
warning
Illegal collection of personal information constitutes a violation of the “Personal Data Protection Act” and other laws of the Russian Federation. Such actions may also be considered a criminal offense under Article 137 of the Russian Criminal Code, “Violation of Privacy.” Neither the author nor the editorial team bear any responsibility for any consequences resulting from the use of information presented in this publication, which is provided solely for the purpose of informing the reader.
Most Telegram bots that search for and provide personal data upon user request operate using OSINT (Open Source Intelligence) methods. They rely on publicly available sources by exploiting APIs from various services and internet resources. Some bots use leaked databases, but these services often face issues: they may not function reliably and struggle with keeping information up-to-date, as any leaked database becomes outdated over time and obviously doesn’t update itself. These bots monetize through donations, advertising, or by limiting the number of free queries before charging for each additional request. Occasionally, if the administrators are particularly greedy, they may employ all these monetization methods at once.
People search for personal information for various reasons. Some may use it to track down their debtors or find a charming neighbor with strikingly blue eyes. Others may be looking for direct contacts of bloggers or page owners, or simply out of curiosity, want to view posts in private social media profiles.
You can also track down the phone number of a reckless driver who cut you off by using their license plate number. Then you can call them, address them by their full name, and politely ask for an explanation. Some “speed demons” seem to get a bit flustered in such situations. There can be various reasons for needing this information, but the method is the same: semi-free Telegram bots or lookup services, which are still widely advertised on the dark web.
info
For information on how services for obtaining personal data are offered on the dark web and their costs, read the article “Fully Exposed: Who Provides Personal Data Access in Russia and for How Much“.
It’s clear that not all bots are equally useful. Some request payment but either fail to provide relevant information or give outright nonsense in return. Others seem to function but do so in such a bizarre way that the reliability of their data remains questionable. To save you valuable time and money sifting through the muck for gems, your favorite magazine has tested the most popular bots on Telegram and is ready to share the results with you. Let’s dive in!
Get Contact
This is the legendary bot that played a significant role in the high-profile investigation. The bot reveals how a mobile phone number is saved in other users’ contact lists. It gathers information from mobile devices of users who have installed the Get Contact app, so if your friends don’t have the app on their phones, you won’t get any data. The bot allows you to submit no more than three phone numbers per day.
In my experience, every single query to the bot resulted in the same response: Result: Meanwhile, searching for the bot’s name on Telegram brings up a couple dozen results, differing by just a letter or two (like get_kontact_bott, get_kontakts_bot, and so forth). It seems like the project’s rising popularity has sparked a surge in people trying to profit from it. Some services, such as @Getcontact_official_bot, immediately demand a payment of 200 rubles to access the service. However, none of these bots actually seem to work.
I’m not sure whether this annoying issue is due to a flaw in the service’s logic or a sudden influx of users, but using the Get Contact Telegram bot is currently a waste of time.
“Eye of God”
Another popular bot, mentioned in several recent journalistic articles, offers a wide range of features: searching by name in plain text format, by vehicle number, phone number, email address, legal entity name, or tax identification number.
