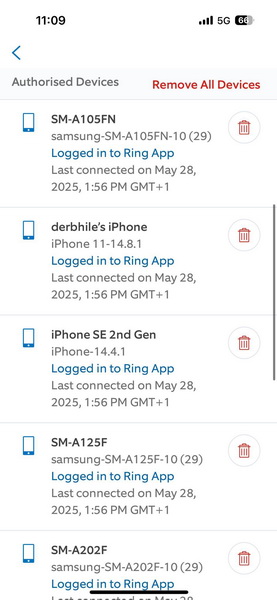
Users of Ring are observing multiple notifications about account logins from unauthorized devices, dated May 28, 2025. Ring developers claim that this is due to an error during a backend update.
Many Ring users received notifications indicating that on May 28, 2025, there were logins to their accounts from unusual devices located around the world. Naturally, this led people to assume that their accounts had been compromised.
Last week, Ring representatives stated that they are aware of “a bug that caused previous login dates to incorrectly appear as May 28, 2025.” The company also updated the Ring status page, indicating that reports of unauthorized logins were the result of a backend update error.
“We are aware of an issue related to the incorrect display of information in the Control Center,” states the official statement. “This is a result of a backend update, and we are working on resolving the issue. We have no reason to believe that any unauthorized access to customer accounts actually occurred.”
However, as reported by Bleeping Computer, users do not believe Amazon’s official explanations. People are writing that they have seen unknown devices, strange IP addresses, and countries they have never visited in the lists of authorized client devices. Therefore, these entries could not relate to previous system logins.
“Your ‘bug’ is absolute nonsense, and I don’t know any Derbhile, are they somehow connected to our Ring camera or family? Just admit you got hacked and fix it,” writes one user, attaching a screenshot to their message on X that shows a login from a device named “derbhile’s iPhone”.
“It’s interesting that you call this a ‘bug’, although one of several logins to my account that day was made from Spain, and I live in Texas. So this doesn’t look like a bug or a login from ‘previous devices’ at all. I assure you, I’ve never been to Spain,” another user notes.
Suspicions that Amazon might be concealing information about some incident are intensifying due to the fact that the backend update issue should have been resolved promptly. However, even several days later, people continued to receive alerts about logins from unknown devices.
Worse yet, some users report witnessing strange activity in real time when none of their family members have accessed the app. Others complain that they received no security notifications or two-factor authentication requests when adding new devices.
Journalists from Bleeping Computer reached out to Amazon representatives for comment, inquiring why Ring users are seeing devices in their accounts that they have definitely never owned and countries they have never visited.
However, Amazon did not provide the publication with any new information. The company reiterated that the IP addresses and devices users see on the Authorized Client Devices page have previously been used to log into the Ring account. Amazon noted that among these records, there may be devices that people no longer own, as well as devices of users with whom Ring account owners once shared their credentials.