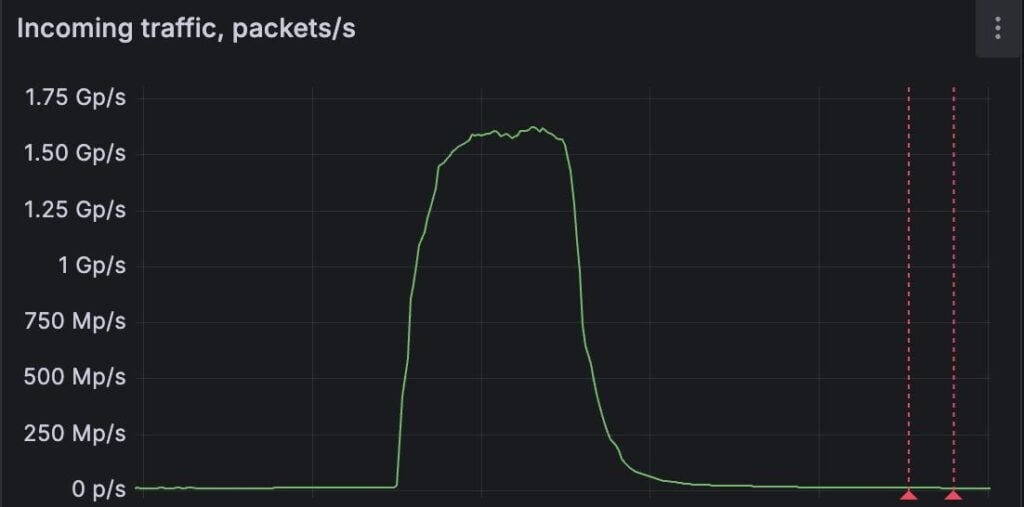
An unnamed European company specializing in DDoS protection became the victim of such an attack itself, with a peak rate of 1.5 billion packets per second (PPS). Experts from FastNetMon, who handled the mitigation, reported that the attack originated from thousands of IoT devices and MikroTik routers.
“The attack peaked at 1.5 billion packets per second—one of the largest packet-rate floods publicly reported,” FastNetMon says. “The malicious traffic primarily consisted of a UDP flood launched from compromised consumer equipment (including IoT devices and routers) distributed across 11,000 unique networks worldwide.”
FastNetMon does not disclose the name of the affected company but reports that it specializes in DDoS filtering. Such services are used to filter out malicious traffic during DDoS attacks, using packet inspection, rate limiting, CAPTCHAs, and anomaly detection.
It was noted that, to counter the attack, measures were taken using the client’s own DDoS-filtering capacity. These measures included deploying access control lists (ACLs) on edge routers that are known for their amplification capabilities.
FastNetMon founder Pavel Odintsov writes that the trend of such large-scale attacks is becoming extremely dangerous. According to him, intervention at the level of internet service providers is required to prevent compromised consumer equipment from being used en masse by hackers.
“This case is notable for the sheer number of distributed sources and the abuse of commodity network devices. Without proactive, provider-level filtering, compromised consumer equipment can be weaponized at scale. The industry must act to implement detection logic at the ISP level to stop outbound attacks before they scale up,” says Odintsov.
It’s worth noting that FastNetMon representatives told The Register that the company recently recorded another incident of nearly the same scale (1.49 billion packets per second), targeting another DDoS filtering service provider in Eastern Europe.
Experts believe that the same botnet was behind this attack. Moreover, in the second case, the targeted organization received an email containing extortion demands.
