
Remote access to Web cameras and security cameras is a common hacking technique. It does not require any special software or even special skills. All you need is a Web browser and a few simple manipulations. In other words, you may gain access to thousands of electronic eyes around the world if you know how to find their IP addresses and exploit their vulnerabilities.
WARNING
This is a research article intended for cybersecurity experts. Publicly available databases were used during its preparation. Neither the Editorial Board nor the author can be held liable for unethical use of any information provided.
Eyes wide shut
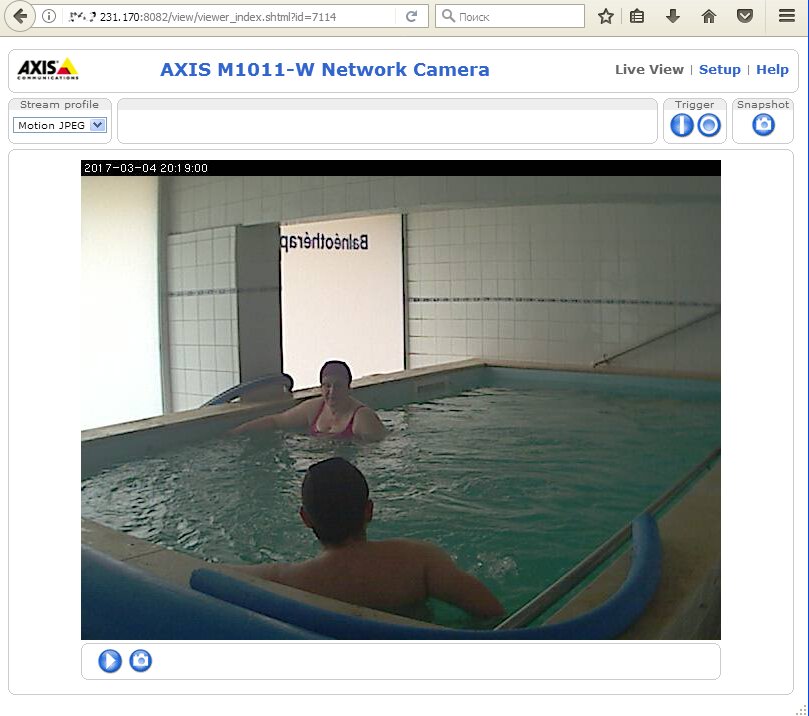
Video surveillance is mostly used for security purposes, so, probably, no nude celebs on the first camera you hack (but hey, we cannot stop you trying). In most cases, you will watch a show of a warehouse or a parking lot. In VGA resolution. Without anyone around. A rather boring, silent show. Even if you see a living person, they would likely just pass or wait. Of course, watching camera operators or working robots would be much more entertaining!
Many people confuse IP and Web cameras, even though these are essentially different devices. A network camera (or IP camera) is a self-sufficient surveillance tool. It is controlled via a Web interface and streams video through the network. In fact, this is a self-contained microcomputer running a Linux kernel. Ethernet (RJ-45) or Wi-Fi connection makes it possible to directly connect to an IP camera. In the past, special client applications were required; not anymore. The majority of modern cameras can be controlled via a browser from any device: either a computer or smartphone. Normally, IP cameras are always on and available via remote access. Hackers use this feature to connect to them.
A Web camera, on the other hand, is a passive device connected to a computer via USB or embedded in a laptop and controlled locally via an OS driver. These drivers are divided into two types: universal (preinstalled in the OS and supporting many camera models from various manufacturers) and proprietary (written for a specific model) ones. In this situation, the hacker’s task is to intercept the video stream broadcast by the camera via its driver. The Web camera does not have an IP address or built-in Web server. Therefore, to hack it, you must first crack the computer it is connected to. Enough with the theory; time for hands-on experience!
Hacking security cameras
If an IP camera is hacked, it does not necessarily mean that somebody has seized control over the computer used by its operator. It just means that the operator is not the only person watching the video streamed by that camera. Such single targets are easy to hack, even though there are some pitfalls on the way.
WARNING
Unauthorized surveillance through hacked cameras may be punishable under criminal and administrative laws. Normally, the punishment is limited to a fine, but not everybody manages to get off the hook that easy. For instance, Matthew Anderson spent 1.5 years in jail for hacking Web cameras with a Trojan. Another hacker, who has repeated his achievement, was sentenced to 4 years behind bars.
First, remote access to the selected camera may be possible only via a certain browser. Some cameras support new versions of Chrome or Firefox, while others require an old version of IE. Second, the video is transmitted in various formats. You may have to install the VLC plugin, or Flash Player, or an old Java version – and still, some devices won’t show you anything without their own plugins.
Sometimes you may encounter a truly original solution. For instance, a Raspberry Pi transformed into a surveillance server with Nginx, and broadcasting video via Real-Time Messaging Protocol (RTMP).
