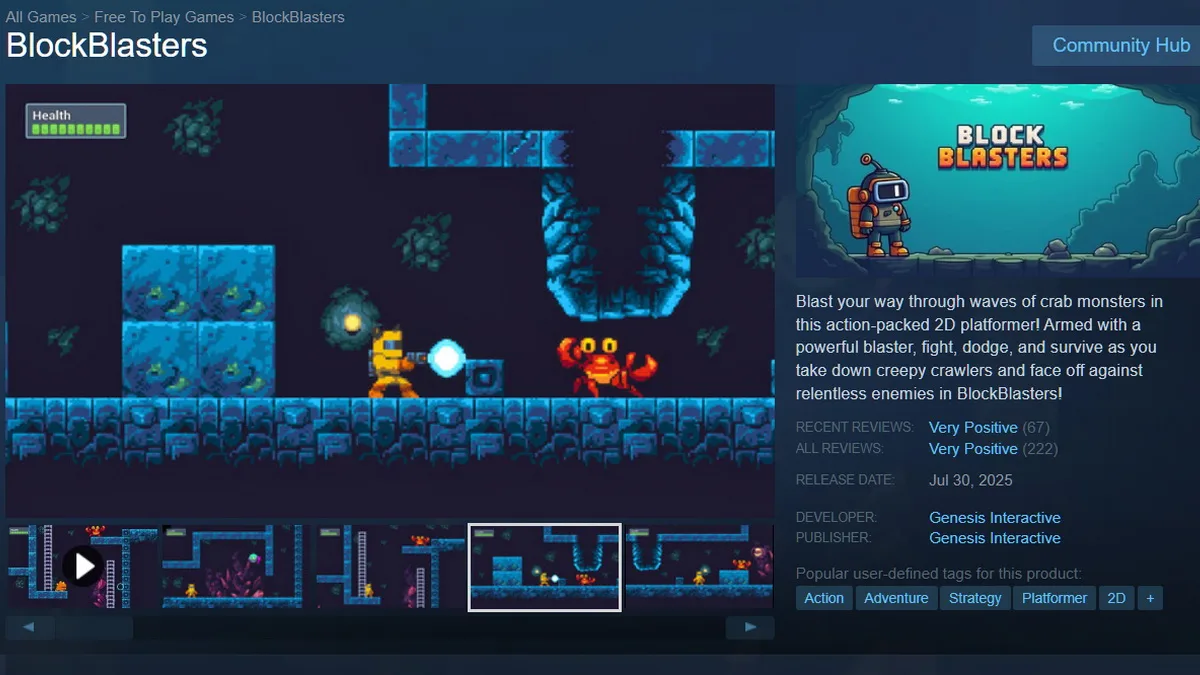
Another malicious game has been discovered on Steam — BlockBlasters. Attention to the issue was drawn by the case of streamer Raivo Plavnieks, known as RastalandTV. He was trying to raise money for stage-four cancer treatment, but after installing BlockBlasters he lost $32,000 that he had received in donations. Further investigation showed that hundreds of users were affected by the game.
BlockBlasters, published by developer Genesis Interactive, was a 2D platformer that was available on Steam for nearly two months (from July 30 to September 21, 2025). According to SteamDB, the game was safe until August 30, and only after that date was a malicious component for stealing cryptocurrency added to it.
At present, BlockBlasters has already been removed from Steam (an archived version can be seen here).
The malware embedded in the game was discovered live on stream. The aforementioned RastalandTV was streaming to raise funds for treatment of stage IV sarcoma. Someone in the chat advised Plavnieks to install BlockBlasters, promising financial support if he showed the game on stream. However, after installing the game, $32,000 raised through commissions and donated to the streamer for cancer treatment were stolen.
RastalandTV has a crowdfunding campaign on GoFundMe, which is currently 58% funded. However, after the theft of donations, the incident drew a lot of attention, and some members of the crypto community offered to cover the losses. In particular, crypto influencer Alex Becker reported that he has already transferred $32,500 to Plavnieks into a secure wallet.
An examination of BlockBlasters’ activity showed that RastalandTV was not the only victim. According to well-known blockchain analyst ZachXBT, the perpetrators behind this game stole at least $150,000 from 261 Steam users.
Researchers from the VXUnderground team were also tracking this attack. According to their data, there were even more victims — 478 people. The specialists published a list of usernames and urged account owners to reset their passwords as soon as possible.
