An infosec specialist has discovered that six of the most popular password managers, used by tens of millions of people, are vulnerable to clickjacking, enabling attackers to steal credentials, two-factor authentication codes, and bank card data.
Independent researcher Marek Tóth was the first to report this issue, presenting a talk on the vulnerabilities at the recently held DEF CON 33 hacker conference. His findings were later confirmed by experts from Socket, who helped notify the affected vendors and coordinate the public disclosure of the vulnerabilities.
The researcher tested their attack on specific versions of 1Password, Bitwarden, Enpass, iCloud Passwords, LastPass, and LogMeOnce and found that all browser-based versions can allow sensitive data to leak in certain scenarios.
Attackers can exploit vulnerabilities when victims visit malicious pages or sites that are vulnerable to XSS attacks or cache poisoning. As a result, the attackers can overlay invisible HTML elements on top of the password manager’s interface. The user will believe they are interacting with harmless clickable elements on the page, but in reality they will trigger autofill, which will “leak” their sensitive information to the hackers.
The attack revolves around launching a script on a malicious or compromised site. This script uses transparency settings, overlays, or the pointer-events property to hide the browser password manager’s autofill dropdown menu.
At the same time, the attacker overlays the page with fake, user-annoying elements (for example, cookie banners, pop-up windows, or CAPTCHAs). But clicks on these elements land on hidden password manager controls, causing forms to be filled with sensitive information.
He demonstrated several DOM subtypes and ways to exploit the same bug: direct manipulation of DOM elements’ opacity, manipulation of the root element’s opacity, manipulation of the parent element’s opacity, and partial or full overlay.
The researcher also demonstrated a technique in which the UI follows the mouse cursor, so any user click, wherever it occurs, triggers autofill. Tot emphasized that a malicious script can automatically detect the active password manager in the victim’s browser and then tailor the attack to the specific target in real time.
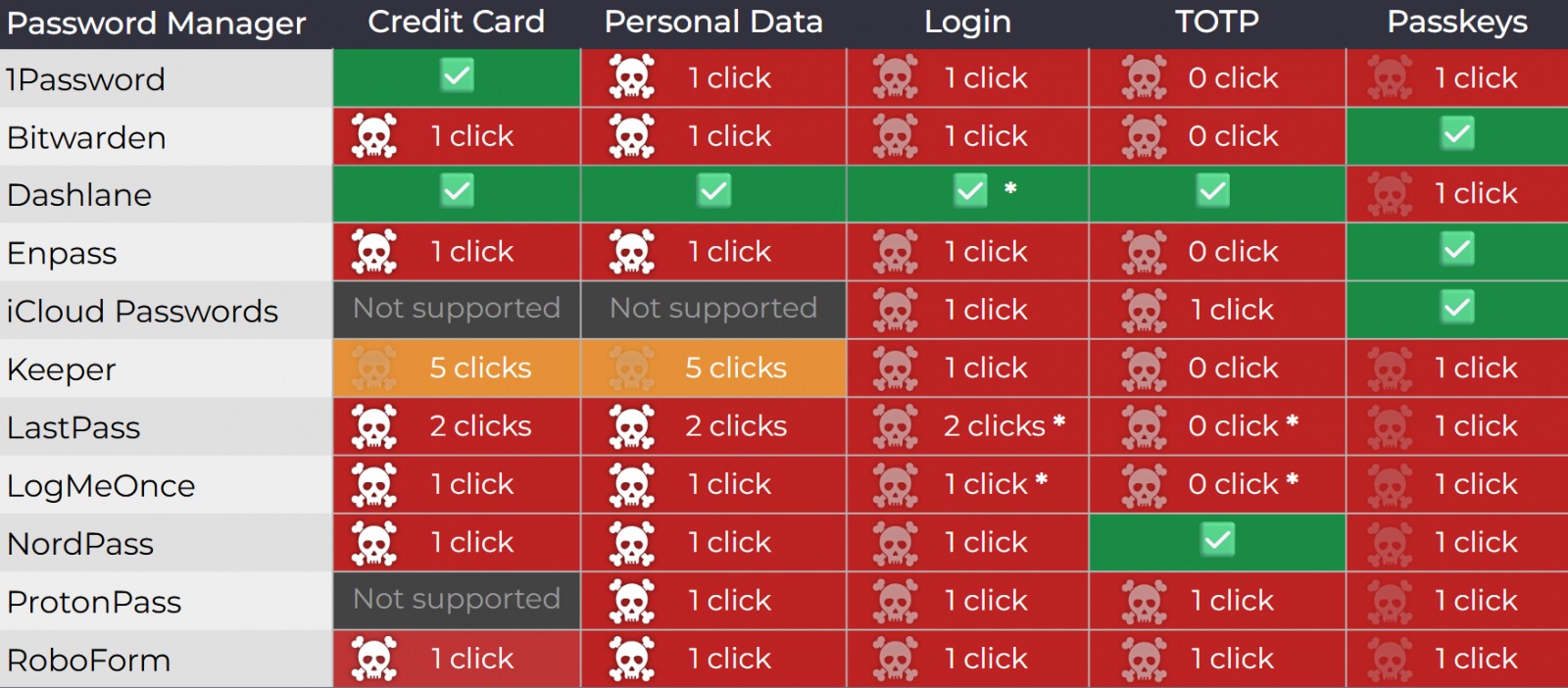
As a result, the researcher tested 11 password managers for susceptibility to clickjacking and found that all of them were vulnerable to at least one attack method.

