The Lovense smart sex toys platform has been found vulnerable to a bug that allows anyone to discover a user’s email address if their username is known.
Lovense is a manufacturer of interactive sex toys, claiming that its products are used by over 20 million people worldwide.
Vulnerabilities
Independent cybersecurity researchers BobDaHacker, Eva, and Rebane examined the Lovense application, performed reverse engineering, and discovered that knowing the username of a Lovense device owner allows one to ascertain their email address. The issue lies in the fact that usernames of Lovense device owners are often publicly available, and the devices are popular, for example, among webcam models.
During their research conducted in March 2025, experts identified two vulnerabilities at once. Currently, only one of these has been addressed — a critical vulnerability that allowed the interception of other people’s accounts. However, the issue that permits the discovery of users’ email addresses remains unresolved.
The vulnerability is related to how the Lovense chat system, based on XMPP (used for communication between users), interacts with the server-side of the platform.
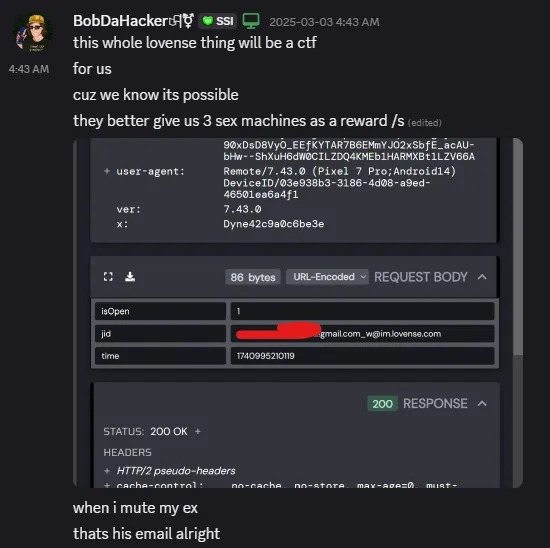
“It all started when I used the Lovense app and muted someone. That’s it. I just used mute,” writes BobDaHacker. “After that, I saw the API response and thought… wait, is that an email address? Why is it here? Digging deeper, I realized that you can turn any username into an email address.”
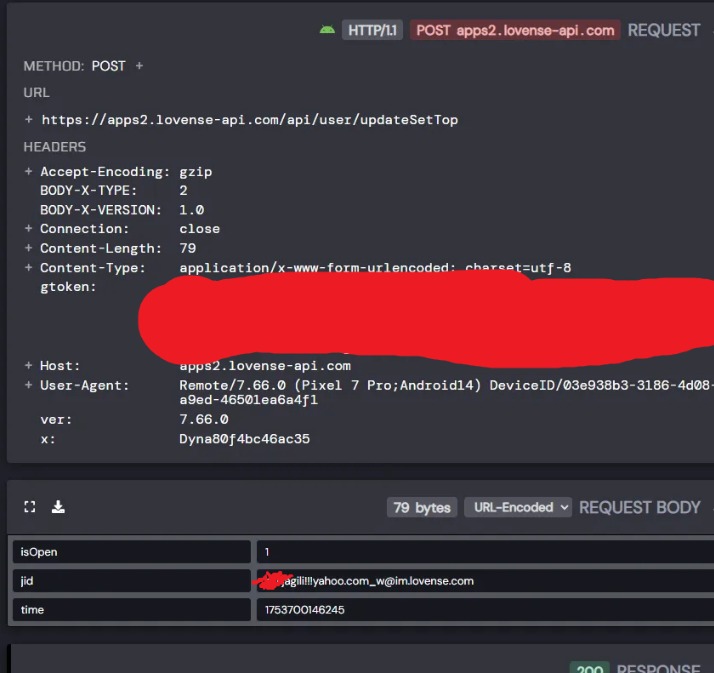
To exploit the vulnerability, an attacker needs to make a POST request to the API endpoint /api/wear/genGtoken with their own credentials, and as a result, they will receive a gtoken (authentication token) and AES-CBC encryption keys.
Then an attacker can select any known Lovense username and encrypt it using the obtained keys. This encrypted payload needs to be sent to the API endpoint /app/ajaxCheckEmailOrUserIdRegisted?email={encrypted_username}. As a result, the server will respond with data containing a fake email address, which can be converted into a fake Jabber ID (JID) used by the Lovense XMPP server.
After this, you need to add the fake JID to your XMPP contacts list and send a subscription request via XMPP (similar to a friend request). Afterward, the attacker can update the contact list, which will include both the fake JID and the real one associated with the victim’s account.