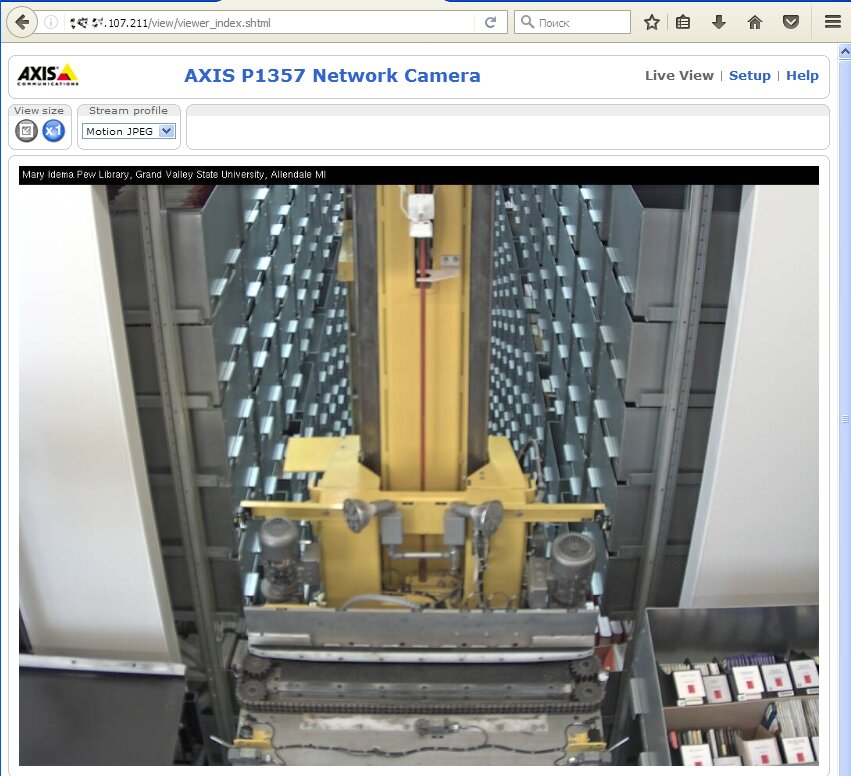
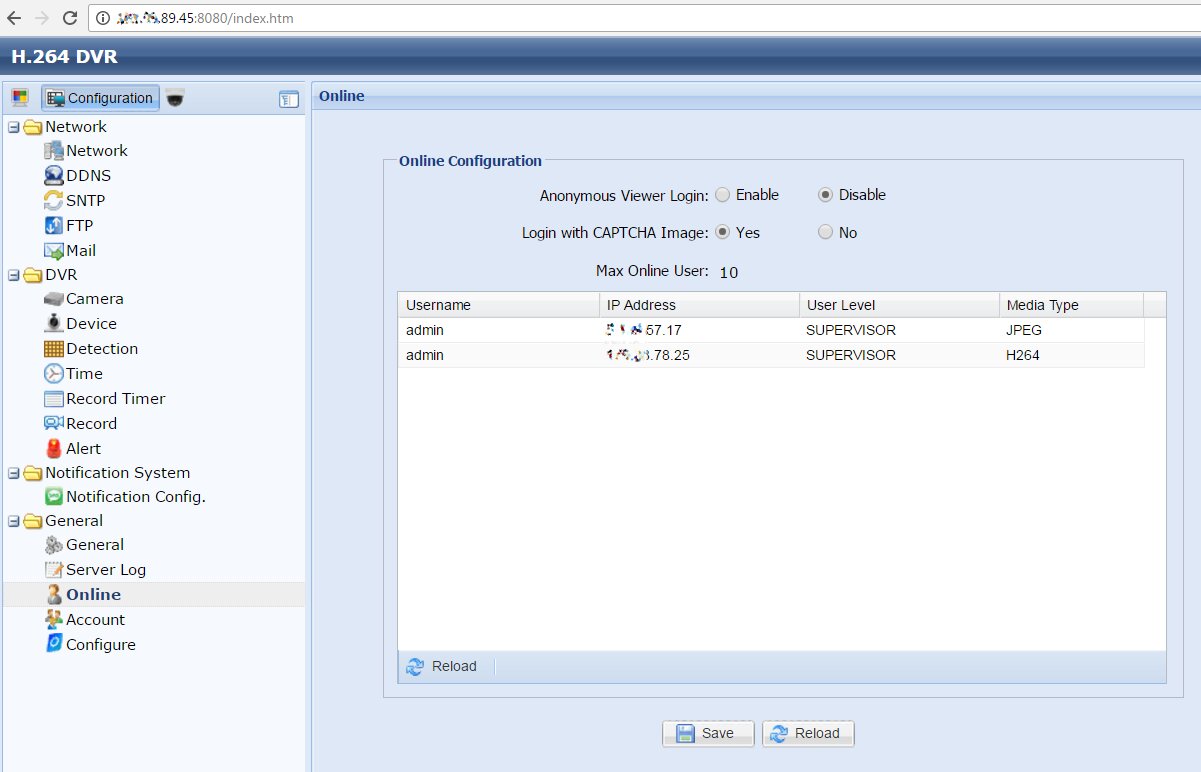
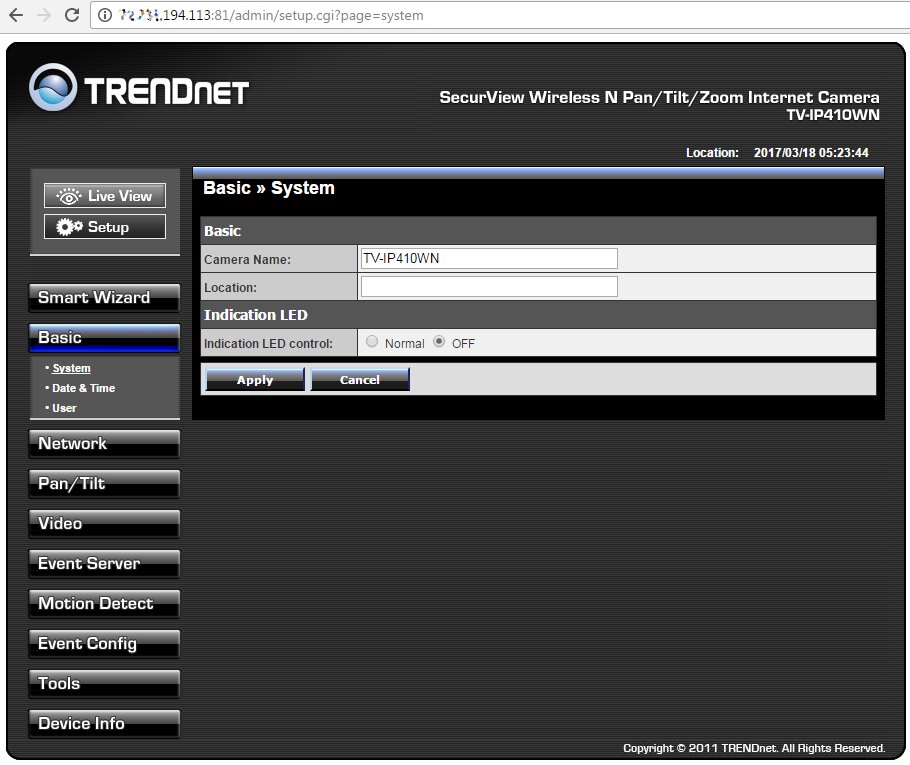
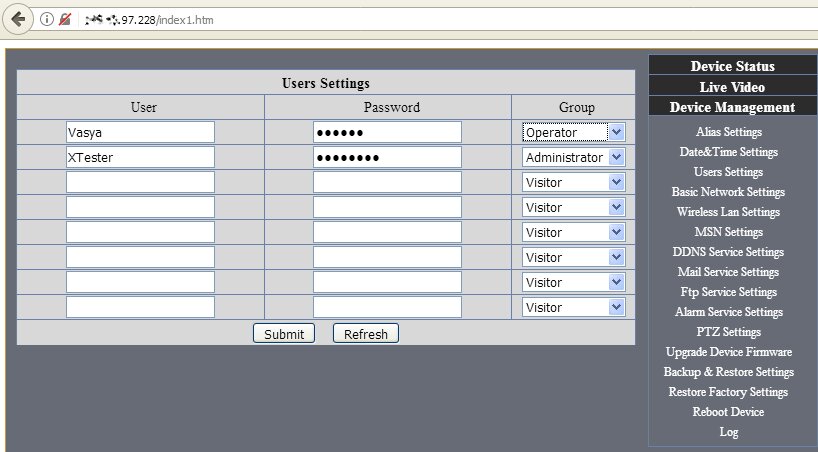
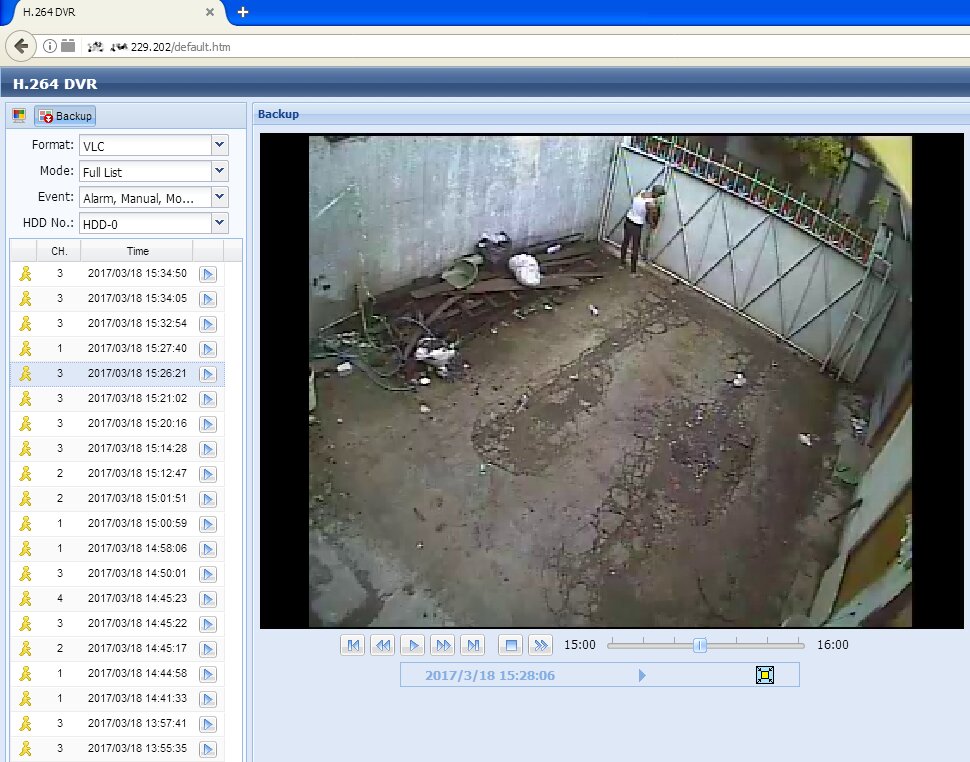
In theory, two secrets guard an IP camera against hacking: its IP address and account password. In reality, it is not a big deal to identify the required IP address nowadays. Most cameras use standard IP addresses, and they send similar replies to requests sent by search robots. In addition, lists of millions of cameras’ IP addresses are regularly shared on hackers’ forums. The