Microsoft reported that the hacker group Secret Blizzard (also known as Turla, Waterbug, and Venomous Bear) is targeting staff at foreign embassies in Moscow. The report states that the hackers allegedly use a MitM (Man-in-the-Middle) position within internet service providers’ networks and disguise their malware, ApolloShadow, as Kaspersky Lab’s antivirus.
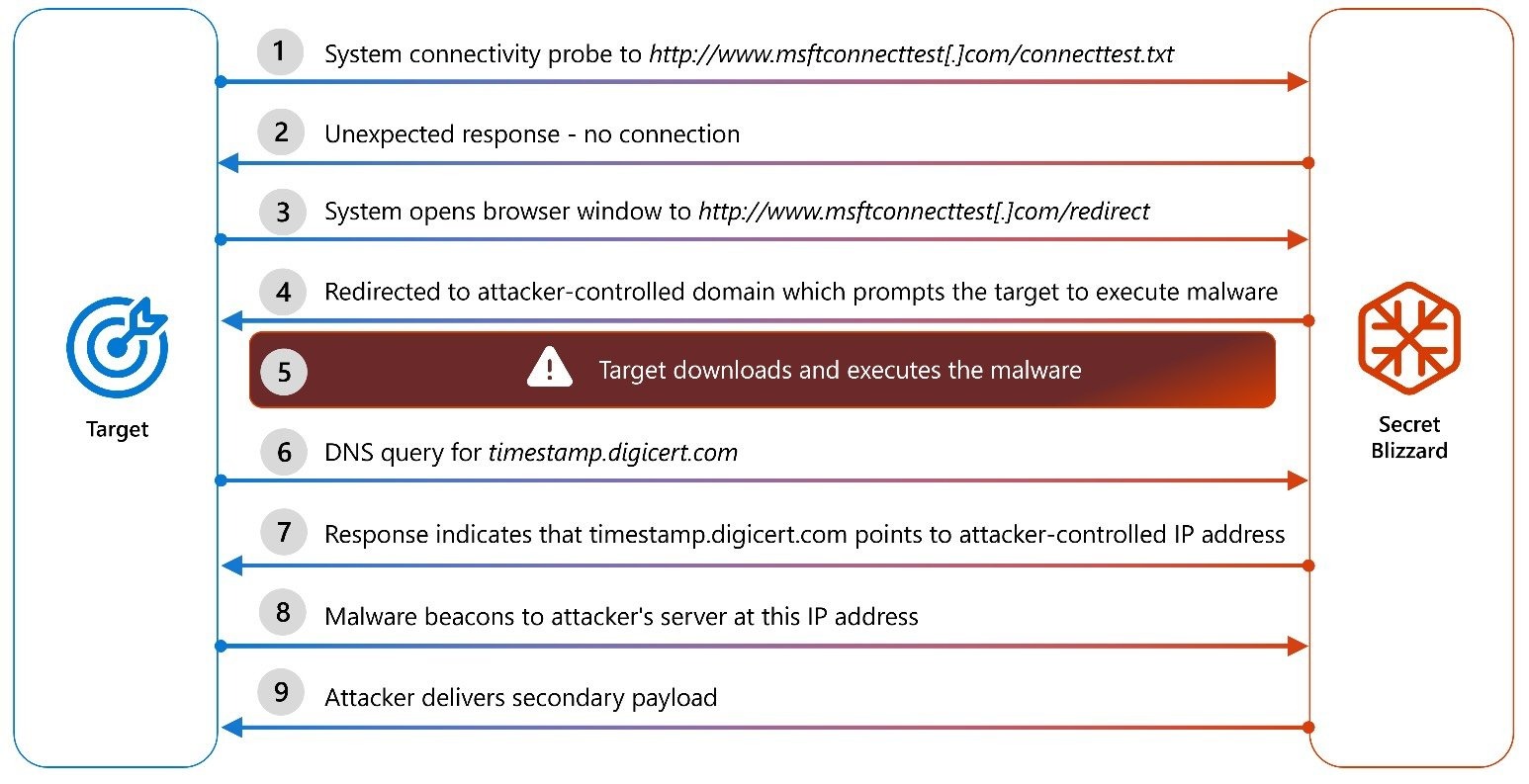
Microsoft Threat Intelligence researchers report that they discovered this campaign in February 2025. However, it has been ongoing since at least 2024, with hackers using access to unnamed internet providers’ networks to direct targeted users to malicious websites, which at first glance appear to be well-known and trustworthy.
The main goal of the attackers is to trick the victim into executing a payload disguised as a Kaspersky Lab antivirus installer, which in reality is the ApolloShadow malware.
