Microsoft Threat Intelligence researchers have discovered a new variant of the XCSSET malware for macOS. The new version monitors the system clipboard to intercept cryptocurrency transactions and achieves persistence using a new method.
XCSSET is a modular macOS malware with capabilities for stealing information and cryptocurrency. The malware exfiltrates Notes, data from cryptocurrency wallets, and browsers from infected devices. It spreads by finding and infecting other Xcode projects on the victim’s device, causing the malware to execute when the project is built.
“XCSSET is designed to infect Xcode projects, which are typically used by software developers, and it runs during the build process,” Microsoft explains. “We believe this infection and propagation method relies on project files being shared among developers of Apple or macOS applications.”
Researchers note that the new version of the malware has undergone some changes. Specifically, it now attempts to steal data from the Firefox browser by installing a modified build of the open-source tool HackBrowserData, which is used to decrypt and export browser data.
Additionally, the updated XCSSET includes a clipboard-hijacking component that monitors the macOS clipboard for regular expression patterns associated with cryptocurrency addresses. If a crypto address is detected, the malware replaces it with one belonging to the attacker. As a result, any cryptocurrency sent by the user from the infected device ends up in the attackers’ hands.
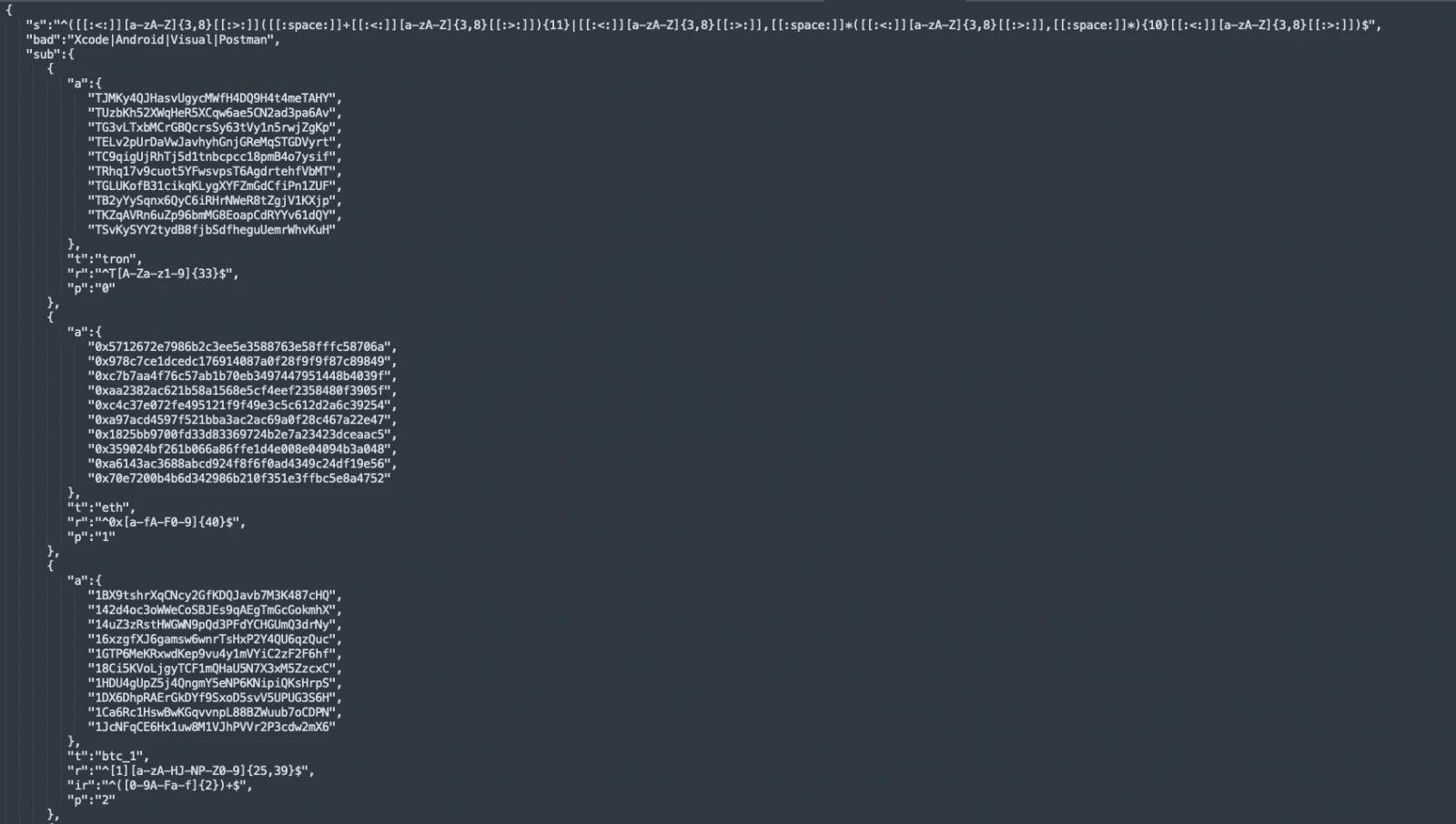
Additionally, the malware now uses new methods to persist on the infected system, including creating LaunchDaemon entries that execute the ~/.root payload, and creating a fake System Settings.app in /tmp to disguise itself.
According to Microsoft researchers, the new variant has not yet seen widespread distribution, although they have already observed its use in limited attacks.
It is reported that the researchers have already shared their findings with Apple and are also working with GitHub experts to remove repositories associated with XCSSET.
To protect against such attacks, experts recommend keeping macOS and applications up to date, especially considering that XCSSET has previously exploited zero-day vulnerabilities. Developers are also advised to always review Xcode projects before building them.