screenshot below shows that the camera owner has disabled anonymous access and added a CAPTCHA to block automated attacks. However, these settings can be changed without authentication using the direct link /index.htm.
Vulnerable security cameras can be located using Google or another search engine and sophisticated requests. For example:
inurl:"wvhttp-01"
inurl:"viewerframe?mode="
inurl:"videostream.cgi"
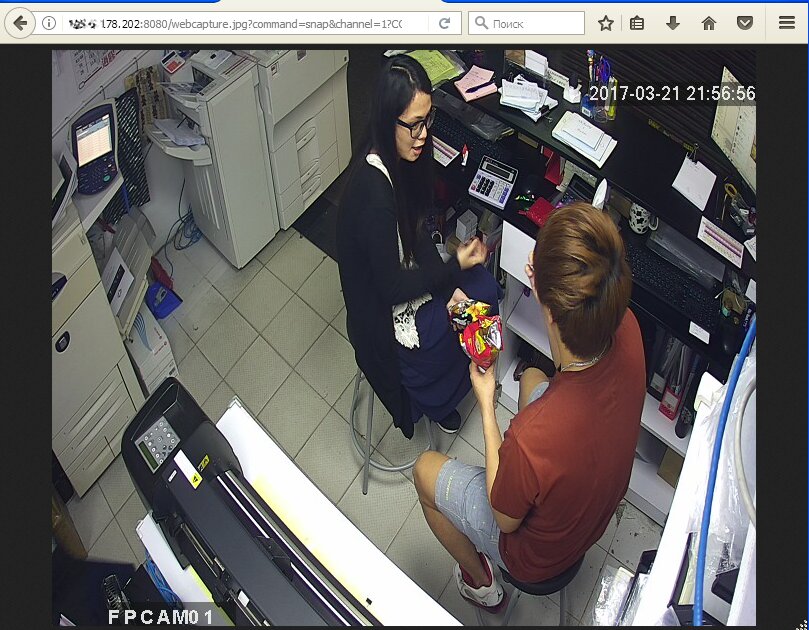
inurl:"webcapture"
inurl:"snap.jpg"
inurl:"snapshot.jpg"
inurl:"video.mjpg"
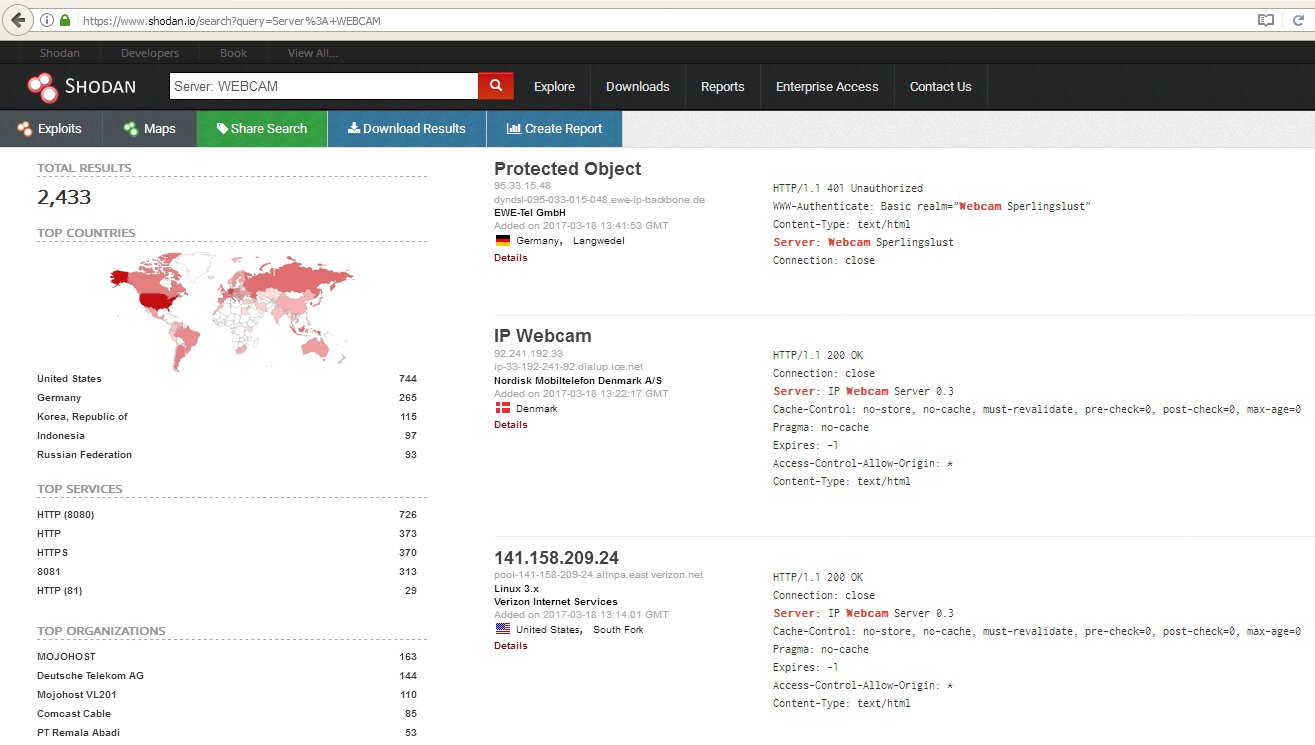