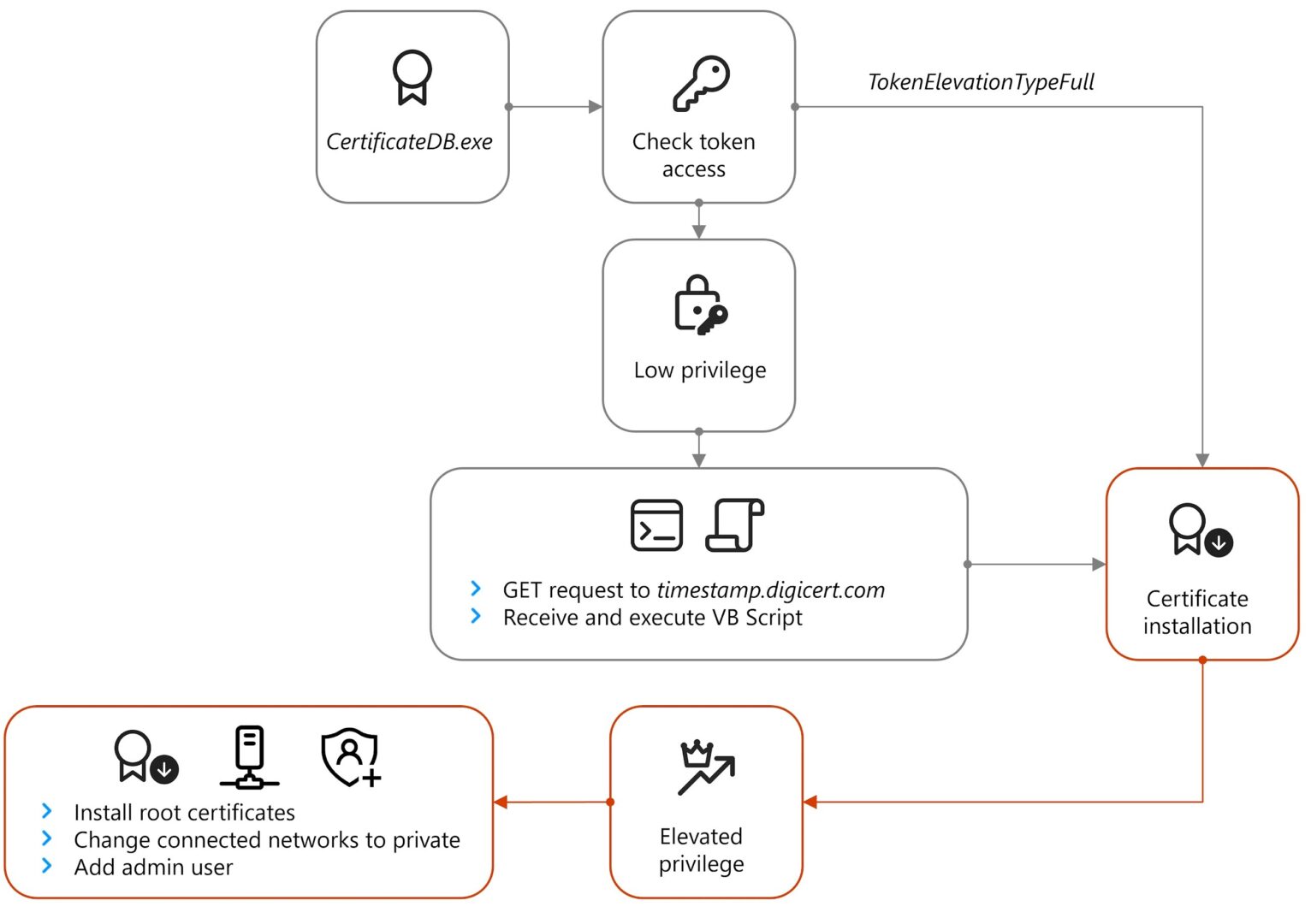
“As soon as the system opens the browser window to this address, it redirects to a separate domain controlled by the attacker. Most likely, a certificate verification error is displayed there, after which the victim is prompted to download and run ApolloShadow. Once launched, ApolloShadow checks the ProcessToken privilege level. If the device is not operating with default settings (without administrator rights), the malware will display a UAC popup to convince the user to install certificates from a file named CertificateDB.exe. This file is disguised as a Kaspersky installer, and it is needed to install root certificates and obtain elevated privileges in the system,” the company report states.
ApolloShadow installs a root certificate on the device, allowing Secret Blizzard to deceive the compromised system into recognizing malicious sites as legitimate. As a result, hackers gain the ability to maintain long-term access to the victim’s machine, collect data, and continue developing the attack further.
“This is the first instance where Microsoft can confirm the capability of Secret Blizzard to conduct espionage at the level of internet service providers, meaning that diplomatic personnel using local internet providers and telecommunications are at high risk and may become targets of Secret Blizzard’s AitM [Adversary-in-the-Middle] attacks,” states Microsoft.
At the same time, researchers told the media that they “have no understanding of the nature of the relationship between the attackers and the internet service providers.”