
Plenty of pentesting distributions are available nowadays. Regardless of their popularity, all these systems have the same purpose: provide hackers with a handy and reliable multitool suitable for all occasions. The majority of utilities included in such highly-customized builds are never used in everyday life, but they raise the hacker’s self esteem (“You have mere 150 utilities, while I have 12,000!”). This article briefly describes the best and most powerful distributions – both well-known and unfairly forgotten.
warning
The primary purpose of these Linux distributions is pentesting, and you are solely responsible for their practical application. Remember that improper use of pentesting software is punishable by law.
NST
- Initial release: 2003
- Based on: Fedora
- Platform: x64
- Graphical shell: MATE
The NST (Network Security Toolkit) distribution is not very well-known, but it definitely deserves your attention. NST is based on Fedora and primarily designed for network attacks. The MATE-based graphical interface reminds of the goodie-oldie 2000s. The pentesting set includes several dozen of most important tools: network scanners, clients for all kinds of services, and various traffic interceptors. Too bad, some useful components are missing, for instance masscan and aircrack (although airsnort is present).

Most utilities are stored in the Applications → Internet folder, including Java-based Angry IP Scanner, Ettercap, end even OWASP ZAP, addressed in one of our earlier articles. The netwag package offers a good assortment of spoofing and scanning modules, and it’s still pretty efficient (although not very handy and terribly obsolete).
All the tested programs run smoothly. Overall, this distribution can be recommended to old-school hackers nostalgic for an ancient interface and familiar tools.
Kali
- Initial release: 2013
- Based on: Debian
- Platforms: x86, x64, ARM, VirtualBox
- Graphical shell: Xfce
As you are well aware, Kali is one of the most popular hacking distributions. Even schoolchildren know about it, and it’s available as an app in Microsoft Store. One of its main advantages is accessibility, but frankly speaking, the system is slightly overloaded with various tools (not as much as BlackArch, but still). Furthermore, some of these tools don’t work properly out of the box (or don’t work at all).
In addition, Kali is not foolproof. Experience shows that not all users understand how risky it is to make this system the main OS. From its core to shell, Kali was created and optimized for combat missions on information security fronts, and it’s poorly suited for regular daily operation. Many features you need in everyday life are not present in Kali, and an attempt to install them may cause malfunctions in the OS or even make it inoperative.
In skilled hands, Kali is a powerful tool, but it must be kept out of the reach of children. More than 600 official and unofficial utilities are included in this distribution, and new modules, frameworks, and other features are released on a regular basis.
Kali is designed for a wide range of tasks, but its primary purposes are attacks in the network environment, identification of vulnerabilities in web applications, and gaining access to wireless networks. A successor to BackTrack, Kali is well adapted to interaction with wireless communication channels, especially Wi-Fi. It includes Metasploit framework and hence can be used for pentesting of remote hosts. Still, its kernel and majority of tools supplied with Kali are designed for hacking Wi-Fi systems.
It is also necessary to note that Kali distributions include plenty of wordlists suitable for attacks targeting not only Wi-Fi, but Internet accounts and network services as well.

For greater convenience, the official website offers a distribution for virtual machines – it’s much safer to use for hacking purposes a system without installation: you never know who may dig in your computer later…
The final verdict is: Kali is a great tool if you know how to use it, but never give it to children.
DEFT
- Initial release: 2005
- Based on: Ubuntu
- Platform: x86
- Graphical shell: LXDE

Created in sunny Italy, DEFT features a broad range of reconnaissance and hacking tools. Furthermore, these tools are harmoniously built into it. Overall, the system, resembles a Swiss Army knife – elegant and extremely useful.
DEFT is based on Lubuntu and features a handy graphical interface. The product offers all kinds of essential utilities: from antiviruses, systems retrieving information from the browser cache, and network scanners to specialized tools required when you search for hidden information on a hard drive.
The OS gives you access to erased, encrypted, or corrupted data stored on various media types.
The main toolkit is located in the DEFT folder accessible in the Run menu.