It is even more convenient to look them up with Shodan. Initially, we may enter a simple request – netcam – and then start using more sophisticated ones: netcam city:Moscow, netcam country:RU, webcamxp geo:55.45,37.37, linux upnp avtech, etc.
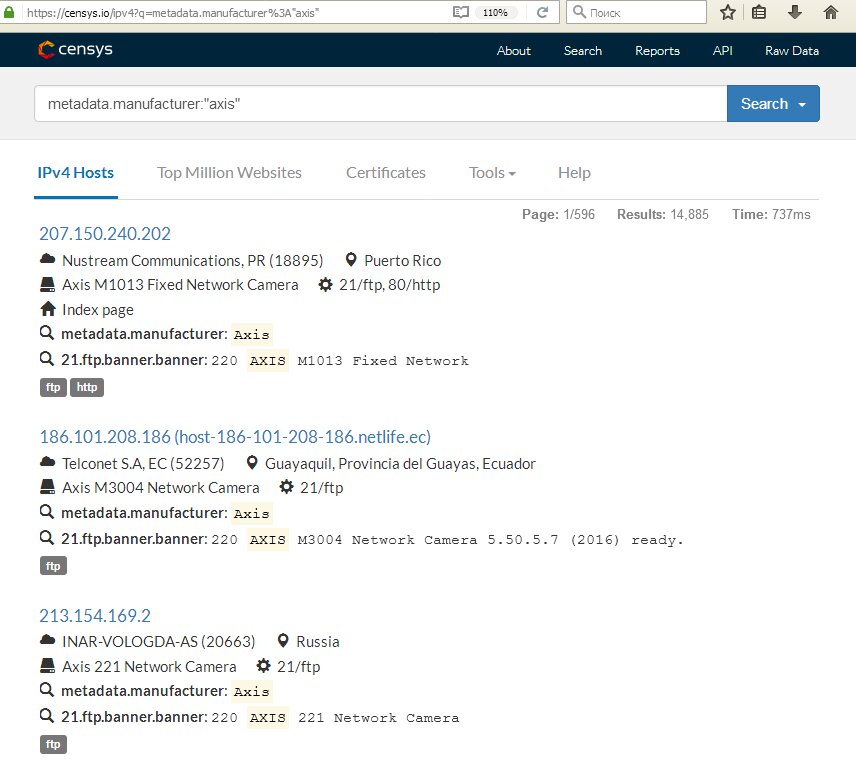
Censys engine can also be used to search for cameras. Its language is more complicated, but it is not a big deal to master it. For instance, the request 80.http.get.body:"DVR Web Client" will show cameras connected to an IP digital video recorder, while metadata.manufacturer:"axis" will find cameras produced by Axis.