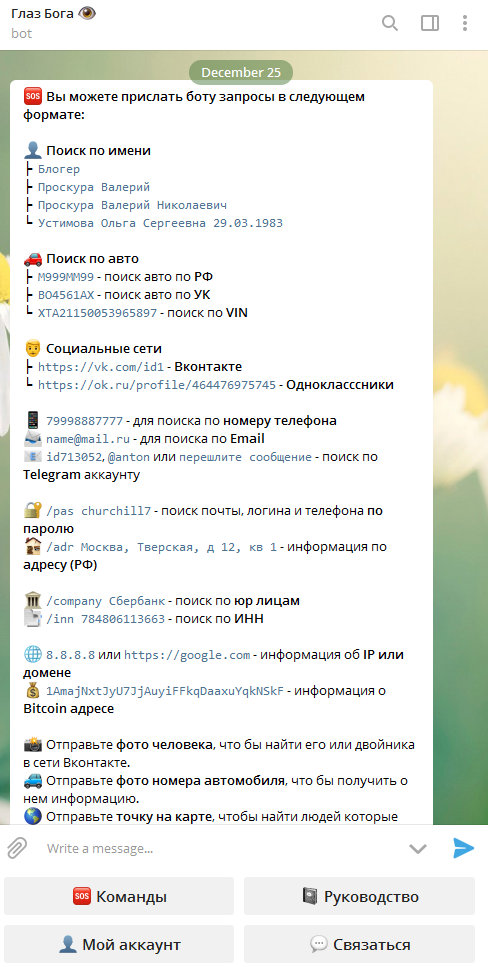
To send commands, the bot requires users to subscribe to its channel, but even that doesn’t guarantee success. The “Eye of God” phone number provides the operator’s name and region (presumably for those who can’t figure this out themselves), and possibly an associated name (I entered several phone numbers and the names matched). It can also find email addresses (most likely from domain administrator databases), a “VKontakte” page, a “Telegram” account, a WhatsApp account, and the number of people who searched for this person before you. However, this information is provided for a fee of 30 rubles. The same goes for automobile number searches: for free, the bot only displays the region (which can be determined elsewhere), but for 30 rubles it offers to download an “Avtocod” report. And, in fact, information about a vehicle by its number can easily be found for free on the web if you really want to.
If you enter an email address, the bot will generously show you the username (before the @ symbol) and the domain (after the @) — which is valuable information! You will also be offered the opportunity to purchase the VKontakte page associated with that email and any related passwords from a leaked database. The bot only searches by name to find a phone number in a specified region, and if it finds an incorrect one, it offers a subscription to view it.
Overall, the usefulness of this bot seems quite questionable to me: the information that “God’s Eye” provides for free can be found with a bit of Googling, and the paid information is limited and not always reliable.
AVinfo
A bot designed to verify vehicle history information using license plate numbers, VIN, title numbers, owner’s full name, or phone number, theoretically allowing the identification of “resellers.” It can easily help determine the owner of a car that’s blocking yours in a supermarket parking lot. The bot offers extensive capabilities at a relatively low cost: one report is priced at 150 rubles, but a subscription option is available.
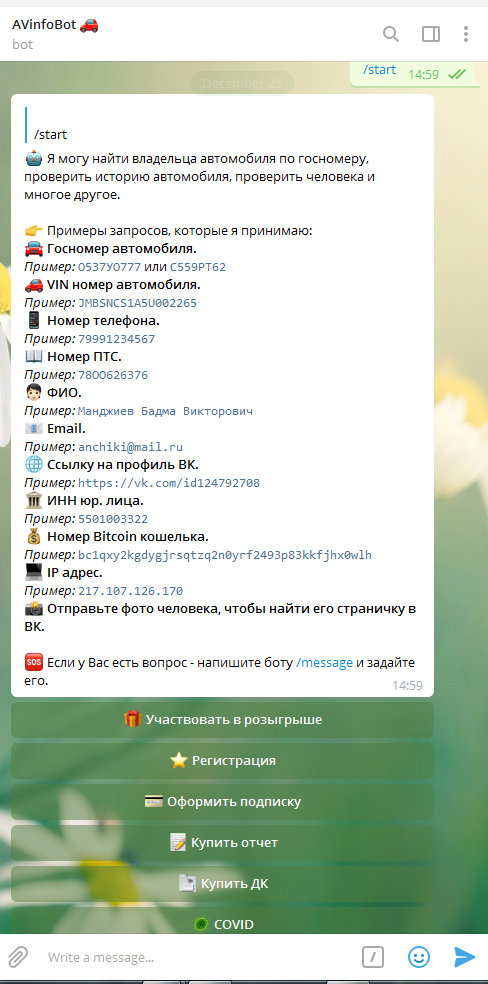
By using a phone number, you can find a “VKontakte” profile and ads for car sales, which theoretically allows you to identify car dealers. Additionally, by using the vehicle’s license plate or VIN, the bot can generate and offer to purchase a comprehensive report. This report includes detailed information about the car, its owners, mileage, all previously used license plates, any restrictions, search alerts, insurance status, accident history, usage as a taxi, court decisions, and any fines. Overall, this information is extremely useful if you’re planning to buy a car to cruise around with your friends through the streets of nighttime Moscow, while also wanting to ensure that the vehicle hasn’t been pieced together from wrecks in places like Dagestan. However, for simply finding information about the car’s owner, this level of detail would be excessive.
