The maintainers of the PyPI (Python Package Index) repository announced that they will now be countering domain-resurrection attacks, which allow attackers to take over other users’ accounts via password resets.
Since PyPI is the official repository for Python packages, it is actively used by software developers, project maintainers, and companies working with Python libraries, tools, and frameworks.
Maintainer accounts for projects publishing packages on PyPI are tied to email addresses. The problem is that if the domain name hosting such a mailbox expires, attackers can re-register it and use it to take over the project on PyPI (after setting up a mail server and submitting a password reset request for the account).
This creates risks of supply chain attacks, because compromised projects can distribute malicious versions of popular Python packages, and in many cases those will be installed automatically via pip.
A vivid example of such an attack is the compromise of the ctx and phppass packages that occurred in 2022. At the time, the packages were deliberately modified by a security researcher, who made them exfiltrate environment variables and search for Amazon AWS credentials and keys.
At the time, the researcher faced harsh criticism from the community. Typically, bug bounty exploits targeting open-source libraries use simple code, for example, printing “you’ve been hacked!” on the target system or exfiltrating some basic information (such as the user’s IP address, hostname, and working directory). However, stealing environment variables and AWS credentials could hardly be called “ethical.”
As reported, in an effort to address this issue, PyPI will check whether the domain registrations of verified email addresses have expired. For security reasons, such addresses will be marked as unverified.
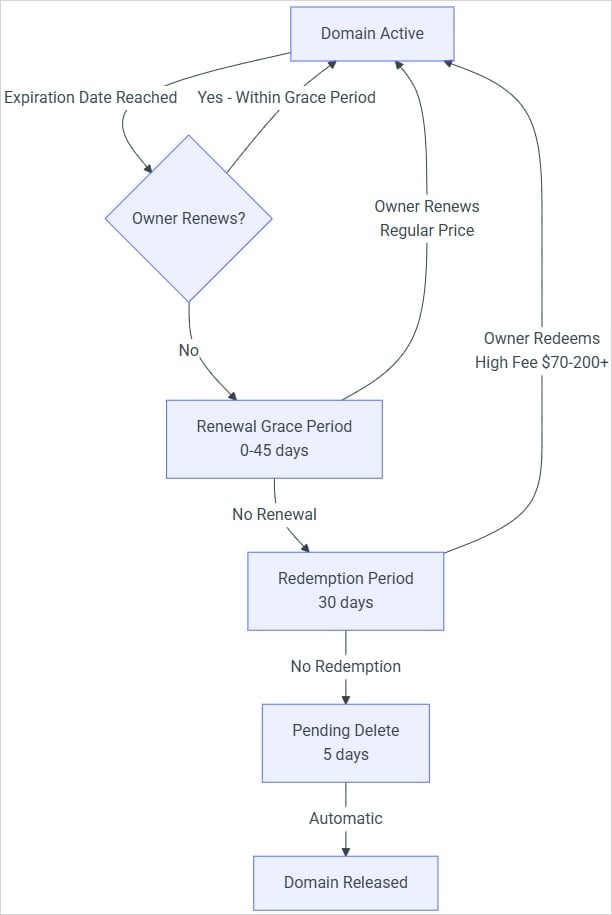
To determine whether action needs to be taken regarding a specific account, PyPI uses Domainr’s Status API to determine the domain’s status (active, grace period, redemption period, pending deletion).
If these checks result in the email addresses being marked as unverified, they cannot be used for password resets or other account recovery actions. In other words, even if an attacker registers that domain for themselves, the attack will not succeed.
According to PyPI, the development of new protective measures began back in April 2025, and trial scans started at the same time, becoming daily by June.
Since then, more than 1,800 email addresses have been identified and marked as unverified because they were at risk.
Although the new measures are not a foolproof defense and do not protect against other attack scenarios, they significantly reduce the risk of PyPI accounts being hijacked by attackers through the exploitation of expired domains.
PyPI recommends that users add a backup email address to their account using a domain from a major service rather than their own, to avoid any disruptions, and also enable two-factor authentication to enhance security.