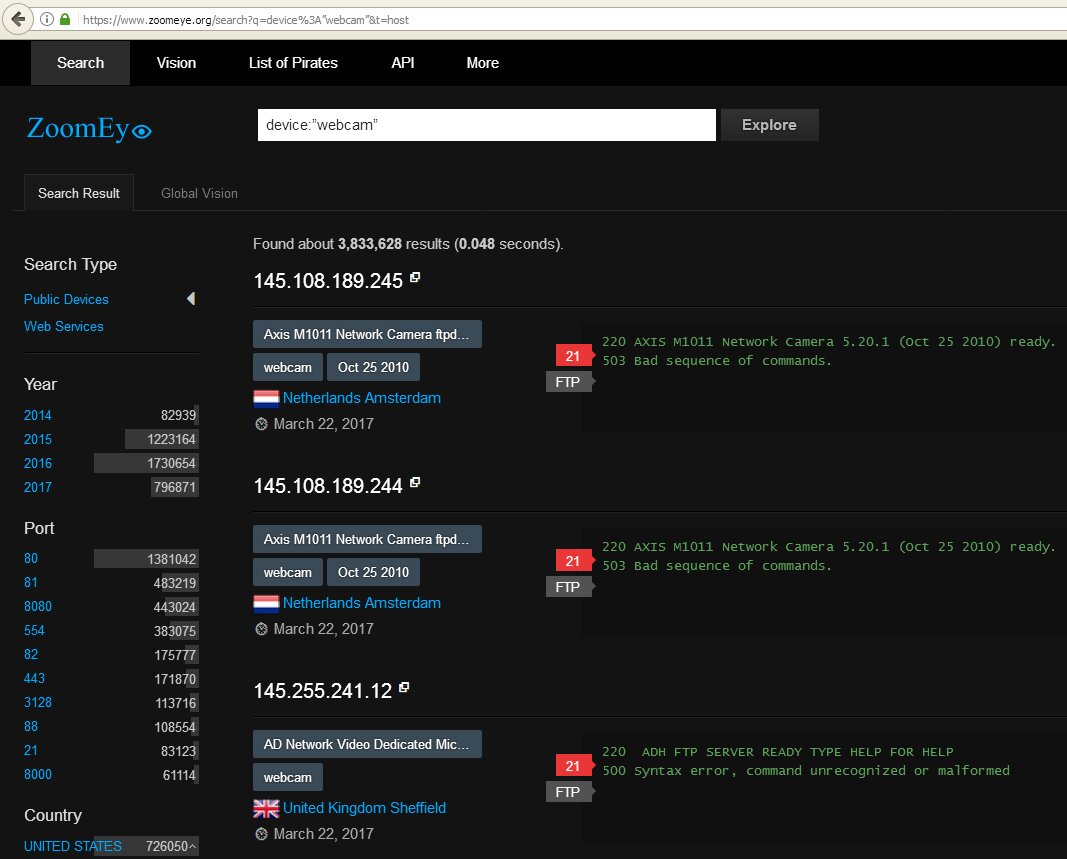
Another excellent search engine for the Internet of Things is ZoomEye. To locate cameras, use requests device:webcam or device:media device.
It is also possible to search in an old-fashion way by scanning ranges of IP addresses looking for characteristic camera responses. Lists of IP addresses for certain cities are available on this Web service. It also offers a port scanner (in case you do not have your own yet).
We are primarily interested in ports 8000, 8080, and 8888 – because they are often set by default. The default port number of a specific camera can be found in its manual. This number hardly ever changes. Of course, any port may support other services as well; so, search results have to be additionally filtered.
The model of the found camera is normally provided on the title page of the Web interface and the settings.
Speaking of the above-mentioned specific client apps required by some cameras, this primarily refers to programs like iVMS 4xxx shipped with Hikvision cameras. Manuals to the program and cameras are available on the manufacturer’s site. If you find such a camera, chances are high that it still has a factory password, and the app will grant you full access.
In fact, the situation with passwords to security cameras is funny. Some cameras do not have passwords; accordingly, there is no authentication at all. Others have default passwords that can be found in their manuals. The list of most common logins and passwords for various models is available on ipvm.com.
Developers often leave a ‘staff entrance’ for service centers in the firmware. It remains open even if the camera owner has changed the default password. Of course, such information is not provided in user manuals, but it can be found on respective forums.
Another problem is that many cameras use the same GoAhead Web server. It has several known vulnerabilities, but camera manufacturers do not rush to patch them.
INFO
GoAhead was first mentioned in Hacker in 2002; last year, a vulnerability resulting in Remote Code Evaluation (RCE) was found in it.
GoAhead is vulnerable inter alia to stack overflow that can be caused by a HTTP GET request. Chinese manufacturers further exacerbate the problem by modifying GoAhead in their firmware, thus introducing additional vulnerabilities.
Today, over one million IP cameras and IP video recorders from various manufacturers enable remote access without authorization. A Python script automating attacks on vulnerable devices is available on GitHub. The problem was discovered in early 2017 in the course of reverse engineering of the firmware for digital video recorders (DVR) produced by Dahua Technology. Later, researchers discovered that it affects over a thousand models from different manufacturers replicating each other’s errors. The original researcher promised to withhold disclosing the details to give the manufacturers some time to rectify the vulnerability, but he is ready to share it privately with cybersecurity specialists by e-mail. If you have a CEH (Certified Ethical Hacker) certificate or a similar credential, you may try to contact him.
Firmware by other manufacturers may include other bugs such as buggy conditional jumps. Such cameras may grant you access even if you have entered an incorrect password or pressed the Cancel button several times. In the course of this research, I encountered more than ten such cameras. Therefore, it you are sick and tired guessing the default password, try clicking Cancel, and you may get access right away.
