In June 2025, researchers discovered a new malicious activity they named Phantom Papa. The attackers sent emails in Russian and English with malicious attachments containing the new Phantom stealer.
This malware is based on the Stealerium stealer’s code and allows its operators to steal passwords, banking and cryptocurrency information, and the contents of browsers and messaging apps. Phantom also features anti-analysis capabilities, autostart, a keylogger, and support for popular obfuscators. For data exfiltration, it can use Telegram, Discord, or SMTP.
According to the researchers, the stealer is distributed through a website whose domain was registered in February 2025. In addition, several other products are featured there: Phantom crypter, Phantom stealer advanced, and Phantom stealer basic.
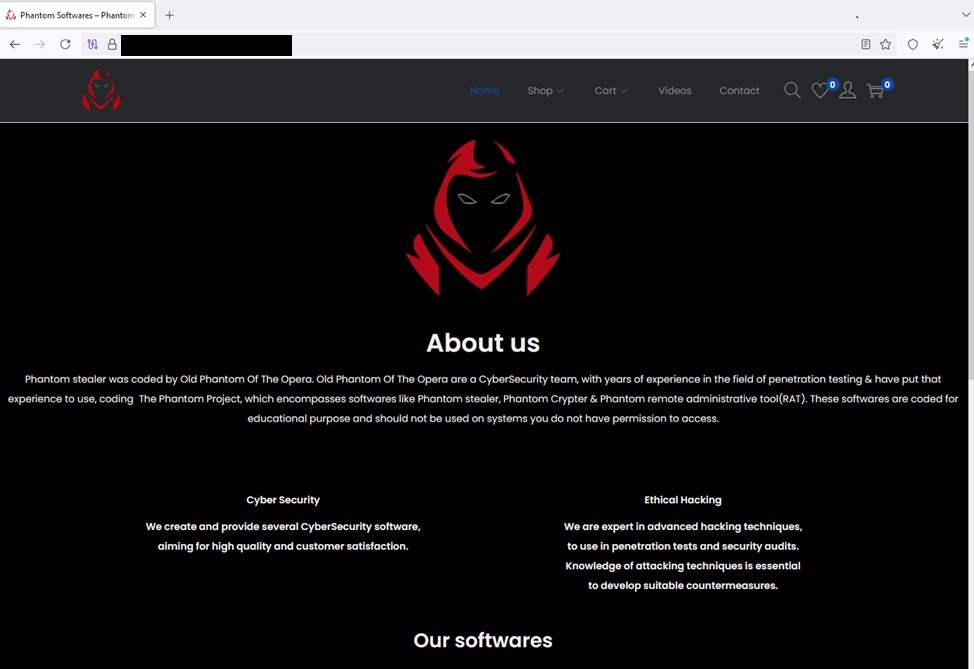
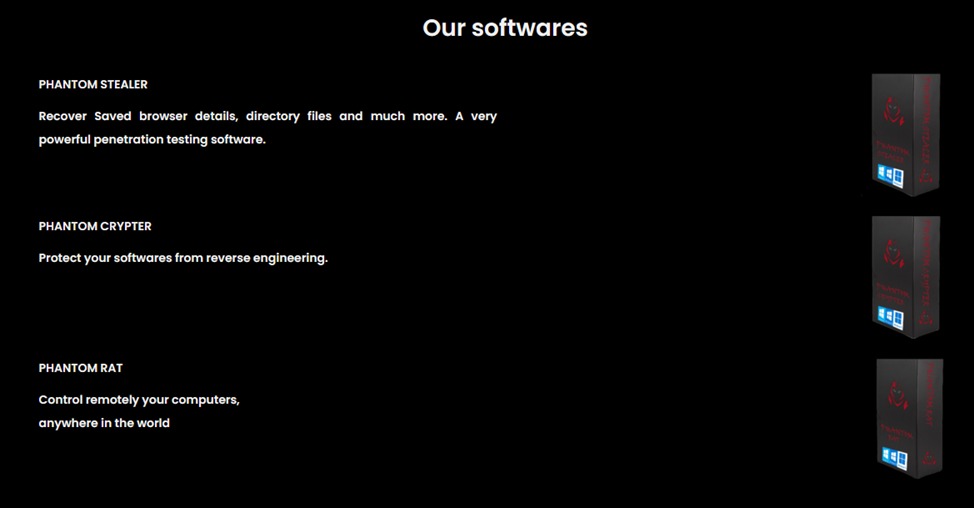
The recipients of the malicious emails containing the stealer were organizations across various sectors of the economy: retail, manufacturing, construction, and IT.
