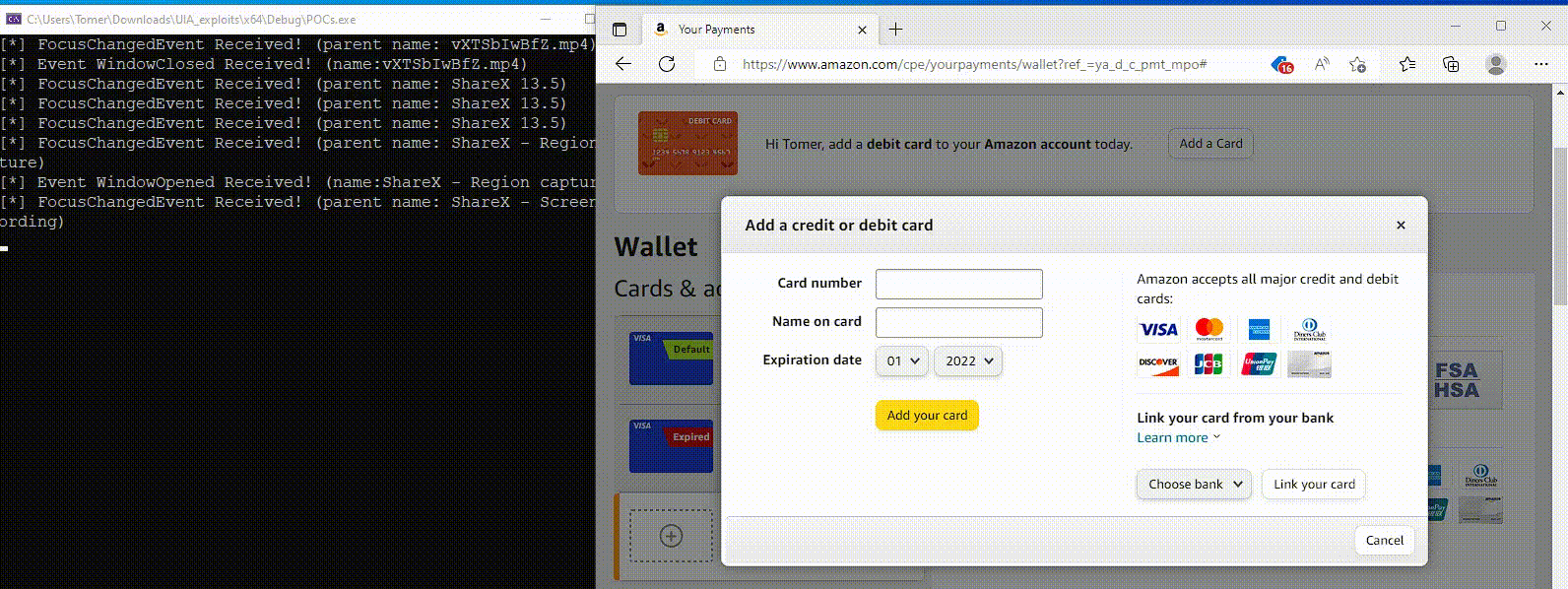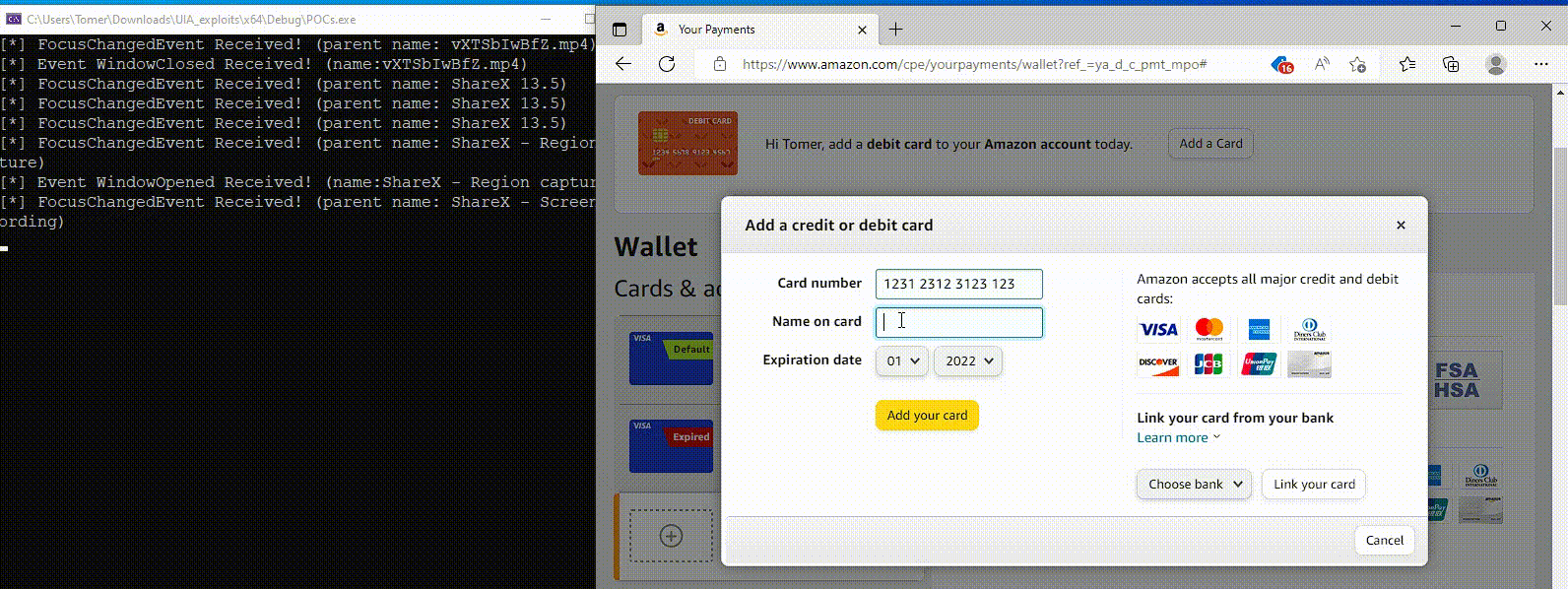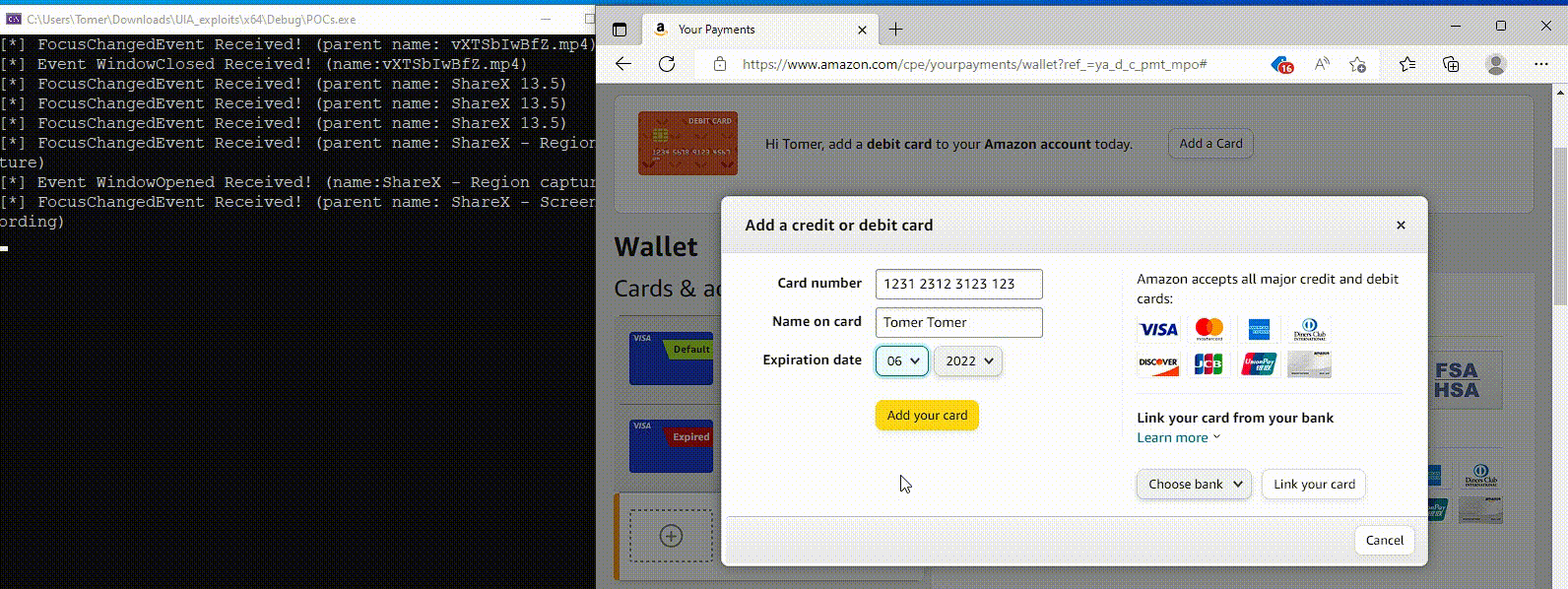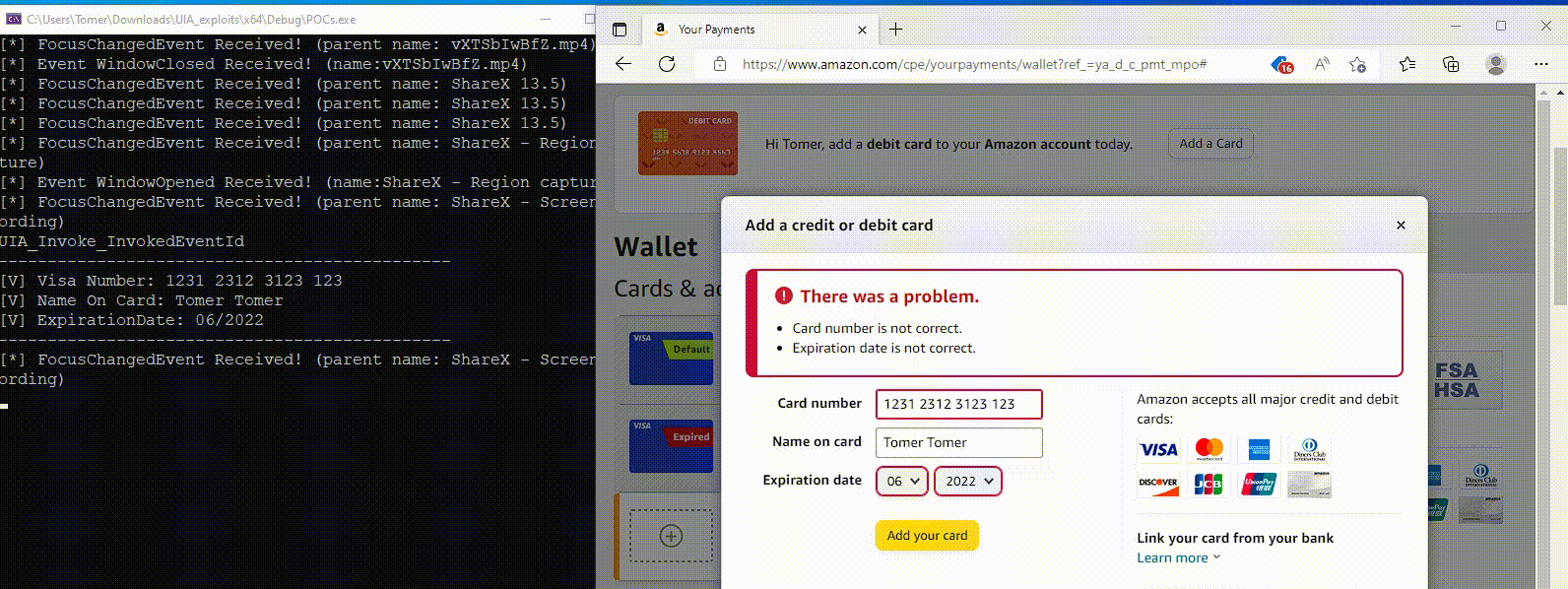
The new variant of the banking Trojan Coyote exploits accessibility features in Windows, specifically the Microsoft UI Automation framework. In this way, the malware detects banking and cryptocurrency exchange websites visited by the user and steals their credentials.
Microsoft UIA is a framework designed to allow assistive technologies to interact with elements of Windows application interfaces: read their properties, control them, and monitor changes. Applications present their structure as a UI Automation tree, and the UIA API allows browsing this tree, obtaining data about interface elements, and interacting with them by emulating user actions. All of this is intended to enable people with disabilities to fully utilize all the capabilities of their devices.
As early as December 2024, specialists from Akamai warned that UIA could be used for credential theft, emphasizing that this technique would allow bypassing EDR protection in any version of Windows starting from XP.
