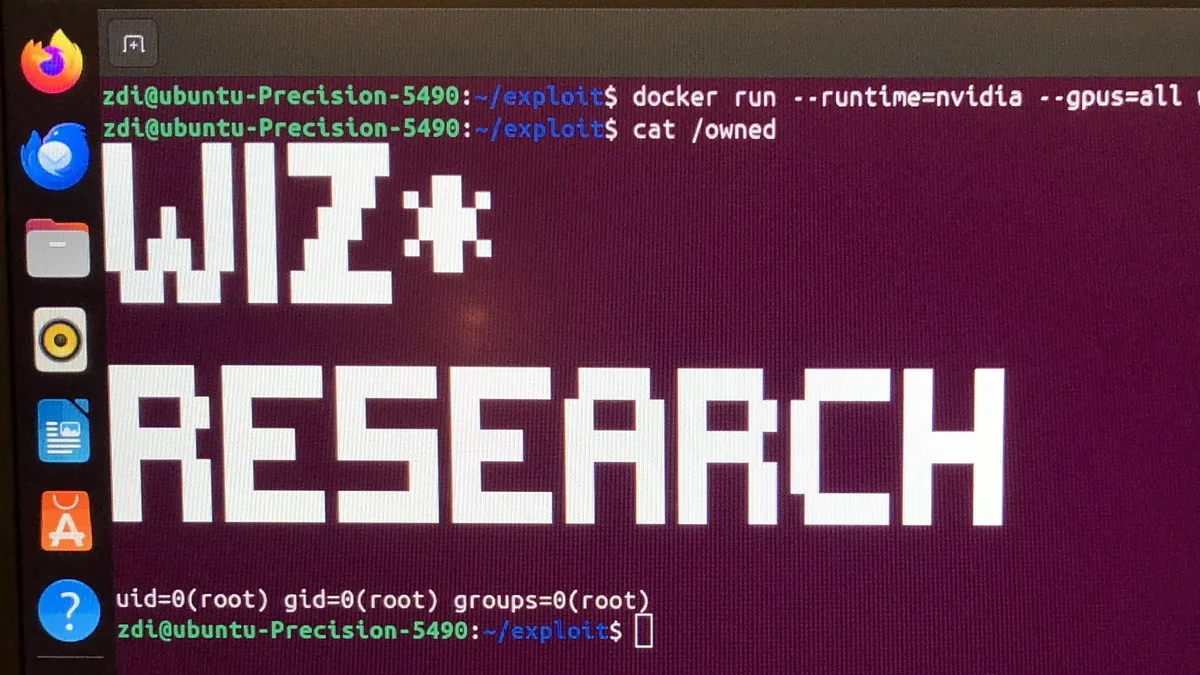
Experts from the company Wiz have discovered a critical vulnerability in the Nvidia Container Toolkit. According to the researchers, the issue could pose a significant threat to managed cloud AI services.
The vulnerability has been named NvidiaScape and is identified as CVE-2025-23266 (9.0 on the CVSS scale). The issue was first demonstrated by Wiz experts in early 2025 at the Pwn2Own Berlin hacking competition. At that time, the bug and its exploit earned the company’s team a reward of $30,000.
Developers at Nvidia have informed customers about a vulnerability and its patch in a bulletin published last week. According to the manufacturer, this critical vulnerability can lead to privilege escalation, information disclosure, data manipulation, and DoS attacks.
The bug affected all versions of the Nvidia Container Toolkit up to and including 1.17.7 and the Nvidia GPU Operator up to and including 25.3.0. The manufacturer resolved the issue in versions 1.17.8 and 25.3.1, respectively.
Nvidia Container Toolkit is designed for creating and running GPU-accelerated containers and, according to researchers, it is often used by major cloud providers in the operation of managed AI services.
Wiz explains that CVE-2025-23266 is caused by the incorrect configuration of Open Container Initiative (OCI) hooks — mechanisms that allow certain actions to be executed at different stages of a container’s lifecycle. The bug poses the greatest risk to managed AI services in the cloud, where users can run their own containers on shared GPU infrastructure.
This means NvidiaScape can be used by a malicious container to bypass isolation and gain full root access to the host machine. From the host machine, an attacker can steal or manipulate data, as well as impact proprietary AI models of other clients using the same hardware.
Now that the patch has been released, experts have shared technical details of the vulnerability and demonstrated that it can be exploited using a malicious payload and a three-line Dockerfile placed inside the container image.
“This research once again highlights that containers are not a reliable security barrier and should not be relied upon as the sole means of isolation,” warns Wiz. “When developing applications, especially for multi-user environments, vulnerabilities should always be assumed, and at least one reliable isolation barrier, such as virtualization, should be implemented.”