Although Tot notified all vendors about the issues back in April 2025 and also warned them that public disclosure of the vulnerabilities was planned for DEF CON 33, there was no prompt response.
Last week, Socket experts reached out to the developers once more to notify them again of the need to assign CVE IDs to the issues in the relevant products.
Representatives of 1Password marked the researcher’s report as “informational,” arguing that clickjacking is a general threat that, essentially, users themselves should protect against.
The LastPass developers also found the report “informative,” while Bitwarden acknowledged the issues; although the company did not consider them serious, fixes were included in version 2025.8.0, released last week.
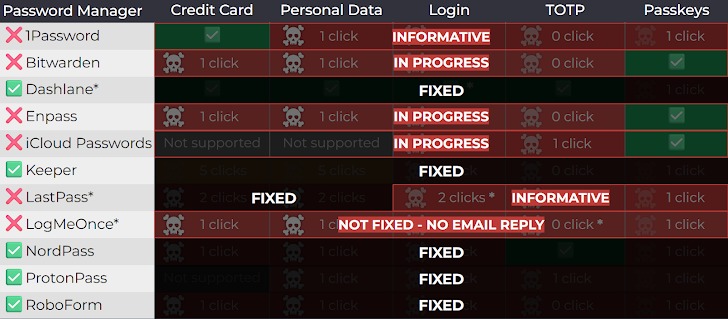
At the same time, neither Totu nor Socket were able to contact the LogMeOnce developers. Only after numerous media reports did LogMeOnce representatives tell Bleeping Computer that they had already prepared a patch.
Currently, the following password managers, which together have about 40 million users, are vulnerable to clickjacking attacks:
- 1Password 8.11.4.27
- Bitwarden 2025.7.0
- Enpass 6.11.6 (a partial fix was implemented in version 6.11.4.2)
- iCloud Passwords 3.1.25
- LastPass 4.146.3
- LogMeOnce 7.12.4
Patches have already been rolled out for the following products: Dashlane (v6.2531.1 released on August 1), NordPass, ProtonPass, RoboForm, and Keeper (17.2.0 released in July). Users are now advised to ensure they have the latest available versions installed.
LastPass representatives told the media that they have already implemented certain protections against clickjacking, including a pop-up notification that appears before autofilling payment card and personal data. The developers also promised to explore further ways to protect users.
1Password reiterated that the clickjacking issue is not unique to the company’s browser extension.
“This is a well-known web attack technique that affects websites and browser extensions in general. Since the underlying issue lies in how browsers render web pages, we believe there is no comprehensive technical fix that browser extensions can implement on their own,” 1Password says, noting that the extension already requires confirmation before autofilling payment information, and that in the next release users will be able to enable similar warnings for other types of data.
To protect against such attacks, Tot and experts at Socket recommend that users disable the autofill feature in password managers altogether and use copy-and-paste only.