Experts at Lumen Technologies warned that operators of the SystemBC botnet are hunting for vulnerable VPS instances and turning them into proxies. Roughly 1,500 bots are active within SystemBC each day, providing criminals with a channel for malicious activity.
According to researchers, the compromised servers are located worldwide. All of them have at least one unpatched critical vulnerability, and some suffer from dozens of different issues.
The SystemBC botnet has been active since at least 2019 and has previously been used by various hacker groups, including ransomware operators, to deliver payloads. The botnet allows attackers to route malicious traffic through compromised hosts and hide the activity of command-and-control servers.
Experts report that SystemBC is designed to handle large volumes of traffic, and its operators pay little attention to stealth. In addition, the botnet serves as a foundation for other proxy networks and is characterized by an “extremely long average infection duration.”
Neither SystemBC clients nor its operators care about stealth, since the bots’ IP addresses are not protected in any way (for example, through obfuscation or rotation). SystemBC has more than 80 command-and-control servers that connect clients to infected proxies and supply other proxy services.
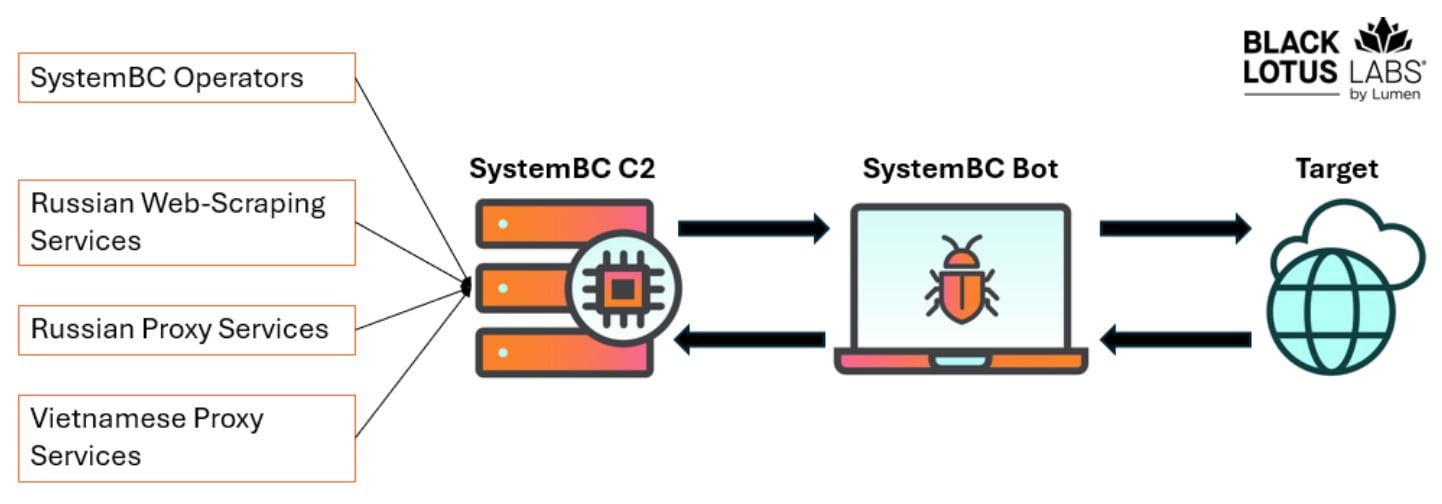
One such malicious service—REM Proxy—is 80% powered by SystemBC bots, delivering services to its clients depending on the required proxy quality. Among other SystemBC customers, researchers mention a major Russian-language web-scraping service, as well as a Vietnamese proxy network known as VN5Socks or Shopsocks5.
Researchers note that, most often, SystemBC operators use the botnet to brute-force WordPress credentials. They then likely sell them to brokers, who use this data to inject malicious code into websites.
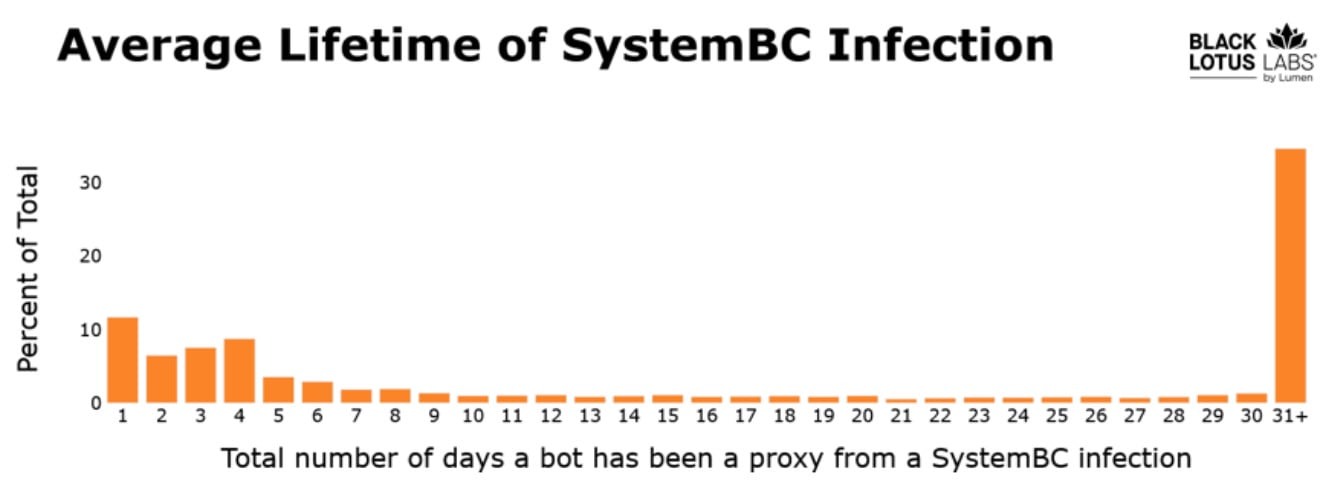
Experts report that nearly 80% of the SystemBC network consists of compromised VPS from several “major commercial providers.” This allows attackers to achieve longer infection durations. For example, nearly 40% of systems remain compromised for more than a month.
Moreover, compromising VPS systems allows SystemBC to provide large and stable traffic volumes for clients, which is impossible when using residential proxies based on SOHO devices. For example, researchers observed that “a specific IP address generated more than 16 GB of proxy data in just 24 hours.”
“This volume of data exceeds by an order of magnitude what is usually observed in typical proxy botnets,” the researchers state.
According to global IP telemetry, a single address (104.250.164[.]214) appears to be at the center of activity for finding and infecting new victims, and it also hosts all 180 samples of the SystemBC malware.