Initially, this distribution was developed for the network police and IS incident response specialists. Accordingly, an important advantage of DEFT is competitive intelligence, including the analysis of interrelations between social media accounts.
DEFT even includes a utility detecting geolocation of LinkedIn and Twitter accounts; it effectively identifies the home country and city for an account.
Unlike Kali Linux or Tsurugi, DEFT is foolproof: not a single tool can be launched without proper precautions. If you don’t have an in-depth understanding of security mechanisms, this OS would be totally useless for you.
Nearly all applications and options require root privileges, so don’t rush to launch utilities or create unprivileged users.
Important: DEFT gets updates from special repositories, and some of them are locked with keys. we spent a few days trying to find out where to request the data from (and found the keys in the process).
Overall, the system is perfectly suited for forensics and incident investigation, especially if you have physical access to the data storage device, be it a disk, a flash drive, or a smartphone.
Tsurugi
- Initial release: 2018
- Based on: Ubuntu
- Platforms: x86 (partially), x64
- Graphical shell: MATE
This distribution is relatively new and not well-known among information security specialists yet: a joint project of the DEFT and Kali developers.
Tsurugi (which means a two-handed Japanese sword) is based on Ubuntu and uses MATE desktop environment. It is primarily intended for forensics and OSINT, not for pentesting, but its tools and features allow to use it for this purpose as well. The system is shipped as a live image, but you can perform a permanent installation if necessary.

A simple GUI features numerous widgets showing the load on the processor, hard drives, and RAM; the network speed; and other useful info.
The heritage of Kali is obvious, including numerous preinstalled tools that you don’t need. On the other hand, the system interface is minimalist and compact. The logic of security systems, including both the web and anti-tracking protection, is based on the best DEFT practices.
The majority of the tools are located in Applications → TSURUGI.

Here you can find utilities responsible for operations with images, malware analysis, data recovery, and OSINT.
Similar to Kali, Tsurugi isn’t foolproof. Like a sharp Japanese sword, it’s suitable only for skilled specialists who act prudently and thoughtfully.
The extensive assortment of utilities allows to use the system as a multitool for a wide range of tasks. Even though Tsurugi resembles Kali, there are significant differences between these distributions. For instance, the number of malfunctioning and inoperative utilities in Tsurugi is significantly less in comparison with Kali
Verdict: if, for some reason, you don’t want to use Kali, Tsurugi is a good alternative.
Parrot
- Initial release: 2013
- Based on: Debian
- Platforms: x86, x64, ARM
- Graphical shell: MATE

This nice-looking Linux distribution is based on Debian. Frozenbox developed it to test the security of computer-based systems, identify vulnerabilities, and assess their severity.
Parrot uses MATE desktop environment, and my personal experience with it is very positive.

In the Applications section, you can find the Anon Surf utility. One of the exciting features of Parrot is that a number of anonymization tools are preinstalled in it, and when you select Anonsurf Start, all system traffic is redirected through Tor. The same section allows you to use the DNS of the OpenNIC project, a non-national alternative to traditional Top-Level Domain registries. In addition, by selecting the Check IP parameter, you can check your current external IP address.
The second important section is Cryptography. It contains a utility called GPA – a graphical interface of GnuPG designed to encrypt information and create electronic digital signatures. GnuPG is a good alternative to PGP encryption. Should you need GPG, Parrot offers you the zuluCrypt utility, an analogue of VeraCrypt that allows to encrypt folders, partitions, flash drives, etc.
The next (and most exciting) section is called Parrot. It contains pentesting utilities; some of them exist in Kali Linux, but others are absolutely unique.
The Internet tab deserves special attention. It contains pre-installed Tor Browser, Electrum Bitcoin wallet, and the XSSer utility (a framework used to detect and exploit XSS vulnerabilities in web applications). The tab also includes Claws Mail, a fully featured mail client supporting GPG encryption. As a special bonus, you get Ricochet IM, a decentralized anonymous messenger operating through the Tor network.
That’s all about Parrot Security. As you can see, it’s suitable not only for pentesting, but can also be used as an OS for everyday work (for those who know exactly why do they need it).
In my personal opinion, Parrot is a high-quality and handy OS. It’s always nice to deal with a system whose tools don’t require repairs and can be used out of the box.
BlackArch
- Initial release: unknown
- Based on: Arch
- Platforms: x64
- Graphical shell: none, several desktop managers are available
BlackArch is a huge distribution: the image of the current version is over 14 GB in size! It can be downloaded from a torrent as well, and there are plenty of seeds.
The system is unbelievably user-friendly: if you manage to download and run this monster, BlackArch will require you to enter the login and password for a live session. Information about them can be found in the user manual available on the official website (just in case, the logon credentials are root/blackarch). Apparently, the developers have totally forgotten about live users…
Nothing is displayed after the successful logon: just an empty Fluxbox; to call the menu, you have to right-click anywhere on the desktop.