Now Akamai reported that their predictions are coming true: since February 2025, experts have observed real attacks using this technique, and it is the first known case where malware exploits Microsoft UIA capabilities for data theft.
The banking trojan Coyote has been active since February 2024. This malware aims to steal credentials from 75 banking and cryptocurrency applications, primarily targeting users in Brazil. When the malware was first discovered, it used keylogging and phishing overlays, but since then, Coyote has undergone significant changes.
According to researchers, the new version of Coyote continues to steal data using traditional methods, but also has added functions in its malware code to exploit UIA, which are used when a user opens banking or cryptocurrency services in a browser.
If Coyote cannot identify the object by the window title, it uses UIA to extract the web address from the browser’s UI elements (tabs or address bar). It then compares the obtained result with a hardcoded list of 75 targeted services.
Among the banks and exchanges that Coyote targets using this method are: Banco do Brasil, CaixaBank, Banco Bradesco, Santander, Original bank, Sicredi, Banco do Nordeste, Expanse, as well as Binance, Electrum, Bitcoin, Foxbit, and others.
Although in this case the misuse of UIA is limited to the reconnaissance phase, Akamai specialists have demonstrated that UIA can also be used for the actual theft of credentials from targeted sites.
“Parsing nested elements of another application without UIA is a non-trivial task,” researchers say. “To effectively read the contents of nested elements of another application, a developer must have a good understanding of how the specific target application is structured. Coyote can perform checks regardless of whether the malware is online or offline. This increases the chances of successfully identifying a bank or cryptocurrency exchange to steal credentials.”
Experts remind us that on Android, the issue of abusing Accessibility Services is very acute and has long become widespread.