Kaspersky Lab experts have observed a wave of attacks using the Efimer Trojan. The malware spreads via compromised WordPress sites, torrents, and email. Its primary goal is to steal and substitute cryptocurrency wallet addresses, but with additional scripts the threat also brute-forces passwords to WordPress sites and collects databases of email addresses for subsequent spam campaigns.
A distinguishing feature of this campaign is that the Efimer operators target both individuals and corporate users. In the first case, the attackers use torrent files purportedly containing popular movies as bait; in the second, they send phishing emails disguised as claims about the unauthorized use of words or phrases registered by another company.
It’s believed that the first versions of the trojan appeared back in October 2024. At that time, it was distributed only through compromised sites running WordPress. Attackers still use this method, but in the summer of 2025 they also began distributing the malware via email.
Researchers report that Efimer operators look for poorly secured WordPress sites, brute-force their passwords, and post messages on the compromised resources offering to download one of the recently released movies, including a link to a password-protected archive containing a torrent file. The malicious file inside is disguised as the player xmpeg_player.exe.
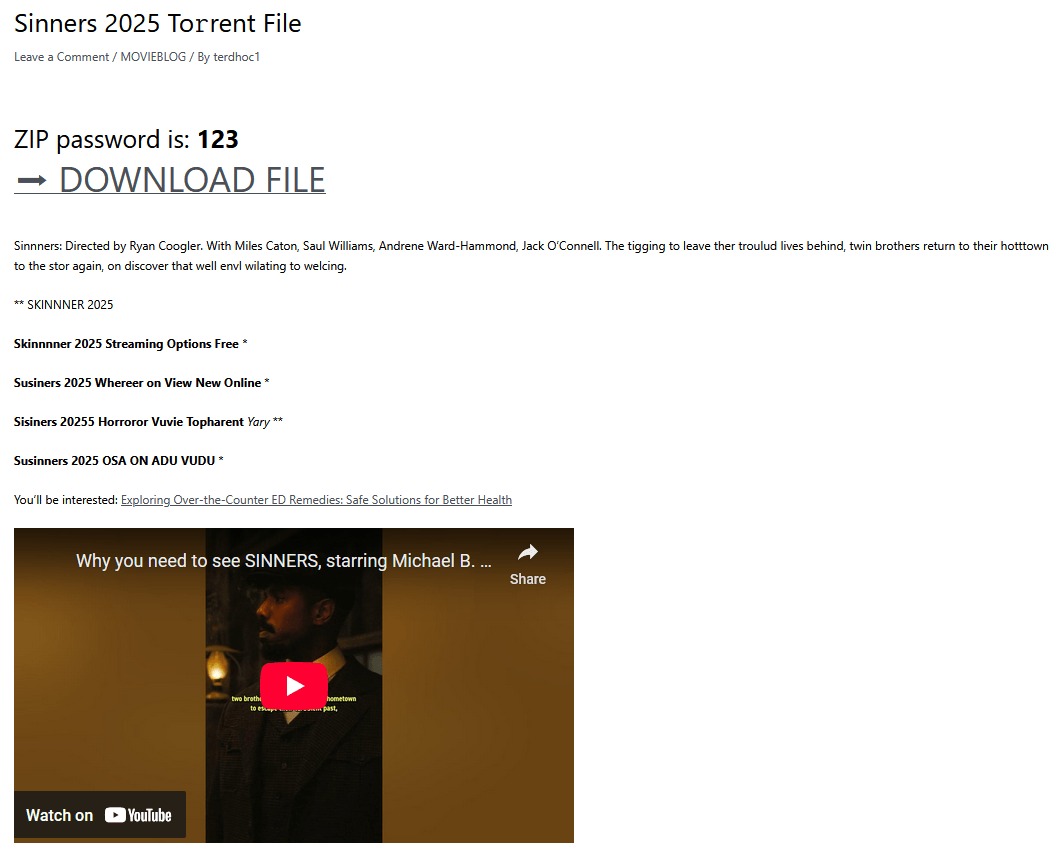
In June 2025, security researchers discovered that the trojan now also spreads through corporate email addresses. Targets can include both small and large businesses.
The phishing emails claim that the lawyers of a certain corporation have reviewed the recipient’s domain and noticed that its name contains words or phrases allegedly already registered by that organization. The lawyers supposedly plan to sue but may refrain if the owner changes the domain name. Moreover, they are even willing to buy this domain.