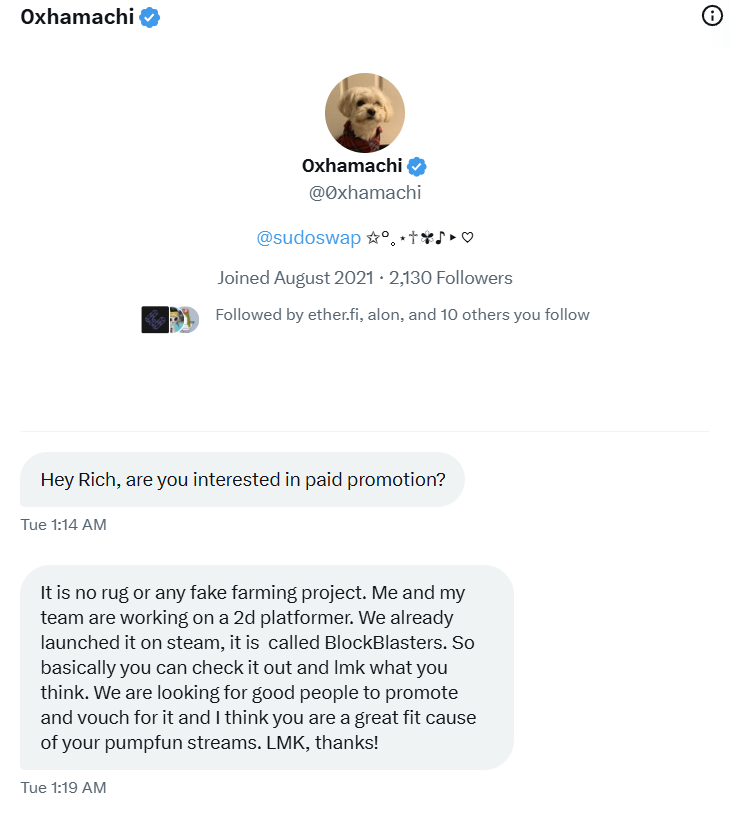
Researchers believe the victims were deliberately targeted. The attackers searched the X social network (formerly Twitter) for people holding large amounts of cryptocurrency, then sent them messages asking them to try the game and promote it.
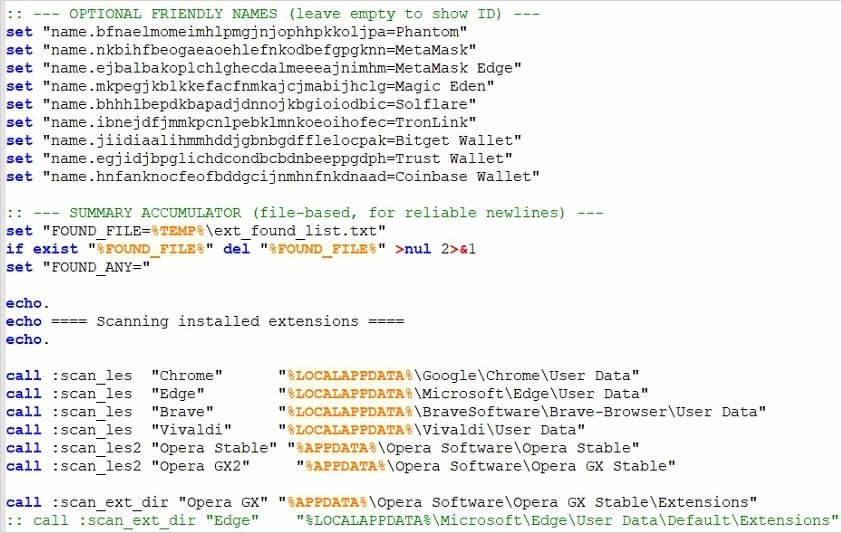
Information security researchers published a brief report analyzing a dropper batch script that performed environment checks before collecting Steam login credentials along with the victim’s IP address and sending all this data to a command-and-control server. GDATA specialists also examined this campaign, reporting that alongside the batch-based stealer the attackers used a Python backdoor and a stealer payload StealC.
At the same time, the attackers made a number of mistakes — for example, they left the code of their Telegram bot and tokens exposed. As a result, OSINT enthusiasts claimed that they had managed to identify the perpetrator. According to them, it is an Argentine immigrant currently living in Miami, Florida, whom they have already reported to U.S. Immigration and Customs Enforcement.
It’s worth noting that this is already the fourth case in 2025 involving the discovery of malware on Steam. In the spring of this year, the malicious games Sniper: Phantom’s Resolution and PirateFi were removed from the platform, and in July a game called Chemia was found on Steam with an embedded infostealer.