The stealer’s logs contained the IP addresses of devices on which malware samples were executed. The IP addresses of infected devices are linked to 19 countries, including the United States, Russia, the United Kingdom, Romania, Spain, Hungary, Kazakhstan, Azerbaijan, Estonia, Serbia, Switzerland, Singapore, Belarus, and others. Some of these, however, are researchers’ virtual machines.
It was noted that attackers sometimes chose rather risqué subjects for their emails. For example, “See My Nude Pictures and Videos” or “See my nude photos and videos.” But there were also more traditional phishing subjects, such as “Attached copy of payment #06162025.”
At the same time, the emails were clearly translated into Russian from English using machine translation.
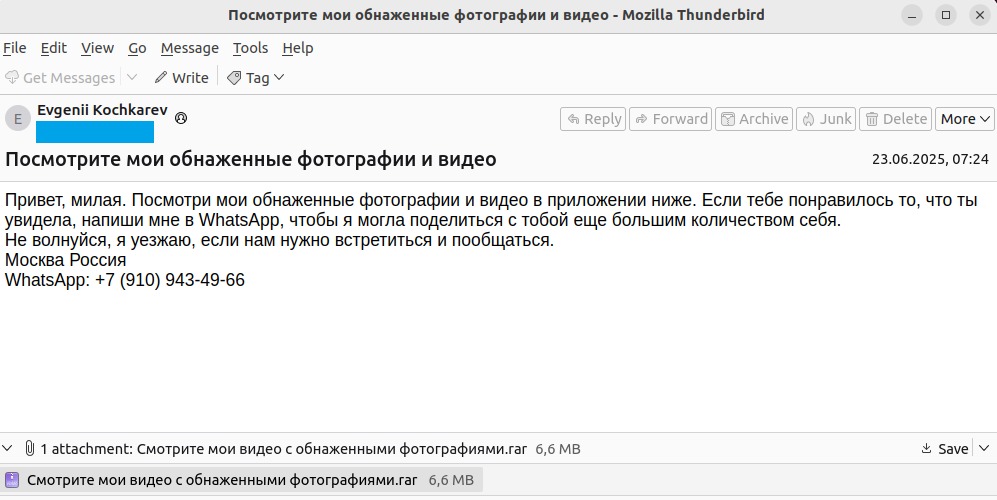
The email attachments were RAR archives used to deliver files with the .img and .iso extensions. Opening such a file mounts the image, inside which an executable file is located.
Upon execution on the victim’s machine, the malware collects the following information: Windows version, PC name, system language, presence of antivirus software, information about the CPU, GPU, RAM, battery, displays, and webcams. In addition, Phantom steals browser cookies, passwords, and payment card data, as well as images and documents.
All the collected information is transmitted by the malware to, for example, the Telegram bot papaobilogs. This bot has been used since at least April 2025, and the researchers named the malicious campaign after it (Phantom Papa).
For persistence in the system, the malware copies itself to %APPDATA%\iWlfdcmimm.exe and %TEMP%\tmpB043.tmp, and also creates a delayed task in the Windows Task Scheduler.
Interestingly, in addition to modules for anti-analysis, keylogging, data theft, and clipboard content theft, Phantom includes a PornDetector module. It monitors user activity and, if it detects one of the substrings “porn,” “sex,” “hentai,” “chaturbate” in the active window, it saves a screenshot to %LOCALAPPDATA%\[0-9a-f]{32}\logs\nsfw\yyyy-MM-dd\HH[.]mm[.]ss\Desktop_yyyyMMdd_HHmmss.jpg and then pauses for 12 seconds.
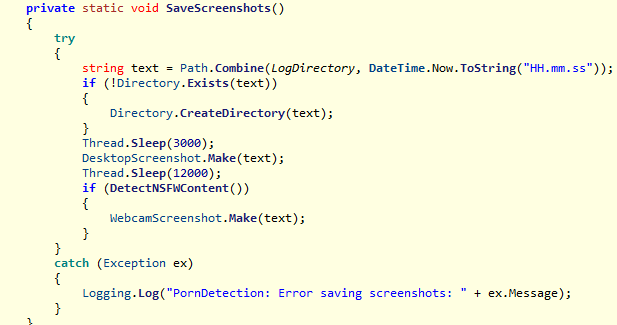
If the window is still active after that, the module captures a snapshot from the webcam and saves it to the file %LOCALAPPDATA%\[0-9a-f]{32}\logs\nsfw\yyyy-MM-dd\HH[.]mm[.]ss\Webcam.jpg.
