Last week, the cybersecurity company Huntress published research based on the fact that an attacker had installed a trial version of its product. However, the company ended up facing criticism, as many raised concerns about the extent of Huntress’s access to customer systems, even when they had installed only the free trial version of the EDR tool.
In their report, the researchers said they had a “rare opportunity” to study a hacker’s operations from the inside, because the attacker had the ill-advised idea to install a trial version of the company’s EDR product. Moreover, the hacker was also interested in other security solutions and used Malwarebytes’ premium browser extension in an effort to conceal their online activity.
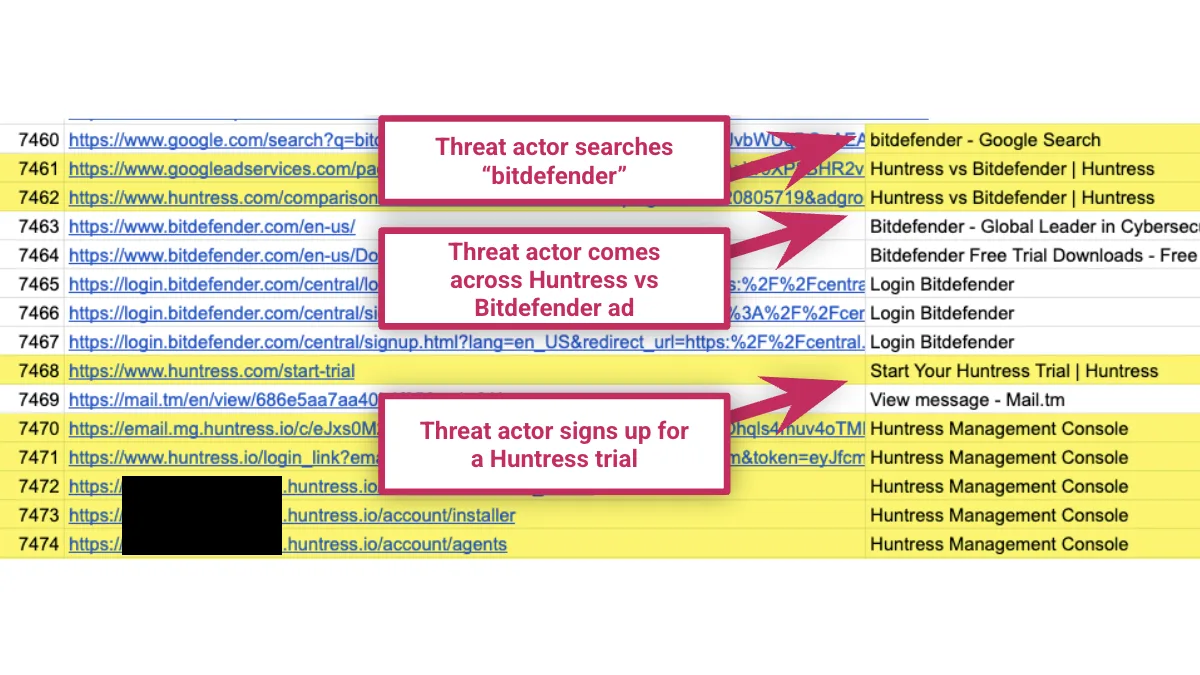
Huntress logs showed that it all started when the attacker performed a Google search for “Bitdefender,” but ended up downloading the trial version of Huntress EDR via a sponsored Google link that appeared at the top of the search results.
After that, Huntress researchers were able to monitor all of the attacker’s activity, which they did for three months.
