Experts from F6 and RuStore report that they have discovered and blocked 604 domains that were part of the hackers’ infrastructure used to infect mobile devices with the DeliveryRAT trojan. The malware disguised itself as popular food delivery apps, marketplaces, banking services, and parcel-tracking apps.
Back in the summer of 2024, F6 analysts discovered a new Android Trojan, which they named DeliveryRAT. Its primary purpose was to collect sensitive data to apply for loans at microfinance institutions, as well as to steal money via online banking.
Later, a Telegram bot called Bonvi Team was discovered, where DeliveryRAT was distributed under a MaaS (Malware-as-a-Service) model. It turned out that through the bot, attackers obtain a sample of the Trojan for free, after which they must deliver it to the victim’s device themselves.
The bot’s operators offer two options: download the compiled APK or get a link to a fake site, which is presumably generated individually for each worker.
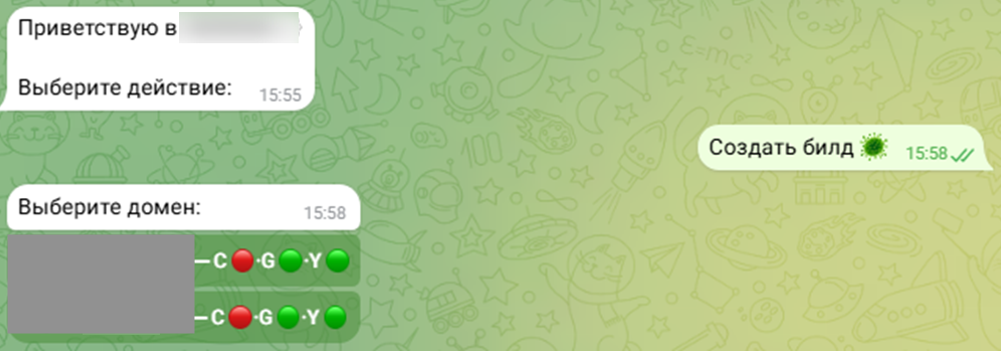
Victims’ devices were infected using several common scenarios.
“To attack victims, the criminals used various crafty scenarios: they created fake classifieds for buying and selling, or bogus listings advertising high-paying remote jobs,” says Evgeny Egorov, lead analyst of the Digital Risk Protection department at F6. “They then move the conversation with the victim to messaging apps and convince them to install a mobile app, which turns out to be malicious.”
Thus, attackers create listings with underpriced goods on marketplaces or in fake stores. Posing as a seller or manager, the criminals contact the victim via Telegram or WhatsApp, and during the conversation the victim provides their personal data (recipient’s full name, delivery address, and phone number). To track the fake order, the “manager” asks them to download a malicious app.
Hackers also create fake remote job postings with attractive terms and pay. They move communication with the victim to messaging apps, where they first collect the victim’s data: SNILS (Russian social insurance number), card number, phone number, and date of birth. Then the scammers ask them to install a malicious app that is supposedly necessary for the job.
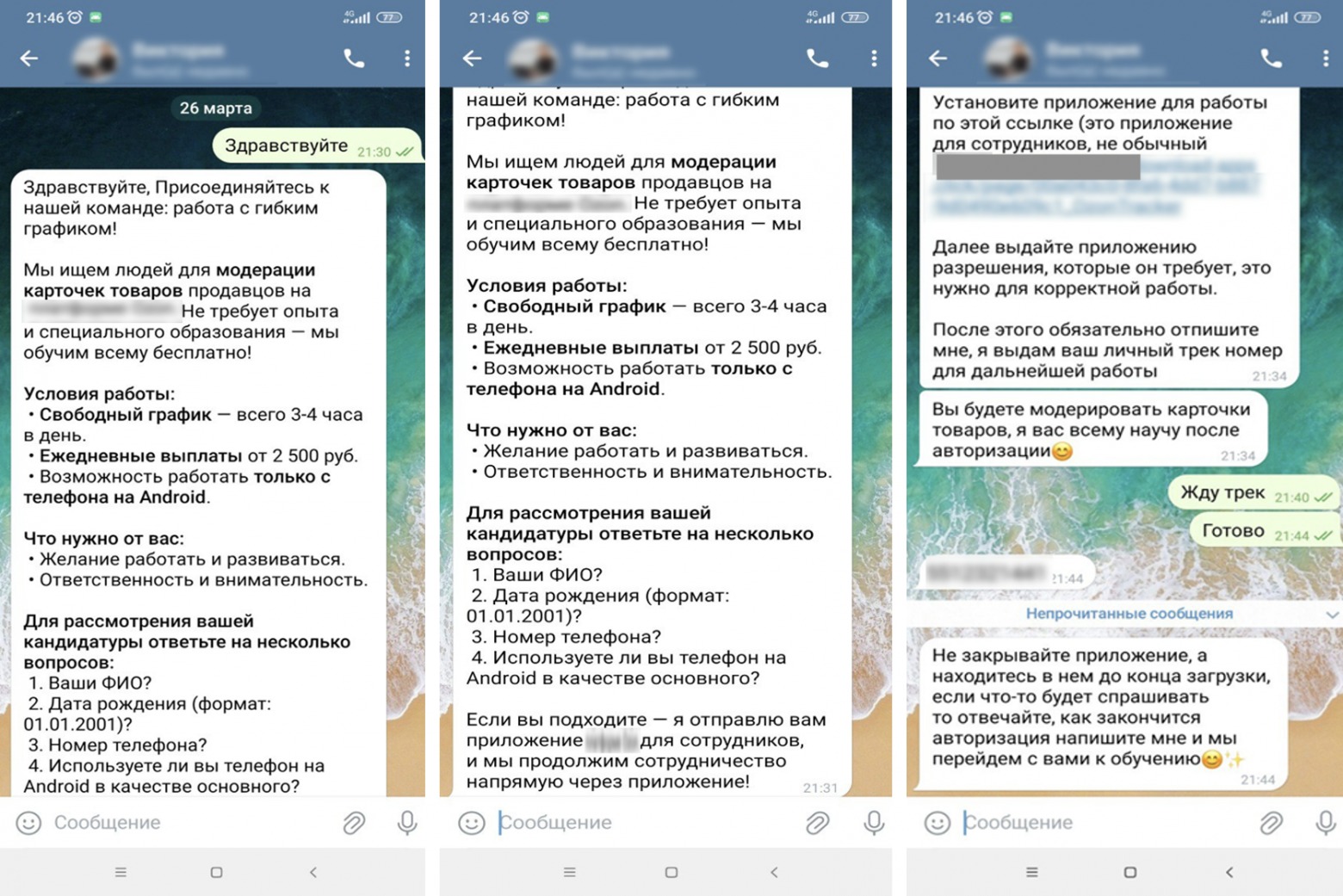
In addition, experts discovered promotional posts on Telegram offering to download a DeliveryRAT-infected app. In these cases, the malware typically disguised itself as apps with discounts and promo codes.
The report notes that the fraudulent scheme has become widespread because creating auto-generated links via Telegram bots does not require any specialized technical knowledge. Researchers also cite a high degree of process automation as a key feature of the scheme.
Experts report that as of today they are aware of at least three groups that lure victims to malicious resources to install this malware.
Researchers have identified and blocked 604 domains that were used in the attackers’ infrastructure. It is noted that the domain names are often generated using combinations of similar keywords such as store, id, download, app, and others.
