Experts from Solar 4RAYS of the “Solar” Group discovered a new hacking group called Proxy Trickster, which engages in cryptocurrency mining and proxyjacking (hijacking control over servers for transformation and sale). Over the course of a year, the attackers targeted nearly 900 servers in 58 countries worldwide, including Russia.
In March 2025, specialists investigated a cybersecurity incident at an unnamed Russian IT company and discovered the activity of a previously unknown group, which has been named Proxy Trickster.
The hackers primarily earn income from cryptocurrency mining and proxyjacking, which involves taking control of legitimate servers through known vulnerabilities, converting them into proxy servers, and then selling them on the darknet to other criminals, who use them to conceal their activities and IP addresses.
The first traces of Proxy Trickster attacks were dated to May 2024, and since then, the hackers have not ceased their activities.
In the attack studied by experts, the entry point could not be restored. However, analysts from Cado Security reported that the group is exploiting previously discovered vulnerabilities in Selenium Grid. In the case examined by Solar 4RAYS, this software was not used, leading to the suggestion that the group targets various publicly available services that contain already known vulnerabilities.
In over a year of activity, the hacker group infected at least 874 devices across 58 countries. The most attacked servers were found in the USA (16% of the total infected servers), Germany (6%), Russia (4%), Ukraine (4%), France (4%), and other countries. Researchers conclude from this that the hackers are not concerned about the geographical location of their targets — they attack any accessible servers for profit.
Researchers believe that the group is more amateur, but uses tools and techniques of professional hackers, attacking with the aim of espionage and destructive actions.
For example, Proxy Trickster replaces system utilities (ps, pstree, pkill) with custom scripts that disguise malicious processes (such as [kworker/u8:1-events_unbound]) from system administrators. Additionally, it employs multi-layered attack automation.
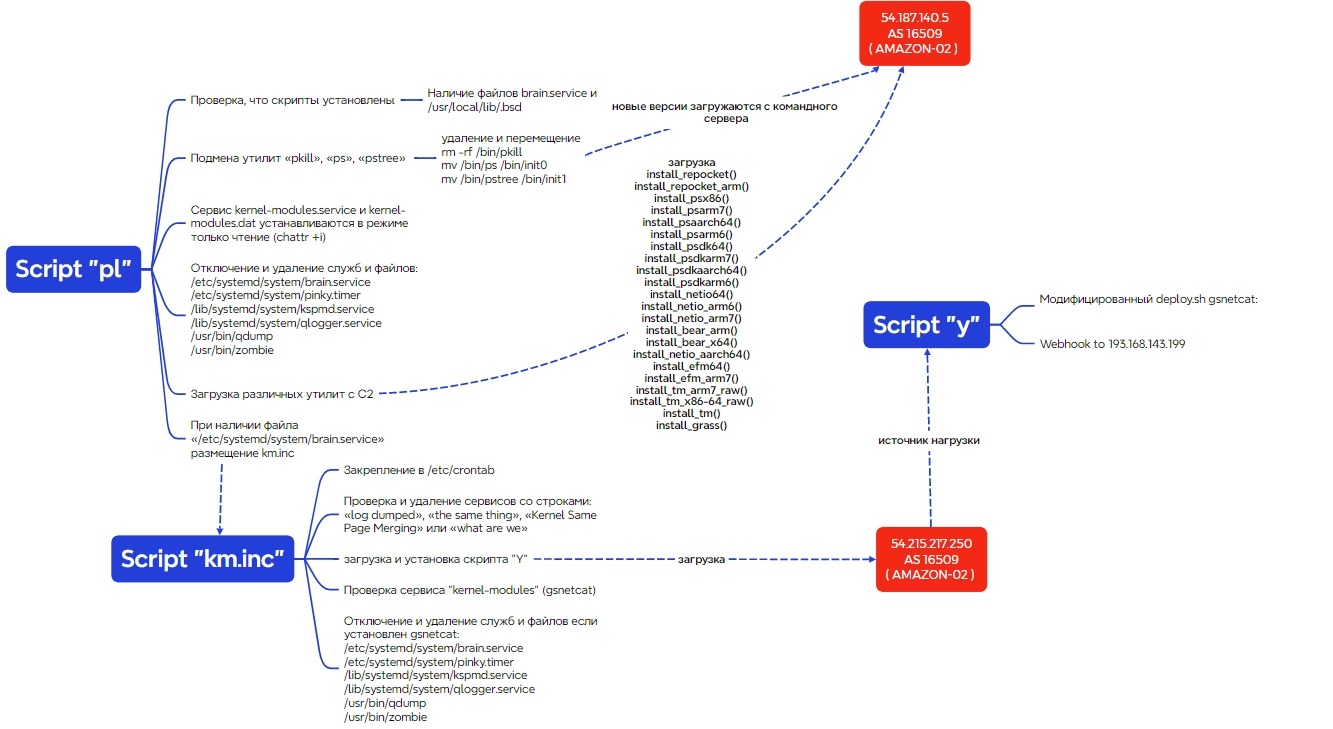
In addition, the group maintains access to compromised servers, which theoretically allows for more complex attacks. This means the group could pose a threat to hundreds, if not thousands of companies, including those in Russia.
“At Solar 4RAYS, we have not yet found confirmation that these hackers have executed more complex attacks, but that does not mean it cannot happen in the future. For example, access to compromised servers could be sold to other malicious actors who might use it to carry out more serious attacks. Security teams within organizations should pay attention to this threat and take measures to protect against it,” comments Ivan Syukhin, head of the incident investigation group at Solar 4RAYS Research Center, Solar Group.