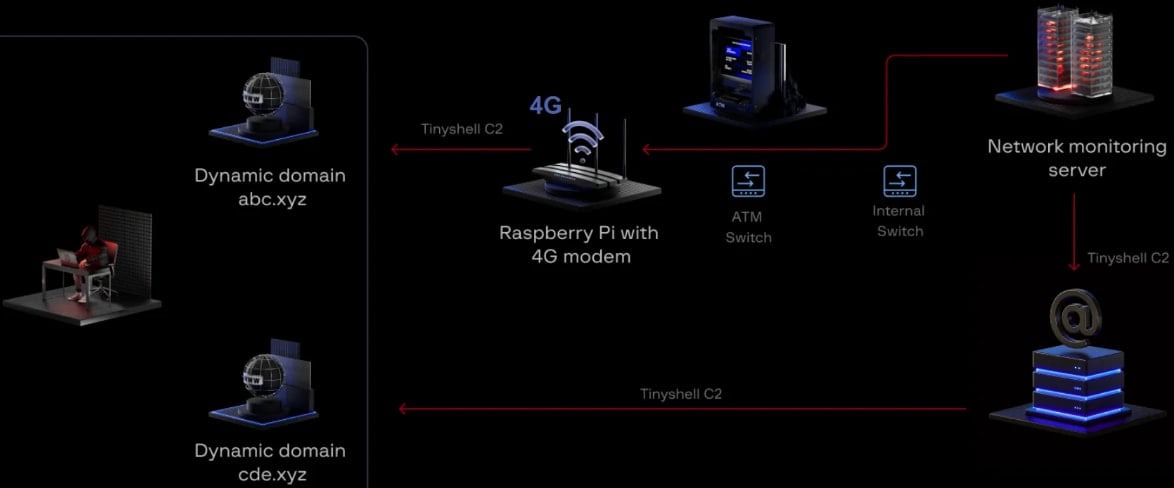
Group-IB reported that the hacker group UNC2891 (also known as LightBasin) used a Raspberry Pi with 4G support to infiltrate a bank’s network and bypass its security systems. The single-board computer was connected to the same network switch as the ATM, creating a channel into the bank’s internal network. This allowed the attackers to perform lateral movement and install backdoors.
According to researchers who discovered the compromise while investigating suspicious activity within the bank’s network, the aim of this attack was to spoof ATM authorization and carry out cash withdrawal operations.
Although the LightBasin attack was unsuccessful, researchers note that the incident is a rare example of an advanced hybrid attack (combining physical and remote access), which also utilized multiple anti-forensic methods.
The LightBasin group, active since 2016, is not new to attacking banking systems. For instance, back in 2022, experts from Mandiant reported on a then-new Unix rootkit named Caketap, designed to operate on Oracle Solaris systems used in the financial sector.
Researchers concluded that the ultimate goal of Caketap was to intercept card verification data and PIN codes from compromised ATM servers and subsequently use this information for unauthorized transactions.
The messages intercepted by Caketap were intended for the Payment Hardware Security Module (HSM), a secure hardware device used in the banking sector for the generation, management, and validation of cryptographic keys for PIN codes, magnetic stripes, and EMV chips.
In an attack discovered by Group-IB, members of LightBasin gained physical access to a branch of an unnamed bank, either on their own or by bribing an employee, who assisted the hackers in placing a Raspberry Pi with a 4G modem on the same network switch as an ATM. This allowed the perpetrators to maintain constant remote access to the bank’s internal network, bypassing firewalls.
The Raspberry Pi had the TinyShell backdoor installed, which the attacker used to create a communication channel with the command server through the mobile network.
In the subsequent stages of the attack, the intruders moved to the Network Monitoring Server, which had extensive capabilities for connecting to the bank’s data center.
From there, the attackers moved to the mail server, which had direct access to the internet, and maintained their presence in the organization’s network even after the Raspberry Pi was discovered and removed.
The backdoors that the attackers used for lateral movement were named lightdm to mimic the legitimate LightDM manager used in Linux systems. Another element that contributed to the high level of stealth was the mounting of alternative file systems (tmpfs and ext4) over the /proc/[pid] paths of the malicious processes. This allowed them to hide associated metadata from forensic tools.
According to researchers, the attackers’ ultimate goal was to deploy the Caketap rootkit, but this plan was thwarted as the attack was detected.