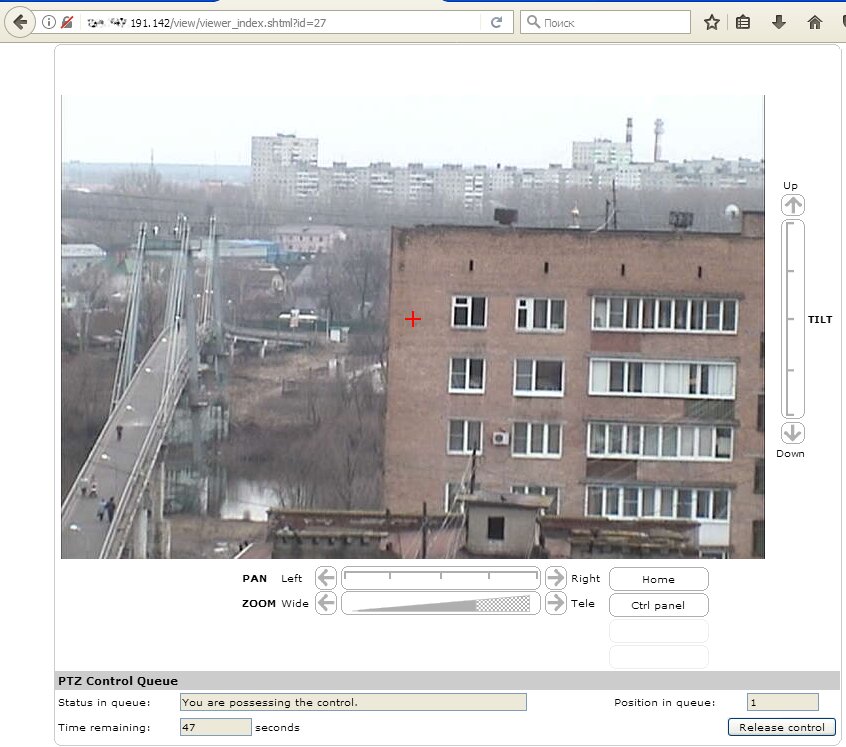
Midrange and high-end cameras are mounted on rotary joints. After hacking such a camera, you may change the camera’s angle and look around. Sometimes, you can enjoy playing ‘camera pulling’ with somebody trying to control it. In most situations, the attacker gains full control over the camera directly from the browser after typing its IP address.
As said above, thousands of cameras are vulnerable, so let us examine at least one brand in more detail. Take, for instance, the popular manufacturer Foscam. Its cameras, similarly to many others, have a backdoor. In addition to the built-in admin account (it is recommended to change its password when the camera is turned on for the first time), there is one more account: operator. Its default password is blank, and very few users bother to change it.
In addition, Foscam cameras have easily recognizable addresses because of patterns used in their registration; it looks as follows: xxxxxx.myfoscam.org:88 (where XX represent two Latin letters and xxxx would be four digits).
If the camera is connected to an IP video recorder, we can remotely watch older records as well as the real-time video stream.
Motion sensors
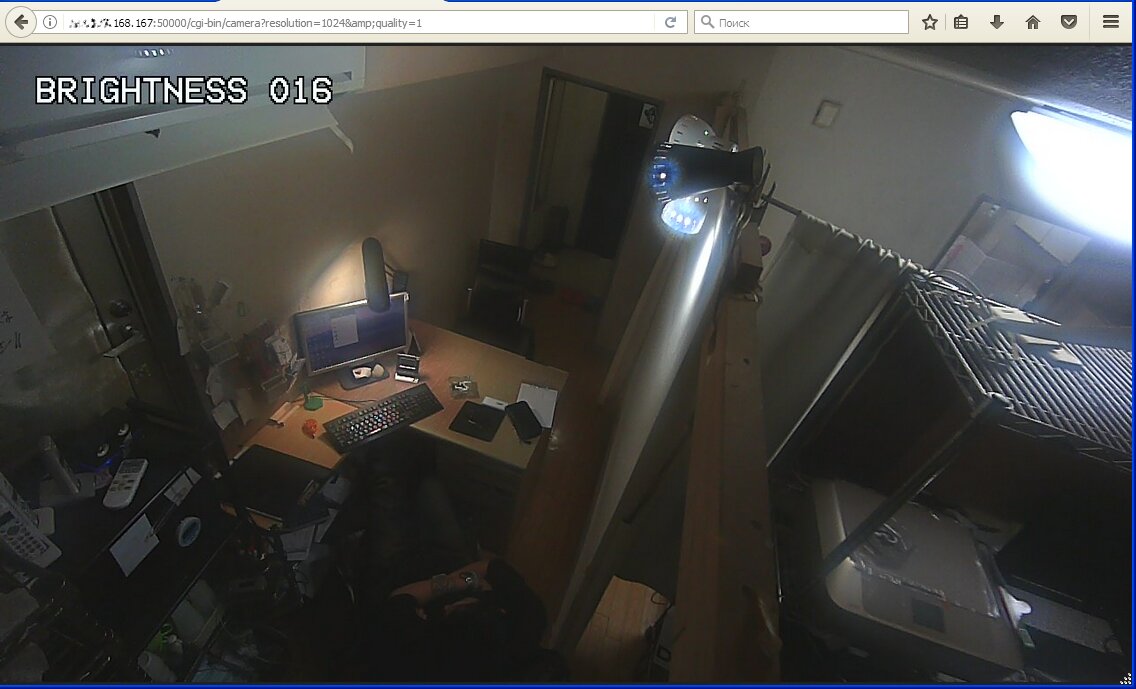
Professional security cameras are equipped with motion sensors operating even in total darkness thanks to built-in infrared detectors. This solution is more efficient than permanent infrared lighting because it does not expose the camera and enables covert surveillance. Living humans always glow in the infrared band. As soon as the sensor detects motion, the controller starts recording. If the photosensitive element indicates low-light conditions, the additional lighting is activated. This happens at the beginning of the recording. As a result, the intruder does not have time to turn the face away from the camera.
Cheap cameras are simpler. They do not have a separate motion sensor and instead compare individual frames. If a frame is different from the previous one, then something has changed, and this should be recorded. If no motion was detected, the series of frames is deleted. This technique allows saving space, reducing traffic, and expediting rewinding. Most motion sensors can be tweaked. You can set the trigger level to avoid recording any random motion, and set additional alerts (e.g. sending a text message and the last frame recorded by the camera to your smartphone).
Software motion sensors are inferior to hardware-based ones, and often cause confusion. In the course of my research, I encountered two cameras continuously sending alerts and recording gigabytes of ‘compromising’ footage. All these alerts were false. The first camera was installed outside a warehouse. It was all covered with spiderweb fluttering in the wind and driving the motion sensor crazy. The second one was in the office right opposite a blinking router. In both cases, the trigger level was too low.
Hacking Web cameras
Web cameras using a universal driver are also called USB video class (UVC) compatible. It is easier to hack a UVC camera because it uses a standard and well-documented protocol. However, to get access to the camera, the attacker must first gain control over the computer it is connected to.