If you visit the bot channel but don’t order any paid services, after a while, it offers you a free trial report. I chose a report based on a phone number, and the bot found… only a fake “VKontakte” page registered to that number. It didn’t find any ads on “Avito” and “Yula” (probably because my accounts are linked to anonymous SIM cards), no car (since it’s registered to someone else, LOL), and nothing in the real estate database. In short, while AVinfo might be able to gather data based on a car’s license plate number, its ability to track down information on mobile numbers leaves much to be desired.
SmartSearchBot
An intriguing bot allows you to search by phone number, providing the user’s name, region, city, email, VK page, Telegram username, and ID if available. You can also search by email, returning the phone number, name, VK page, and city. Additionally, it can search by vehicle number, social media username or name, and even by a photograph to find similar images.
The free version of the bot allows only two requests before asking for a subscription, which costs about 67 rubles per day—quite affordable. I decided to invest this modest amount for a good cause and test the bot purely for research purposes.
For several car license plate numbers I entered, the bot didn’t find anything at all. It performed better with mobile phone numbers: information was found, and it seemed somewhat relevant. However, for some of the numbers I provided, the bot only returned the operator’s region and a user’s name, seemingly from someone’s address book, with no additional details available.
Based on a person’s last name, first name, and patronymic, the bot provides the name of an organization they might be associated with, a partial address (city, street), and a tax identification number (possibly by searching a database of legal entities and individual entrepreneurs). Some results only include a mobile phone number. If the last name is common, there may be many results, so you’ll need to refine your search using a combination of full name and date of birth or full name and city of residence. However, my experiments with the bot revealed that it uses outdated databases, like fossilized dinosaur droppings: all mobile numbers found from the test names I fed into it had long since gone inactive.
The bot provides quite comprehensive information based on an email address, including a link to the VK (VKontakte) page, the associated mobile number, and the full name from the user’s profile. An interesting outcome can be achieved with the “VK history” query. Even if a user’s profile is private, SmartSearchBot can extract a few photos and return information spanning several past years. This feature can be particularly useful if the user has deleted or cleaned their VK profile—at the very least, the bot can help identify their date of birth, place of residence, and workplace (if they were listed).
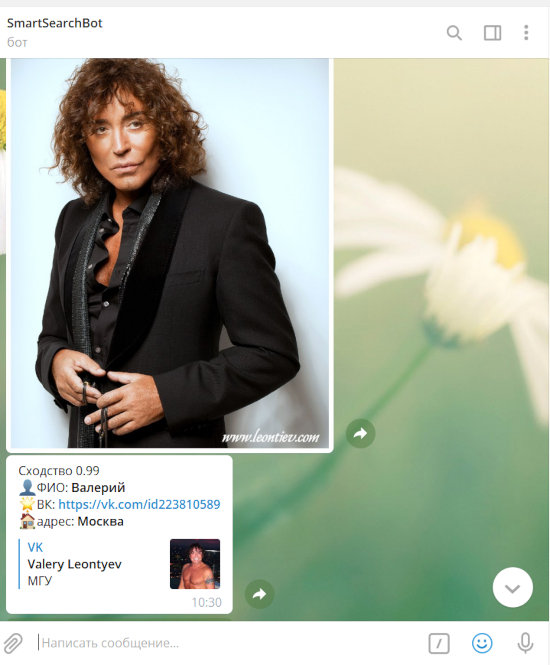
Finally, I decided to test searching by photo on social media. The bot allows up to three such searches per day. On a couple of photos I uploaded, SmartSearchBot inexplicably detected multiple faces (I swear there was only one!), and on others where the person was in profile, it didn’t find a face at all. By trial and error, I managed to feed it a small set of photos. Overall, the bot accomplished its task—although it requires the face in the photo to be front-facing and the user to have saved the exact or a very similar photo on their VKontakte profile.