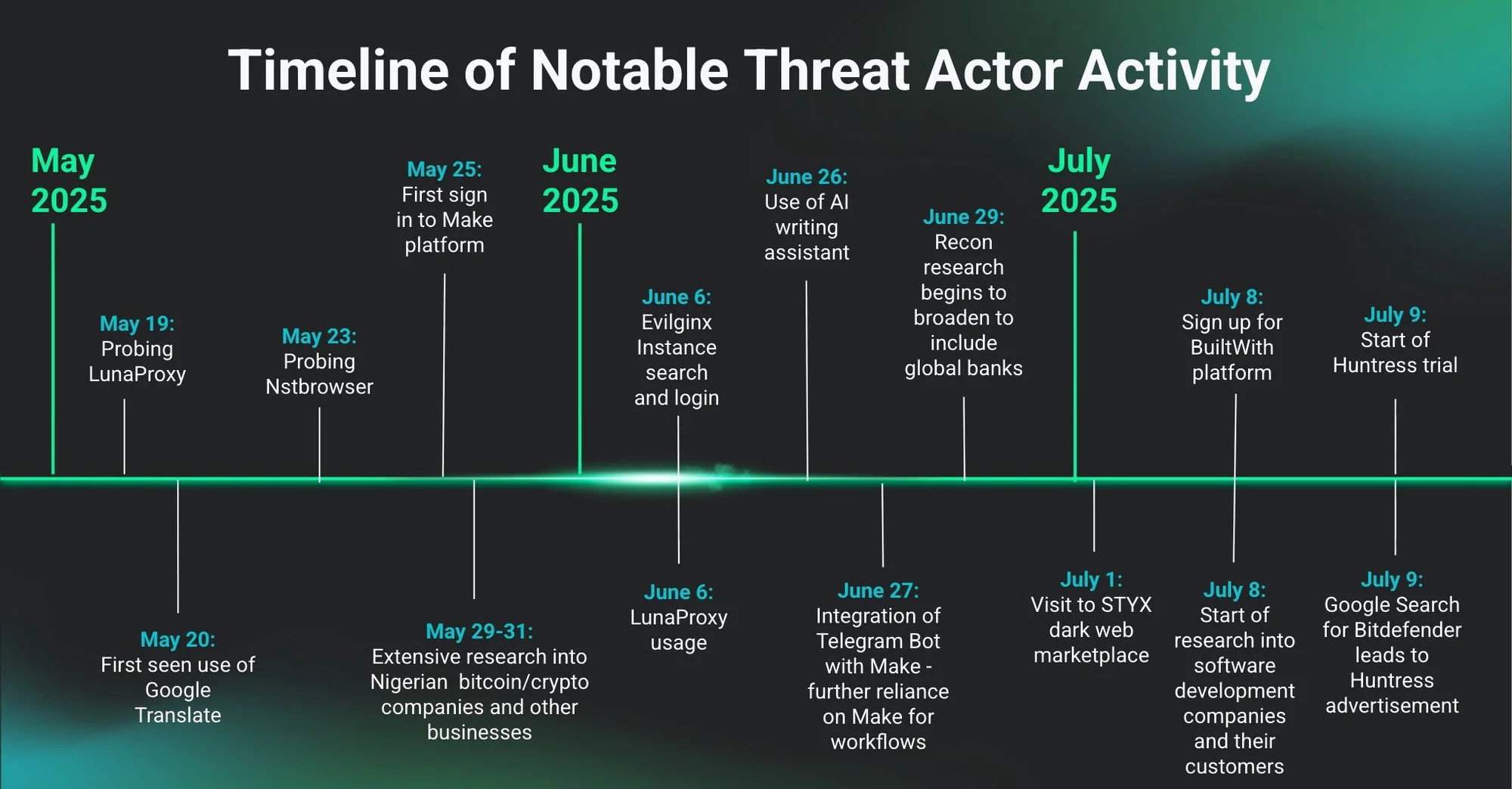
“We determined this was a threat actor rather than a legitimate user based on several telling signs. A red flag was that the unique computer name used by the attacker matched a name we had previously been tracking across multiple incidents (before they installed our agent). Further investigation uncovered additional clues, including the attacker’s browser history, which appeared to show active attempts to target organizations, craft phishing messages, find Evilginx instances and access them, and more. We also suspect that the computer on which the Huntress solution was installed was being used as a jump box by multiple threat actors, though we don’t have conclusive evidence at this time,” the researchers wrote.