From the technical perspective, the access to cameras on Windows-based computers (regardless of the OS version) is exercised via the camera driver, DirecDraw filters, and VFW codecs. However, a novice hacker does not have to go into such details unless they are going to write a sophisticated backdoor. It is sufficient to take any Remote Admin Tool (RAT) and slightly modify it. There are plenty of publicly available remote administration tools on the Internet. In addition to top-quality backdoors on VX Heaven, there are many legitimate utilities, including Ammyy Admin, LiteManager, LuminosityLink, Team Viewer, and Radmin. Optionally, you may tweak the following functions in these utilities: automatic acceptance of remote connection requests and minimization of the main window. Then social engineering techniques come into play.
The victim clicks on a phishing link and installs the modified RAT on its computer. Alternatively, the RAT penetrates it via a discovered vulnerability. This process even can be automated. Important: the majority of links to ‘camera hacking utilities’ lead to phishing websites infecting your PC with malware.
Many users’ cameras are inactive most of the time. Normally, the built-in LED indicates when the camera is on, but this cannot protect you from covert surveillance. The activity indicator may be disabled even if the LED and CMOS matrix are physically powered together. Such a trick was successfully performed with iSight cameras installed on MacBook computers. Researchers Matthew Brocker and Stephen Checkoway of Johns Hopkins University wrote iSeeYou utility that can be launched by an unprivileged user. The program exploits a vulnerability in the Cypress controller and reflashes it. The victim launches iSeeYou, and the attacker becomes able to turn on the camera with the LED disabled.
Vulnerabilities are discovered on a regular basis in other controllers as well. A specialist at Prevx has collected a whole bunch of such exploits and demonstrated examples of their usage. The majority of these vulnerabilities are 0day-related, but there are also plenty of well-known bugs that have not been fixed by the manufacturers for some reason.
The number of ways to deliver exploits is growing every day; as a result, it becomes increasingly difficult to catch them. Antivirus programs can often do nothing with modified PDF files, have preset limitations on the scanning of large files, and cannot detect encrypted malware components. Furthermore, polymorphism and continuous recompilations of the combat load became standard practices; therefore, the signature analysis has downgraded on the list of priorities. It is easy nowadays to deliver payload granting remote access to a Web camera. This is a popular amusement among the Internet trolls and script kiddies.
Transforming a Web camera into a surveillance camera
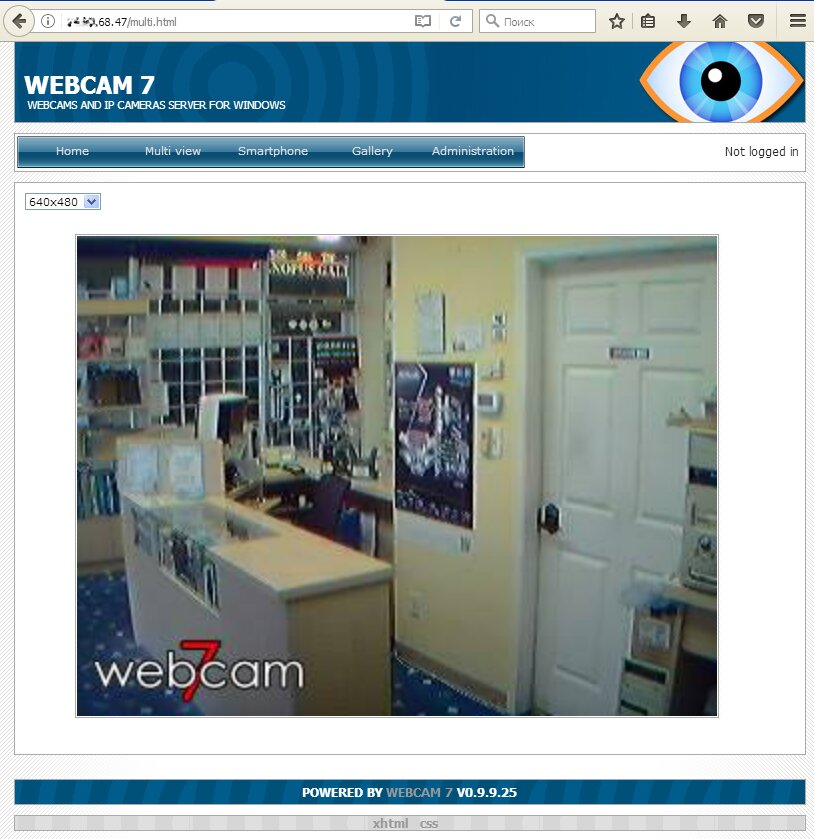
Any Web camera many be turned into an IP camera of a sort. All you have to do is install a video surveillance server on the device it’s connected to. For computers, many people use the old webcamXP, the newer webcam 7, etc.
Similar software is available for smartphones, for instance, Salient Eye. This program saves videos in the cloud, thus, freeing the phone memory. However, there are plenty of vulnerabilities in such tools and in the OS. Therefore, hacking Web cameras controlled by smartphones is as easy as gaining control over IP cameras with unpatched firmware.
<< PICTURE: Webcam 7 streams video without authorization >>
Smartphone as surveillance tool
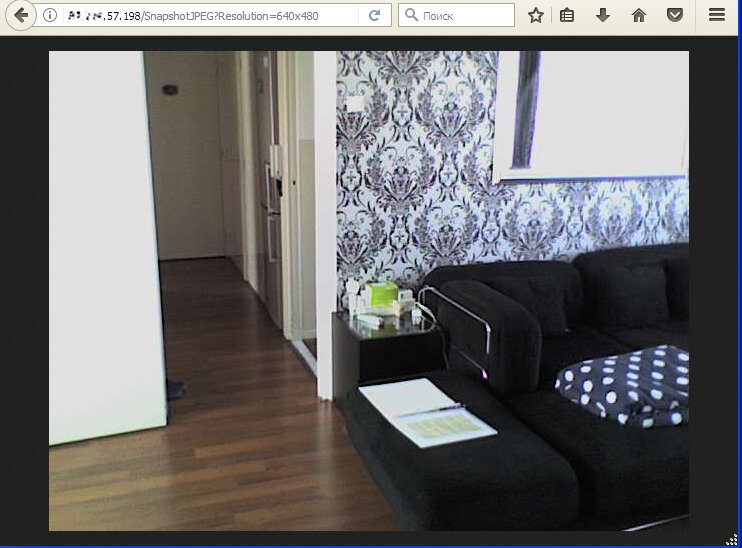
Old smartphones and tablets are frequently used for home video surveillance. In most cases, homeowners are using Android Webcam Server, a simple app broadcasting the video stream from the built-in camera. It accepts requests on port 8080 and opens the control panel on the self-explanatory page /remote.html. On that page, one can change the camera settings and watch the video in the browser window (either with or without sound).
