Citizen Lab analysts warned that more than 20 VPN apps on the Google Play store have serious security issues that threaten users’ privacy and allow transmitted data to be decrypted. In total, these apps account for 972 million downloads.
Experts report that the VPN providers distributing the problematic apps are clearly linked to each other. At the same time, they claim to be separate companies and use various methods to conceal the true state of affairs.
The Citizen Lab report builds on previous research that identified links between three VPN providers supposedly based in Singapore — Innovative Connecting, Autumn Breeze, and Lemon Clove. All of these companies were previously tied to a Chinese national, and now analysts have uncovered additional overlaps among the apps, as well as connections to other VPN apps and their developers.
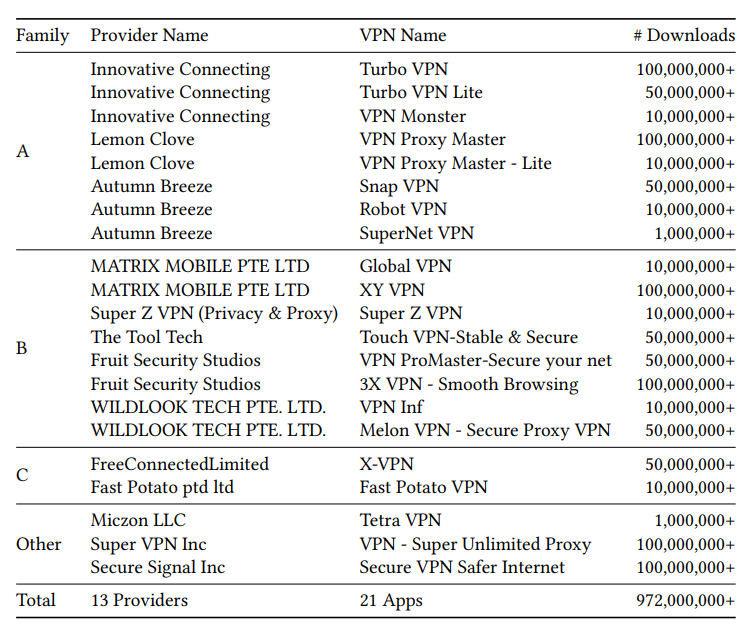
According to the report, eight VPN apps developed by Innovative Connecting, Autumn Breeze, and Lemon Clove share code, dependencies, and hardcoded passwords, which could potentially allow attackers to decrypt all user traffic. Collectively, these apps have over 330 million installs on the Google Play Store.
All three companies, which were previously linked to Qihoo 360 (a Chinese cybersecurity company sanctioned by the U.S. in 2020), offer VPN services and rely on the Shadowsocks protocol, which was originally created to bypass the Great Firewall of China.
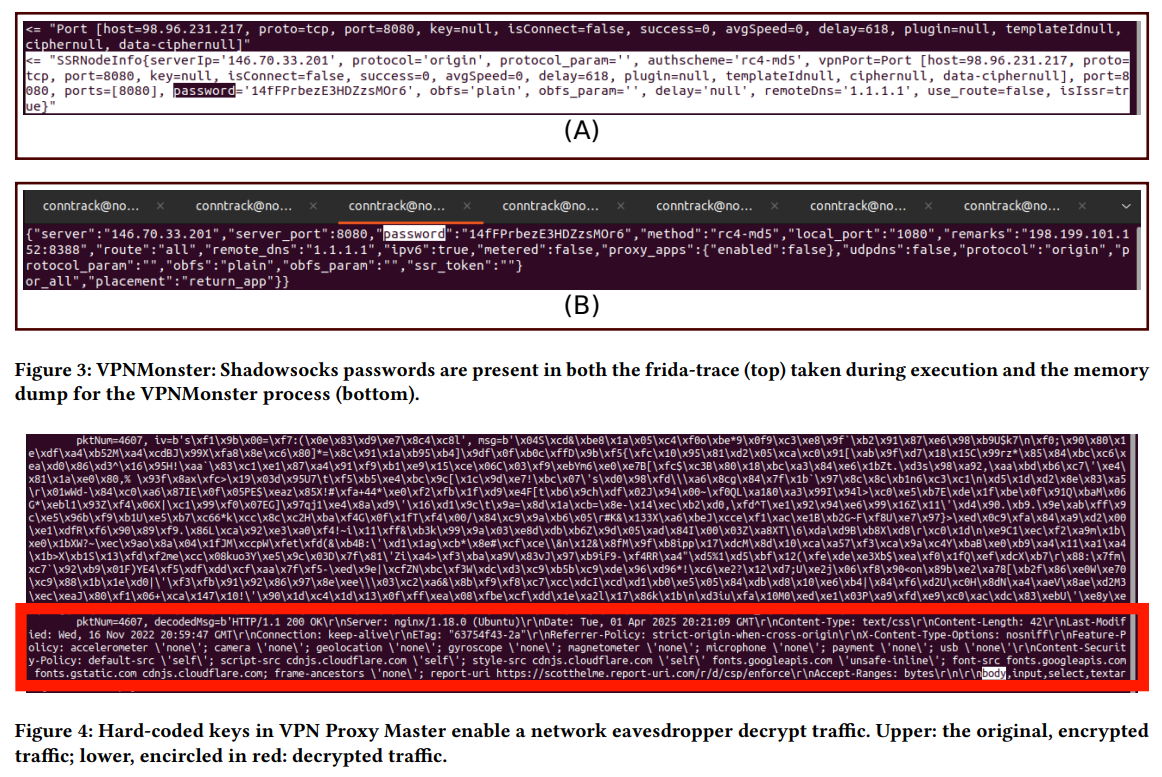
The researchers note that the protocol uses symmetric encryption and is vulnerable to various attacks due to the use of outdated ciphers and hard-coded passwords. In addition, its interaction with the operating system’s connection tracking system allows attackers to take control of victims’ connections.
Eight apps (Turbo VPN, Turbo VPN Lite, VPN Monster, VPN Proxy Master, VPN Proxy Master – Lite, Snap VPN, Robot VPN, and SuperNet VPN) support the IPsec and Shadowsocks protocols, likewise exhibit significant code overlap, and employ various anti-analysis mechanisms to evade automated security checks.
All the applications examined by the researchers were vulnerable to connection-tampering and packet injection attacks. They all secretly collect users’ location data, use weak encryption, and contain the same hardcoded password for the Shadowsocks configuration.
Using this password, Citizen Lab discovered that all three VPN providers offering these apps use a single infrastructure, which further confirms the connection between them.
At the same time, it is noted that another group of providers — Matrix Mobile PTE LTD, ForeRaya Technology Limited, Wildlook Tech PTE LTD, Hong Kong Silence Technology Limited, and Yolo Mobile Technology Limited — may also be linked to the aforementioned trio, given their use of identical protocols, similarities in code, and obfuscation.
Their VPN solutions, with more than 380 million total downloads, also turned out to be vulnerable to man-in-the-middle attacks, contain obfuscated passwords, and connect to the same set of IP addresses.
Two other providers — Fast Potato Pte. Ltd and Free Connected Limited — offer VPN clients that rely on the same proprietary implementation of the protocol.
According to Citizen Lab, the identified security and privacy issues in the studied apps affect users in different ways. For example, they can undermine trust and privacy through the covert collection of location data, and they can also expose people to the risk of traffic interception and modification.
“The issues we identified affect users, service providers, and app stores. VPN users who value their privacy are, at the very least, advised to avoid using Shadowsocks, including apps from these developers, since Shadowsocks was designed not to provide privacy but to circumvent censorship,” Citizen Lab concluded.