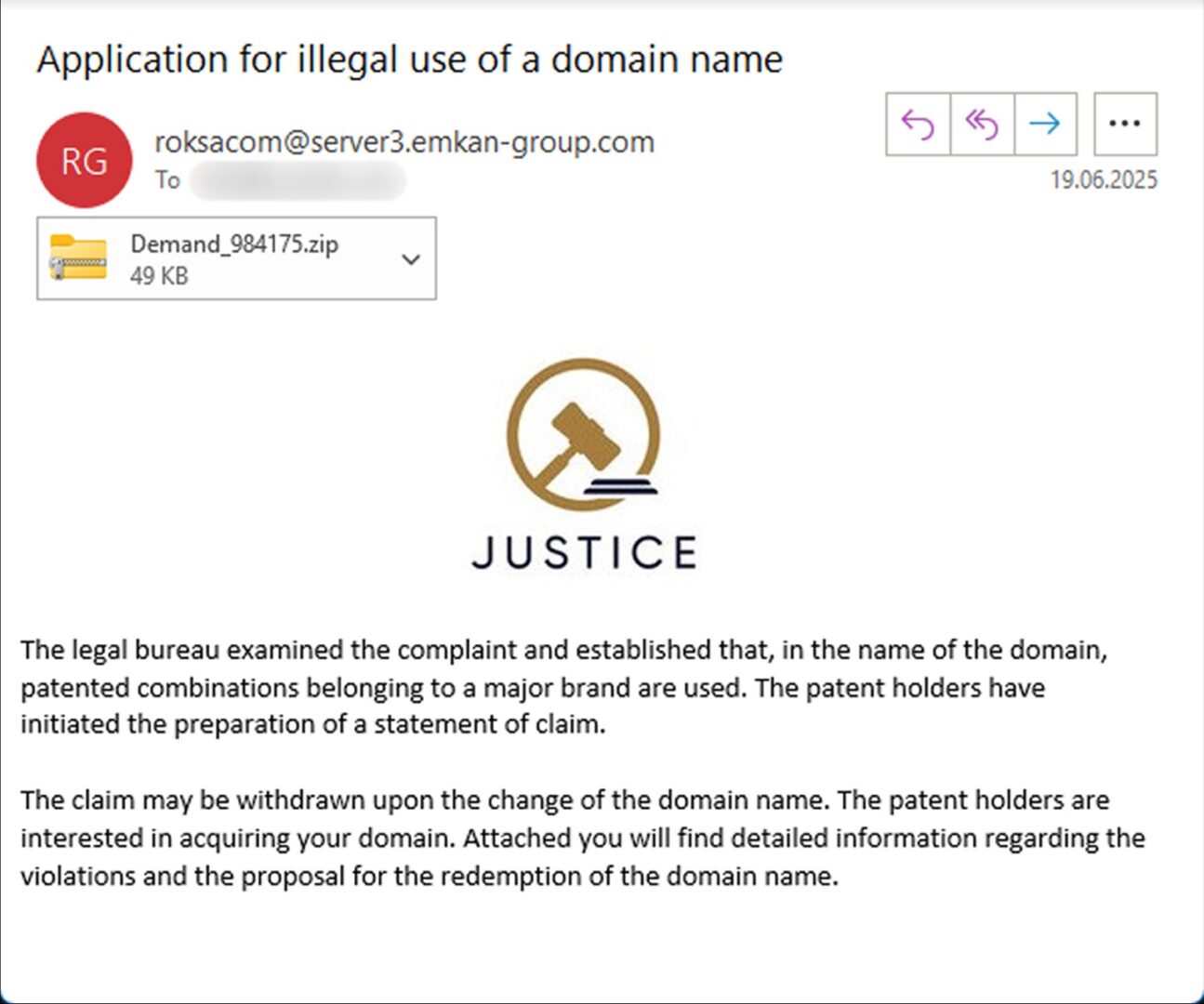
The details — what exactly the violation is and what they’re demanding as ransom — can supposedly be learned by opening the attachment. The email includes a password-protected archive containing a malicious file. If you run it, the computer will be infected with Efimer, and the user will see only an error notification.
On the victim’s machine, Efimer deploys a script called controller.js, which is a ClipBanker-type trojan that replaces cryptocurrency wallet addresses in the clipboard with the attacker’s wallet addresses (the malware also searches the clipboard for strings resembling seed phrases). In addition, it can execute external code received from the command-and-control (C2) server.
It is noted that to communicate with the command-and-control (C2) server, the script initiates the installation of the Tor proxy client on the victim’s computer. The script contains several hardcoded addresses for downloading Tor so that if one of them is blocked, the software can be obtained from other sources.
On some infected machines, a number of additional scripts were found communicating with the same .onion domain. It is assumed that they were installed by the attackers using the eval command to execute a payload delivered from the command-and-control server.
Among these scripts were:
- a file named btdlg.js (MD5: 0f5404aa252f28c61b08390d52b7a054), which brute-forces passwords for WordPress sites, pulling lists of random words from Wikipedia;
- a script named assembly.js (MD5: 100620a913f0e0a538b115dbace78589), which is similar to controller.js and ntdlg.js and is also a ClipBanker, but has a number of differences;
- the Liame email-harvesting script, which collects email addresses from specified sites and sends them to the attackers’ server (the script receives the list of sites as a command from the command-and-control (C2) server).
It is reported that from October 2024 to July 2025, 5,015 users of Kaspersky Lab’s solutions encountered Efimer attacks. The malware is most active in Brazil, where the attacks affected 1,476 users. India, Spain, Russia, Italy, and Germany were also among the most affected countries.
To protect against such threats, experts recommend not downloading torrent files from unfamiliar or dubious sources, verifying email senders, and keeping antivirus definitions up to date.