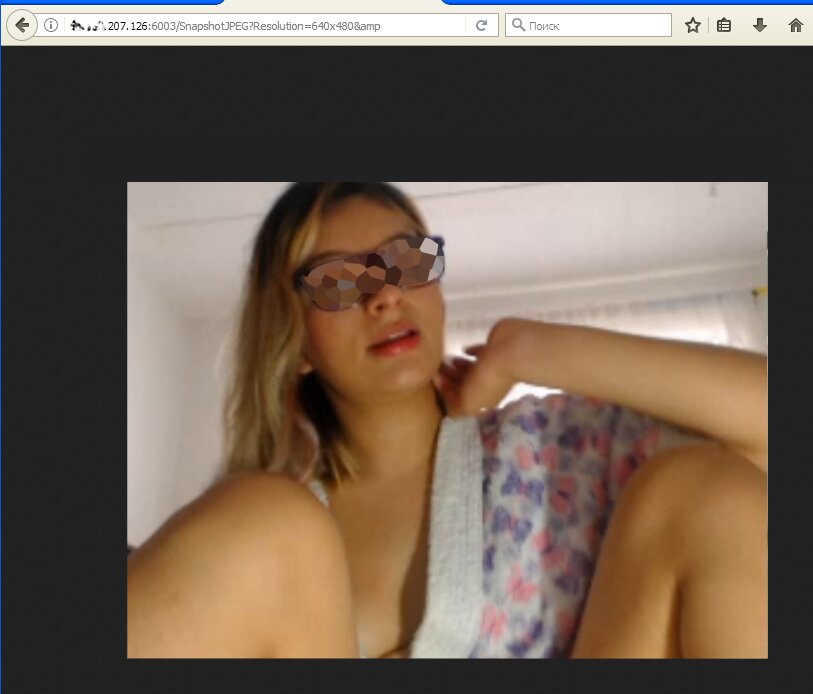
Normally, such smartphones demonstrate some boring views: a sleeping dog or a car parked by the garage door. However, Android Webcam Server and other similar apps can be used in other ways as well. In addition to the rear camera, smartphones also have one on the front. After switching to the front camera, the hacker can see the other side of the homeowners’ life.
Protection from spying
Upon becoming aware that their cameras can be easily hacked, many users start duct-taping them. Owners of Web cameras equipped with privacy covers mistakenly consider themselves protected from surveillance, even though microphones on their computers make eavesdropping possible as well.
Antivirus and security software developers use a trick to promote their products. They show user the scary camera hacking statistics (which is impressive indeed, especially including IP cameras), but only offer some technically limited solutions protecting Web cameras against unauthorized access.
The security of IP cameras can be increased by taking a few simple steps: updating firmware, changing the default password, disabling default accounts, and enabling the IP address filtering. However, this is not enough. Many firmware versions carry over unfixed vulnerabilities making it possible to get access without authentication, such as using the standard Web page address in LiveView or the settings tab. When I discover yet another firmware with unpatched vulnerabilities, it is really tempting to update it remotely!
The situation with Web cameras is different. Their hacking is just the tip of the iceberg. Prior to doing this, attackers normally examine the local disks, steal all account credentials, or make your computer a part of the botnet.
For instance, Kaspersky Internet Security prevents unauthorized access only to the video stream broadcasted by the Web camera. It does not prevent the hacker from changing setting or turning on the microphone. The list of cameras protected by this antivirus is officially limited to Microsoft and Logitech products. Therefore, you must be aware that ‘Web camera protection’ is just an extra and nothing more.
Spying websites
Another problem relates to websites taking control of your camera through the browser. Many Web sites offer communication services, including video chats. Your Web browser throws requests to access the camera and the built-in microphone many times a day. The point is that a Web site may use a script that opens a pop-under window (i.e. an additional window behind the browser window), and permissions of the parental window are transferred to it. When you close the main page, the microphone remains active on the background page. As a result, you think that the conversation is over, while your talk partner (or somebody else) can still hear you.
Most browsers store such permissions indefinitely; therefore, next time you visit this Web site, you won’t get a warning, while others will see and hear you. I suggest checking camera and microphone permissions granted to various Web sites on a regular basis. In Google Chrome, this can be done on the Settings page at chrome://settings/contentExceptions#media-stream. In old Firefox versions, similar settings were located in about:permissions; in new versions, they are set separately for each website by clicking the (i) icon located to the left of the address line. See Mozilla Web site for more details.




Thanks for the article. In fact, CCTV cameras are the most vulnerable because some of those who install them do not change the default password for IP cameras, making them easy prey for hackers.
Don’t forget to change the default password for your security camera, if you forget your password, you can always find a list of passwords for popular cameras online, for example here: http://www.jvsg.com/ip-camera-default-password/
Hi there!
I just wanted to drop by and say how much I appreciate Dahua’s recent change in camera order. As someone who frequently uses Dahua cameras for various projects, the new camera order has made my workflow so much smoother and efficient.
It’s great to see that Dahua is constantly listening to their customers and making changes to improve their products. The new camera order makes it easier to navigate through multiple cameras and quickly access the ones I need without any confusion or frustration.
Thank you, Dahua, for taking the time to make this change and for continuously improving your products. I look forward to seeing what other improvements and innovations you have in store for the future!
I have seven cameras in and around our property where we live naked as exhibitionists.we love the idea of someone watching our activities but can’t find out how to encourage people to view or ‘hack’ us
We have seven cameras around our property and love the thought of people watching us as we spend most of the time naked. How do we encourage people to view or ‘hack’ us