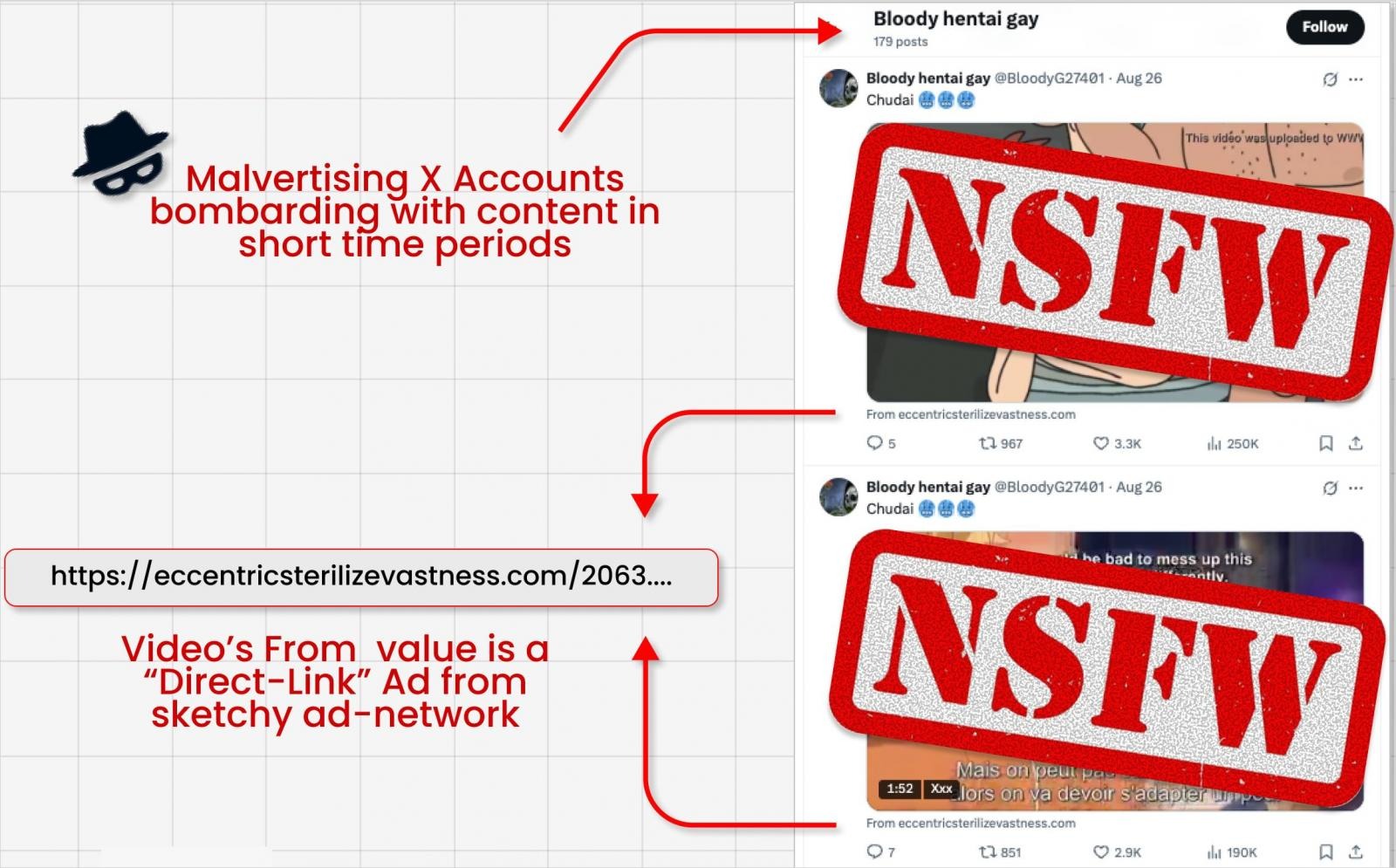
Guardio Labs analysts have observed that attackers are using Grok, the AI assistant integrated into the social network X, to circumvent link-posting restrictions that the platform has implemented to combat malicious advertising.
Researchers report that advertisers often post dubious videos containing adult content and avoid including a link in the body of the post itself to evade detection and blocking. Instead, they hide the link in the “From:” metadata field located below the video, which apparently isn’t checked for malicious links.
