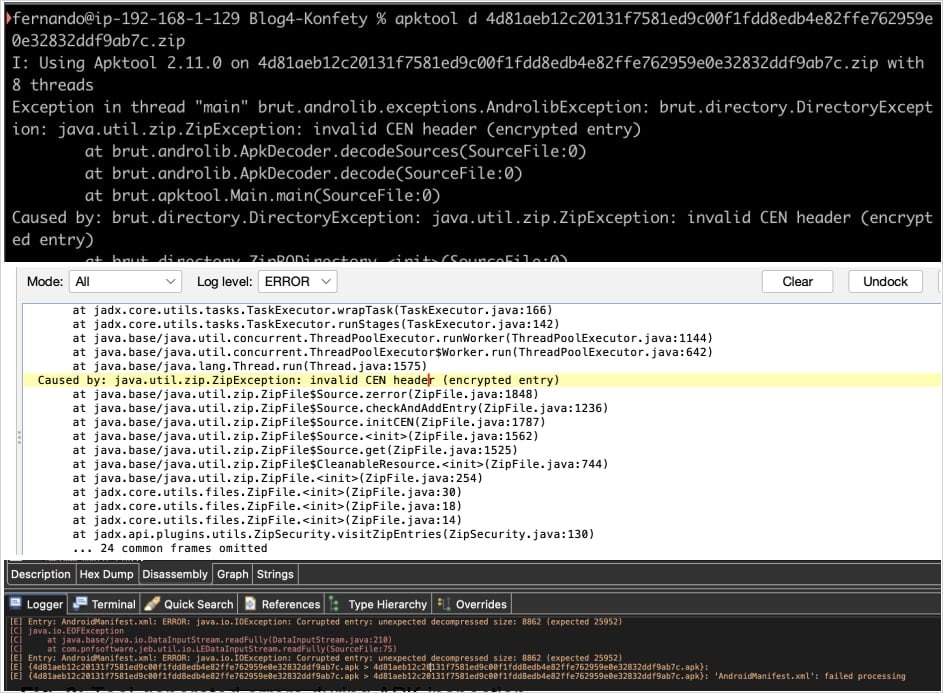
Experts have discovered a new variant of the Android malware Konfety with a distorted ZIP structure and other obfuscation techniques that allow it to evade analysis and detection.
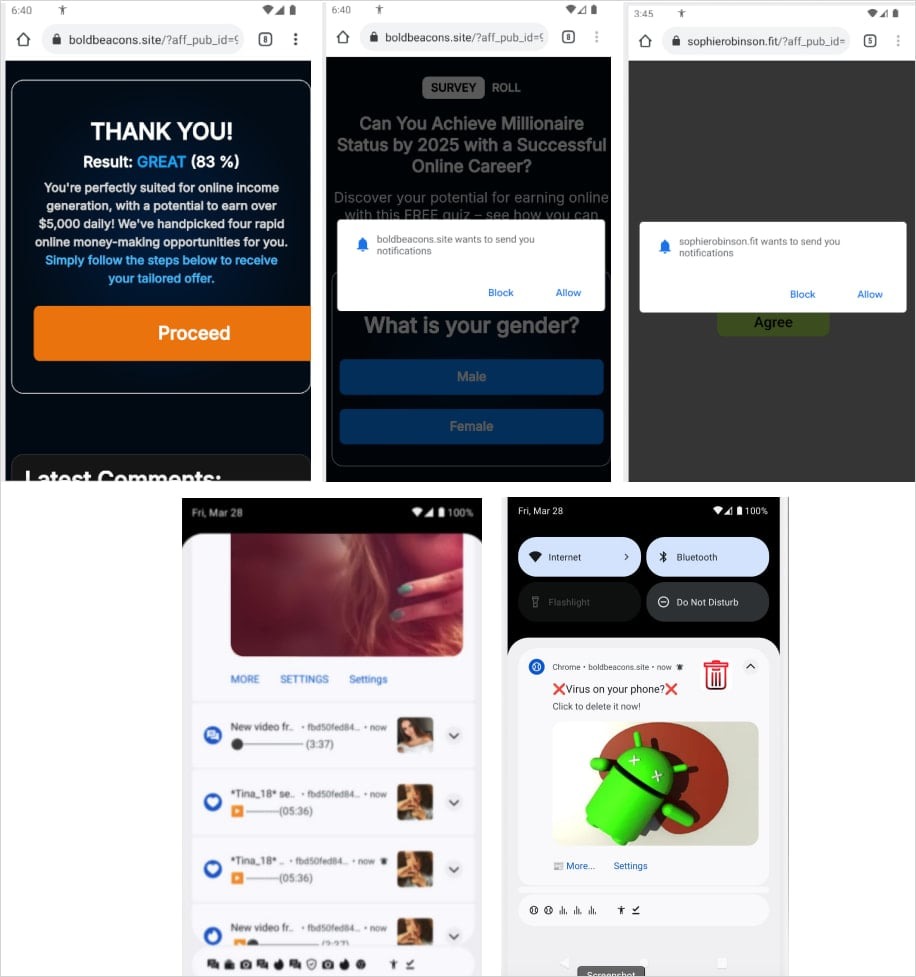
Konfety disguises itself as legitimate applications by mimicking the appearance of harmless products from the Google Play Store, but in reality, it possesses none of the claimed features. Instead, the malware can redirect users to malicious websites, install unwanted applications, and display fake notifications in the browser.
Additionally, the applications display hidden ads using the CaramelAds SDK and collect information about the victim’s device, including data on installed applications and the system, as well as network configuration.
Although Konfety is not a spyware or a full-fledged RAT, the applications contain an encrypted auxiliary DEX file within their APKs. This file is decrypted and loaded at runtime, and it contains hidden services registered in the AndroidManifest. This allows for the dynamic loading of additional modules, which extends the capabilities of the already installed malware and allows for the addition of new, more dangerous features.
Researchers from Zimperium have discovered and analyzed a new variant of Konfety and reported that the malware now uses several methods to conceal its true nature and activity.
One of the methods is disguising as legitimate applications. Attackers copy the name and design of actual applications from Google Play and distribute the malware through third-party app stores.
In general, the developers of Konfety actively promote their malware on third-party platforms, where users often look for “free” versions of paid applications. This usually happens for three reasons: the desire to avoid tracking by Google, using old Android devices, or simply the lack of access to Google services.
Another method of obfuscation is dynamic code loading. The malware hides malicious logic in an encrypted DEX file and activates it only at runtime, which complicates analysis.
Additionally, Konfety employs a rare technique for analysis protection: it intentionally distorts the structure of the APK file to confuse reverse engineering tools and static analysis.
Firstly, in the ZIP header of the APK, the value for the General Purpose Bit Flag is set to “bit 0,” indicating encryption, although the file is not actually encrypted. This results in false password prompts when attempting to open the file, hindering access to its contents.
Secondly, important files within the APK are packed using BZIP (0x000C), which is not supported by popular tools such as APKTool or JADX. This causes errors when attempting to analyze them.
At the same time, the Android OS itself ignores the specified compression method and uses the default processing to avoid errors—allowing the malware to be installed and function on the device.
Once installed on the victim’s device, Konfety hides its icon and name and utilizes what is known as “geofencing,” meaning it behaves differently depending on the user’s region.
It is worth noting that a similar obfuscation method has been encountered before: in April 2024, Kaspersky Lab discussed the SoumniBot malware, which specified a non-existent compression method in the AndroidManifest.xml, faked file sizes, and confused analyzers with excessively long strings in namespaces.