Overall, I’d rate the Telegram bot SmartSearchBot as slightly above average. It does search and occasionally returns useful information, but more than half of the search results are irrelevant or low quality, requiring manual sorting.
Quick_OSINT_bot
The bot’s capabilities are quite similar to those of SmartSearchBot — it can search using a phone number, email address, license plate or vehicle VIN, passport number, Social Security Number (SSN), or Tax Identification Number (TIN). A noteworthy feature is its ability to search by password: the bot can look through leaked databases to find an email address that may be associated with a given password.
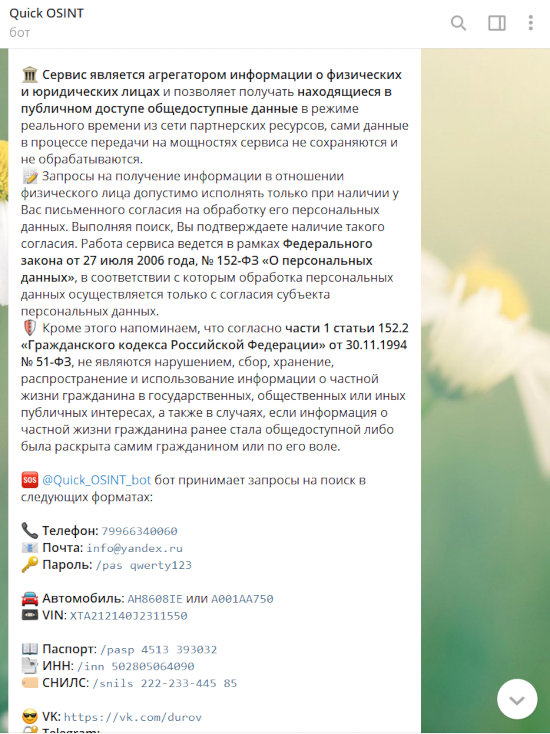
The test revealed that the Quick_OSINT_bot is not accurate in finding a mobile number through a vehicle’s license plate. It mainly returns the service provider’s region and the name saved in phone directories when queried with a phone number, as well as the name the individual uses on classified ads websites.
Conducting a search using an email address yields some very insightful results: the bot returns accounts associated with that email across various social networks, along with usernames, mobile numbers, first and last names (though not always accurately), and even passwords linked to that email from leaked databases.
The bot allows you to make a few free requests each day, after which it starts prompting you to pay: $0.10 for each report or it offers a subscription.
Himera
According to reports, the bot is connected to the counterparty verification system Unirate24, and it is a paid service. The cheapest plan, which limits the number of searches, costs 1199 rubles. The bot can search for information using a person’s full name, phone number, vehicle number, email address, and legal entity data. It is capable of finding details about a citizen’s residence registration, records of law violations, and information about relatives.
It is said that this Telegram bot does a decent job when searching in Moscow and the surrounding areas, but might face challenges in other regions since not all information is consistently available. A significant amount of information on legal entities is publicly accessible. Overall, the bot can be useful for vetting business associates, potential partners, or, for instance, when you’re considering hiring a suspicious candidate for a position in the gold vault of your private bank.
TeleSINT
A free bot that lets you find out which groups a user is a member of on Telegram by searching their username. In theory, this information might give you some insight into the interests and hobbies of the person you’re curious about.
A significant drawback of this bot is that it only reveals user participation in open public groups, while closed communities (which are often the most intriguing!) remain outside its scope.
