Adversa researchers have published an analysis of the top 25 Model Context Protocol (MCP) vulnerabilities. They describe this list as “the most comprehensive analysis of MCP vulnerabilities to date.”
Model Context Protocol (MCP), developed by Anthropic and released as an open standard in 2024, is essentially a standard method for establishing consistent and secure connections between data sources and AI tools. MCP defines how AI agents interact with tools, other agents, data, and context in a safe and accountable way.
Like any other software, MCP can contain vulnerabilities that attackers can exploit, and we discussed this quite recently in a separate article.
It is already known that OWASP plans to compile its own MCP Top 10 issues; however, it is not available yet and will likely be limited to just ten vulnerabilities in the future. Adversa specialists write that they are not trying to compete with OWASP, but aim to provide immediate assistance to companies that are currently developing and deploying agentic AI solutions.
“We will map to OWASP/CSA/NIST where appropriate, and we also plan to contribute to OWASP’s MCP work as it becomes formalized,” the researchers say.
The Adversa vulnerabilities table includes the recommended “official” name of the issue (plus common alternative names), an assessment of the vulnerability’s impact, a rating of its exploitability, as well as links to additional information.
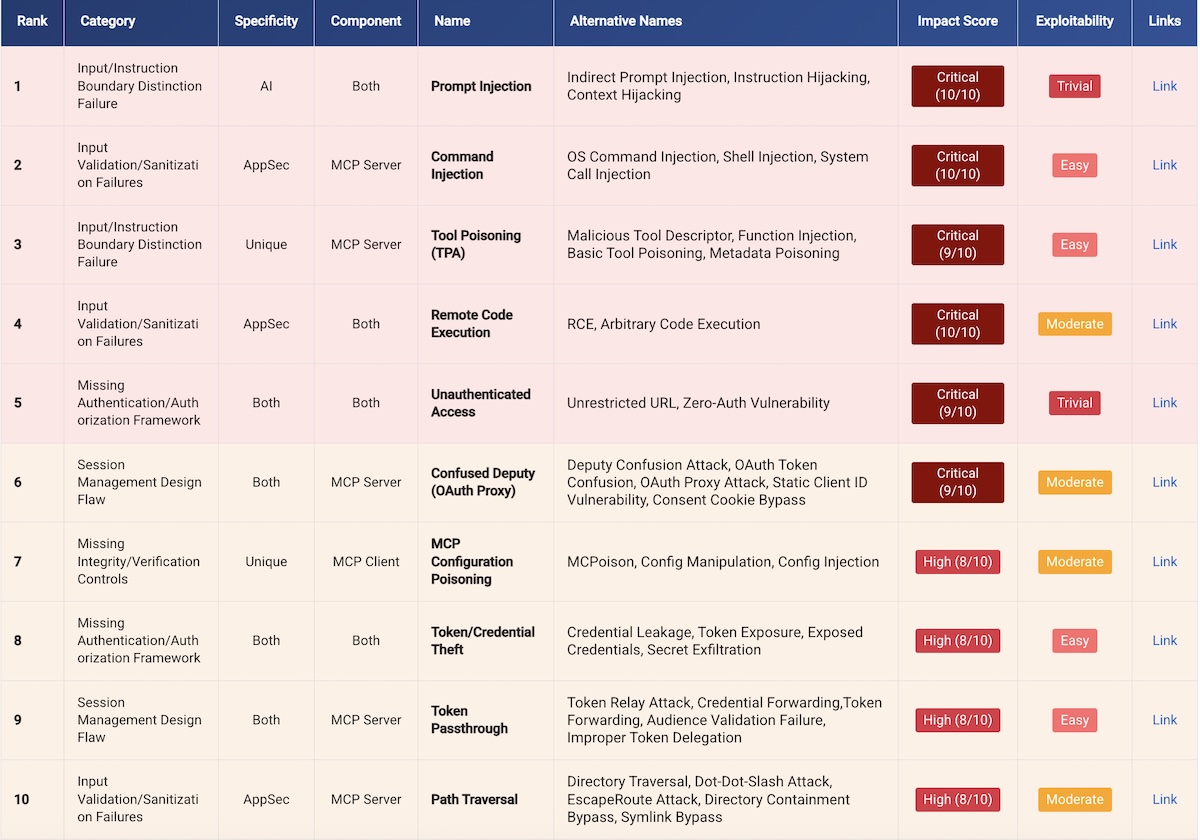
Impact ratings range from critical (full system compromise or remote code execution) to low (information disclosure only), while the level of exploitability ranges from trivial (can be exploited with only basic knowledge and access to a browser) to very complex (a theoretical attack that may require nation-state-level resources).
In the end, the ranking is calculated by the following algorithm: 40% — severity of impact, 30% — ease of exploitation, 20% — prevalence, 10% — remediation complexity. Unsurprisingly, prompt injection took first place — this issue combines critical impact with ease of exploitation. Meanwhile, the MCP Preference Manipulation Attack (MPMA) ranked 24th: the impact is small and exploiting this vulnerability is extremely difficult.
“The document will be updated every month or as new incidents and CVEs emerge that require urgent updates,” Alex Polyakov, co-founder and CTO of Adversa AI, told SecurityWeek.
For now, the links in the document point to the initial descriptions of the vulnerabilities; however, the ranking’s creators intend to replace them with “higher-quality sources as they become available.”
Beyond the list of the threats themselves, the researchers provide a practical guide to protection and mitigation, including “immediate measures,” a “defense-in-depth strategy,” and a “mitigation schedule.”
For example, priority measures include mandatory input validation, since 43% of MCP servers are vulnerable to command injection. “Validate and sanitize ALL incoming data,” the experts write.
The defense strategy is divided into four layers: protocol, application, AI-specific protection, and infrastructure. For example, mandatory TLS for all connections (protocol layer) and parameterized database queries (application layer).
Mitigation measures span a three-month period, starting with “implementing authentication on all exposed endpoints” (immediately) and ending with “redesigning the architecture for a zero-trust model” (by the third month).