All applications are conveniently categorized in the blackarch submenu of the main menu. Forty-nine categories containing tools suitable for any situation are present. Forget about navigating the system with the mouse (like you do in Windows). Only the keyboard, only hardcore! On the other hand, since you are dealing with *nix systems and your goal is hacking, what else would you expect?
BlackArch includes all the popular (and not-so-popular) hacking tools, including such iconic programs as Metasploit and BeEF XSS. The detailed description of all utilities embedded in this monstrous distribution goes beyond the scope of this article; so, we am going to list only the most notable ones, while others can be found in the documentation.

BlackArch uses Wine to run some ‘alien’ applications, for instance, mft2csv (see the above screenshot) that parses the MFT of the NTFS file system for subsequent analysis. Java (OpenJDK 14.0.1) is supported as well.

The terminal (as well as the whole graphical solution) looks grim, but the software versions are up-to-date. On the one hand, it seems that the developers were inspired by sci-fi movies about hackers; on the other hand, the system is quite usable, even though it requires advanced Linux skills.
Overall, if you are not ready to fight your way through numerous configs, set arguments, and search the Internet for any small detail, use Kali or Parrot – on these systems, you can do at least something without a thick desktop reference book. BlackArch is more than unfriendly to novice hackers. And of course, don’t even think about using this multitool as your main OS.
BackBox
- Initial release: 2010
- Based on: Ubuntu
- Platforms: x64
- Graphical shell: Xfce
In the end, we would like to present a distribution standing apart from others. BackBox does not pretend to be the best hacking multitool – but it is perfectly suited for everyday use. Its Xfce graphical shell minimizes the consumption of system resources. The system is offered in two variants: ISO and Torrent. No images for virtual machines are available.
BackBox is based on Ubuntu (to be specific, Xubuntu), which makes it a handy home OS. Extensive documentation and numerous forums provide an answer to any question you may have. The BackBox kernel is not tweaked in some twisted way; so, your manipulations likely won’t inflict any harm. These features make BackBox an excellent choice for a novice pentester.

The assortment of tools available out of the box is not very impressive: some 200 items; but this is more than enough to make first steps in the information security industry. In other aspects, BackBox is just like Xubuntu – with all its bugs features and functions.
An important advantage is that all tools are conveniently grouped in the menu. Even if you don’t know a single tool (e.g. have no idea what to use for attacks on Wi-Fi), you will easily find everything you need there.
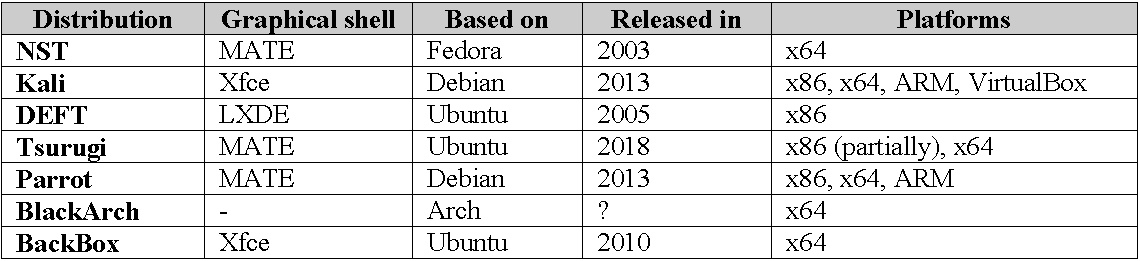
Summary table
Conclusions
All distributions have their strengths and weaknesses. Try different variants, chose the one that is optimal for you, and good luck in your pentesting endeavors!