The root of the problem is that the actual JID is formed based on the user’s real email address in the format username!!!domain.com_w@im.lovense.com. This makes it easy to discover the victim’s real email address.
Researchers note that the attack can be automated, and if a script is used, extracting one user’s email address takes less than a second. They also specify that for the successful exploitation of the bug, the victim does not need to accept a “friend request” from the attacker.
Additionally, BobDaHacker writes that the FanBerry extension, developed by Lovense, can be used to mass-collect usernames, as many webcam models use the same usernames across different platforms. According to him, usernames can also be found on forums and sites related to Lovense, such as lovenselife[.]com.
As for the already fixed critical vulnerability that allowed for the complete takeover of another user’s account, an attacker only needed to know the victim’s email address to generate authentication tokens without the need to enter a password. Using these tokens, the attacker could impersonate the user on Lovense platforms, including Lovense Connect, StreamMaster, and Cam101. Moreover, the tokens also worked for administrator accounts.
Although Lovense has resolved this issue by discontinuing the use of tokens in their API, researchers note that gtokens can still be generated without a password.
Issues with Patches
Specialists notified Lovense about both issues back on March 26, 2025. In April, after the information about the bugs was also submitted to HackerOne, the manufacturer reported that they were already aware of the issue with email addresses and that it would be fixed in one of the upcoming versions.
Initially, the company attempted to downplay the significance of the vulnerability that could lead to a complete account takeover. It was only after being informed that the bug could provide full access to an administrator account that Lovense classified the vulnerability as critical.
As a result, the researchers received $3,000 for discovering the aforementioned issues through the bug bounty program.
It is worth noting that in July 2025, Lovense only fixed the critical bug related to account takeovers, and stated that it would take about 14 months to resolve the second issue concerning email addresses, as it would break compatibility with older versions of the application.
“We have developed a comprehensive remediation plan, which will take about ten months to implement, and at least another four months will be needed for the full deployment of a complete solution,” Lovense told researchers. “We also considered a faster fix that would take one month. However, this would require an immediate update for all users, which would disrupt support for legacy versions. We decided to reject this approach in favor of a more stable and user-friendly solution.”
In their report, experts criticized this response, stating that the company had repeatedly assured them that the issues had been resolved, although this was not the case.
“Your users deserve better. Stop prioritizing the support of legacy applications over security. Address the issues genuinely. And test your patches before claiming they work,” writes BobDaHacker.
As a result, representatives of Lovense stated that on July 3, 2025, the company implemented a proxy feature, previously suggested by researchers to protect against potential attacks. However, even after this forced application update, the vulnerability was not eliminated.
As noted by Bleeping Computer, after the public disclosure of the vulnerabilities, other cybersecurity specialists (with nicknames Krissy and SkeletalDemise) claimed that they had identified the same account takeover bug back in 2023 and notified the manufacturer via HackerOne.
However, at that time, Lovense representatives marked the vulnerability as fixed (although it was not), downgraded its severity from high to medium, and paid the researchers only $350.
Moreover, another API (/api/getUserNameByEmailV2) was discovered at that time, which also allowed converting a username into an email address (and vice versa), without needing to use XMPP. According to researchers, this API was fixed and became unavailable following the disclosure of the issue, yet the company has not commented on this in any way.
The representatives of Lovense have now informed Bleeping Computer journalists that the company has already released an update addressing both issues described by BobDaHacker.
“It is expected that a full update will be distributed to all users within the next week. Once all users have upgraded to the new version and we disable the old versions [of the app], the issue will be completely resolved,” assured the company.
However, along with this, the press service claims that Lovense fixed the vulnerability revealing email addresses back in late June. This statement contradicts the information provided to journalists by BobDaHacker. The fact is, just two days ago, the researcher demonstrated the vulnerability in practice and effortlessly obtained the email address from a test account of journalists.
It is worth noting that this is by no means the first time serious vulnerabilities and defects have been discovered in Lovense products. For instance, back in 2017, users discovered that the Lovense app recorded everything happening during the use of the intimate gadget, saving the resulting audio files in 3gp format in the local directory of a smartphone or tablet.
The issue arose because during installation, the application requested access to the device’s microphone and camera, and these permissions were allegedly required for the built-in chat function and the use of voice commands.
In the end, the developers described the recording of everything the microphone hears on the device where the application is installed as a “minor bug,” rather than an officially intended feature.
In 2021, experts from ESET warned about multiple security issues with sex toys. The report included Lovense gadgets, whose tokens for connection could be guessed using simple brute force methods.