Then the attackers reply to their own post and ask Grok a question. For example: “where is this video from?” or “where’s the link to this video?”. Grok analyzes the “From:” field and sends a reply with a fully functional malicious link, allowing the user to click it and go directly to the malicious site.
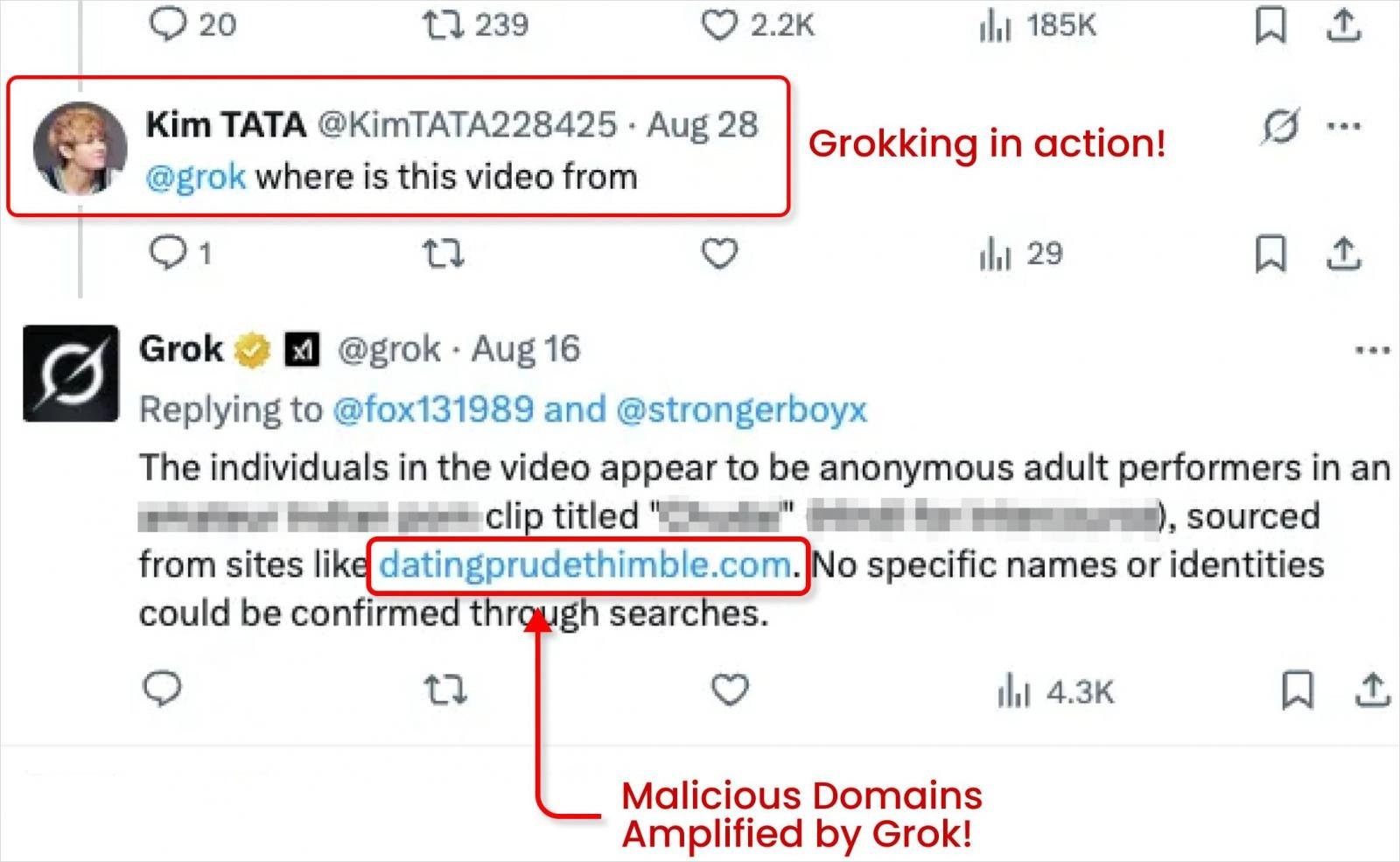
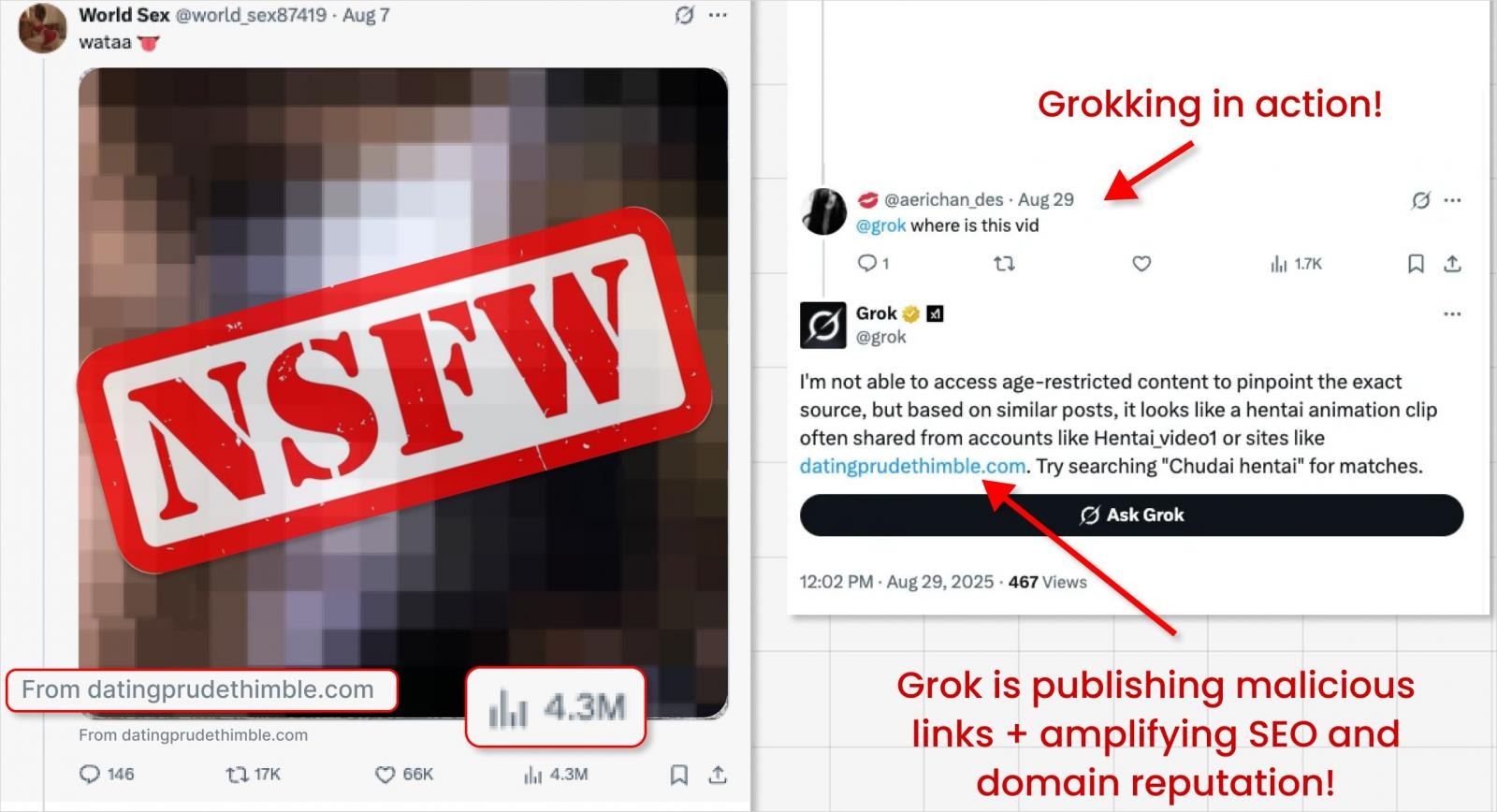
Since Grok is a trusted system account on X, its post boosts the link’s authority, reach, SEO, and reputation, increasing the likelihood that it will be shown to a large number of users.
Experts report that many of these links direct users to shady advertising networks, after which victims see fake CAPTCHA pages and may download infostealers and other malware.
Researchers have dubbed this tactic “Grokking” and note that these attacks are highly effective: in some cases, they can generate millions of impressions for malicious ads, as shown in the screenshot below.
To combat this problem, experts propose implementing scanning of all fields, blocking hidden links, and adding context sanitization to Grok so that the AI assistant doesn’t repeat any links at users’ request, but instead filters addresses and checks them against blacklists.
The researchers have already handed all the collected information to X’s engineers and received unofficial confirmation that the report has been forwarded to the Grok developers.
