29,000 Exchange servers are vulnerable to CVE-2025-53786, which allows attackers to move within Microsoft cloud environments, potentially leading to full domain compromise.
CVE-2025-53786 allows attackers who have already obtained administrative access to on-premises Exchange servers to escalate privileges in the organization’s connected cloud environment by forging or tampering with trusted tokens and API requests. Such an attack leaves virtually no traces, which makes it difficult to detect.
The vulnerability poses a risk to Exchange Server 2016, Exchange Server 2019, and Microsoft Exchange Server Subscription Edition in hybrid configurations.
The vulnerability is tied to changes introduced in April 2025, when Microsoft released guidance and a hotfix for Exchange as part of the Secure Future Initiative. At that time, the company moved to a new architecture with a separate hybrid application that replaces the insecure shared identity previously used by on-premises Exchange servers and Exchange Online.
Later, researchers discovered that this scheme leaves room for dangerous attacks. At the Black Hat conference, experts from Outsider Security demonstrated such a post-exploitation attack.
“Initially, I didn’t consider this a vulnerability, since the protocol used for these attacks was designed with the features discussed in the talk in mind, and it simply lacked important security controls,” says Dirk-Jan Mollema of Outsider Security.
Although Microsoft specialists have not found any signs of the issue being exploited in real-world attacks, the vulnerability has been marked as “Exploitation More Likely” (“High likelihood of exploitation”), meaning the company expects exploits to appear soon.
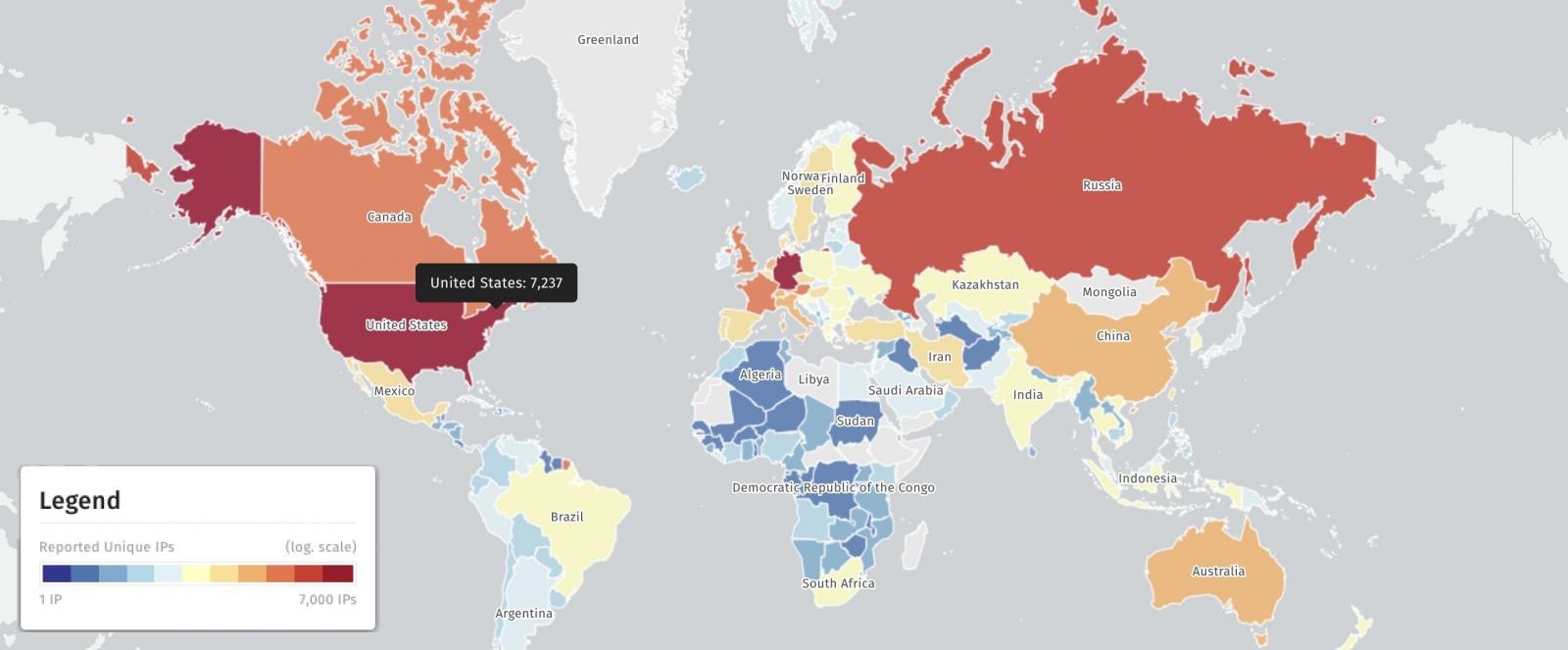
As analysts at Shadowserver warn, 29,098 Exchange servers without patches can be found on the internet. Specifically, more than 7,200 IP addresses were found in the US, over 6,700 in Germany, and more than 2,500 in Russia.
The day after the issue was disclosed, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) issued an emergency directive, mandating that all federal agencies (including the Departments of the Treasury and Energy) urgently address the threat.
In a separate security bulletin, CISA representatives emphasized that failing to remediate CVE-2025-53786 could lead to a “complete compromise of the hybrid cloud and the on-premises domain.”
As Mollema explained, Microsoft Exchange users who have already installed the aforementioned hotfix and followed the company’s April guidance should be protected from the new issue. However, those who have not yet implemented the mitigations remain at risk and should install the hotfix and follow Microsoft’s instructions (1, 2) for deploying the dedicated Exchange Hybrid app.
“In this case, simply applying the patch is not enough; you need to perform additional manual steps to move to a dedicated service principal,” Mollema explained. “The urgency from a security standpoint depends on how important the isolation of on-premises Exchange resources and cloud-hosted resources is to administrators. In the old configuration, the Exchange hybrid system had full access to all resources in Exchange Online and SharePoint.”
The expert also emphasized once again that exploitation of CVE-2025-53786 occurs post-compromise: an attacker must have already compromised the on-premises environment or Exchange servers and have administrator privileges.