“Archangel”
The bot that was heavily advertised on hacker forums in September 2020 is reportedly linked to the Solaris information and analytics system, which is used by professional data harvesters. This database enables users to search for information based on full names, passport series and numbers, last names and years of birth, as well as by taxpayer numbers, social insurance numbers, addresses, phone numbers, or vehicle numbers.
The cost of a single query to “Arkhangel” was recently 250 rubles, but following recent events, the bot has been disabled and currently displays a message about “temporary technical maintenance.” Let’s hope the issues are indeed temporary.
GetFB
The bot operates quite simply: by entering a mobile phone number in international format (+7XXXAAABBCC), GetFB finds the Facebook page registered to that number. The bot performs its task excellently and doesn’t charge for its services.
Mailsearchbot
The bot searches through leaked databases for passwords that match email addresses, usernames, or phone numbers. The bot provides only a partial display of the discovered passwords for free, and directs users to a third-party website for the full version, where they are immediately prompted to purchase a subscription.
Results
My experiments demonstrated that bots designed for searching personal data can generally be useful, but with a few caveats:
- Most of these services require payment, and the quality of search results is average at best; you’ll need to verify and sift through them manually.
- There are a couple of free options with a limit on the number of queries, but the search results often contain a high percentage of irrelevant information.
Even though most bots use the same sources of information, it’s better to use several tools for data verification to enhance the relevance of the search and the quality of the results. However, for a serious investigation, you can’t do without professional investigators: they have access to the current databases of various government and commercial organizations, or rather, connections with employees who, in turn, can access these databases.
Bots can help guide your search and expand the dataset, but they are unlikely to be a fully effective tool for collecting personal data.

2023.04.19 — Kung fu enumeration. Data collection in attacked systems
In penetration testing, there's a world of difference between reconnaissance (recon) and data collection (enum). Recon involves passive actions; while enum, active ones. During recon,…
Full article →
2022.02.15 — EVE-NG: Building a cyberpolygon for hacking experiments
Virtualization tools are required in many situations: testing of security utilities, personnel training in attack scenarios or network infrastructure protection, etc. Some admins reinvent the wheel by…
Full article →
2023.02.21 — Pivoting District: GRE Pivoting over network equipment
Too bad, security admins often don't pay due attention to network equipment, which enables malefactors to hack such devices and gain control over them. What…
Full article →
2022.01.12 — First contact. Attacks against contactless cards
Contactless payment cards are very convenient: you just tap the terminal with your card, and a few seconds later, your phone rings indicating that…
Full article →
2023.02.13 — First Contact: Attacks on Google Pay, Samsung Pay, and Apple Pay
Electronic wallets, such as Google Pay, Samsung Pay, and Apple Pay, are considered the most advanced and secure payment tools. However, these systems are also…
Full article →
2022.12.15 — What Challenges To Overcome with the Help of Automated e2e Testing?
This is an external third-party advertising publication. Every good developer will tell you that software development is a complex task. It's a tricky process requiring…
Full article →
2023.02.13 — Ethernet Abyss. Network pentesting at the data link layer
When you attack a network at the data link layer, you can 'leapfrog' over all protection mechanisms set at higher levels. This article will walk…
Full article →
2022.06.01 — Cybercrime story. Analyzing Plaso timelines with Timesketch
When you investigate an incident, it's critical to establish the exact time of the attack and method used to compromise the system. This enables you to track the entire chain of operations…
Full article →
2023.02.12 — Gateway Bleeding. Pentesting FHRP systems and hijacking network traffic
There are many ways to increase fault tolerance and reliability of corporate networks. Among other things, First Hop Redundancy Protocols (FHRP) are used for this…
Full article →
2022.01.11 — Pentest in your own way. How to create a new testing methodology using OSCP and Hack The Box machines
Each aspiring pentester or information security enthusiast wants to advance at some point from reading exciting write-ups to practical tasks. How to do this in the best way…
Full article →