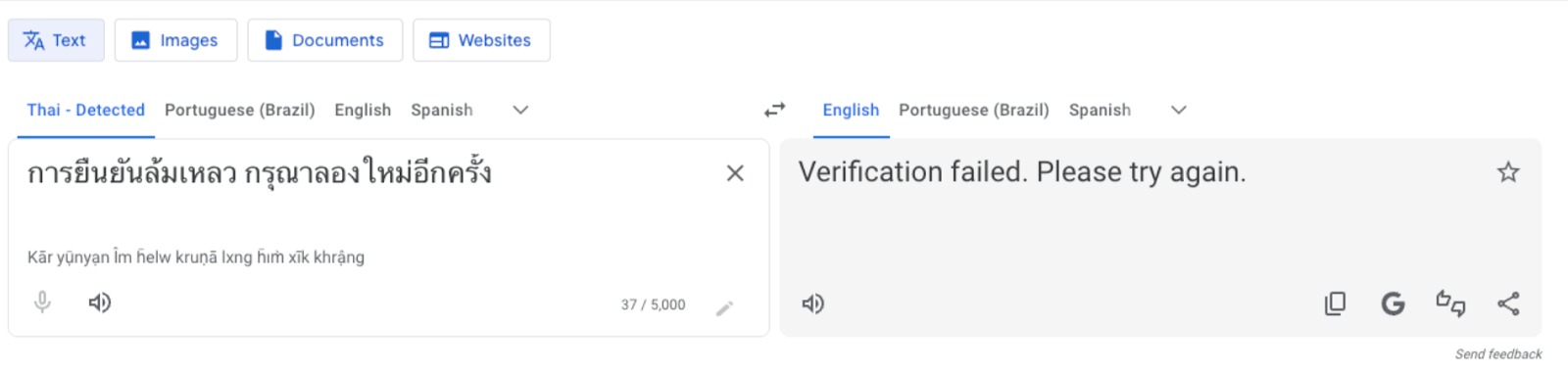
Looking at the extensive use of Google Translate, the researchers concluded that the attacker apparently understood Thai, Spanish, and Portuguese. The hacker regularly used the translator to convert messages into English and then likely used the resulting texts in phishing campaigns aimed at collecting banking credentials.
However, many found the Huntress experts’ report quite alarming. While some cybersecurity specialists and users agreed with the vendor’s assessment and found it amusing that a hacker had installed a trial version of the EDR tool, others began expressing concerns about the level of access the company has to customers’ systems.
“This gave defenders unique insights, but it also raised a real question: should a private company have the right to track an adversary in this way, or was it obligated to notify authorities as soon as it shifted from incident response to intelligence gathering?” — wrote Horizon3.ai CEO Snehal Antani.
Other experts called what happened “a complete violation of privacy” on the part of the manufacturer.
In the end, Huntress representatives had to update their report by adding an official statement to the original publication. In it, the company addresses the community’s questions about the ethics of what happened, and also explains how its product works and what level of access its employees actually have to the attacker’s system (and to customer systems in general).
The company stated that the research methodology mirrored that used by other EDR vendors, and that such tools will always have extensive access to data on host systems.
“We first encountered the host mentioned in this publication because we responded to numerous alerts related to malware execution on it. As part of this process, our SOC team carefully reviews the signals and collects artifacts related to the host’s EDR telemetry. Only upon further examination of this telemetry did we discover signals indicating malicious behavior. In addition, by that point we had found that the unique machine name used by this individual matched a name we had been tracking across several incidents,” the company explains.
It is also emphasized that the Huntress agent does not have capabilities such as remote screen access or taking screenshots. All examples from the attacker’s browser history mentioned in the article “were obtained by examining forensic logs and artifacts related to alerts of malicious behavior observed on the endpoint.” And the images in the article were simply recreated “inspired by” the hacker’s actions.
“When deciding what information to publish about this investigation, we carefully weighed several factors, including strict adherence to our confidentiality obligations and the provision of EDR telemetry that captures precisely those threats and behavioral patterns that can help defenders. Overall, this investigation reflects what we do best: transparency, education, and fighting hackers,” the Huntress team sums up.