OSCP (Offensive Security Certified Professional) is an ethical hacking certification offered by Offensive Security. The certification requires strong practical skills; so, expect plenty of fun (as well as pain and sleepless nights). In any case, the OSCP certification will be an excellent addition to your resume.
To become eligible for the exam, you have to pay the minimum price of $999. In exchange for this money, you will get the PWK (Penetration Testing with Kali) course materials, 30-day access to the lab where you can advance your practical skills, a set of videos, and an 853-page textbook in the PDF format.
Preparations
Most questions relate to the preparations. What to look for, what to download, where to practice?..
Prior to accessing the lab
Prior to purchasing the PWK course and accessing the lab, you have to learn plenty of things by your own (which is a characteristic feature of this profession: you always self-develop, self-study, and search for new information).
Note that both the training course and exam are based on Kali Linux; accordingly, you should be familiar with this OS. Kali Linux is a Debian-based distribution that includes all kinds of hacking software. Not everything works out of the box, not everything is optimized, but overall, Kali Linux gives you quick access to the tools you need. This distribution is not much different from any other kind of Debian (e.g. Ubuntu). If you had dealt with Linux before, you will surely figure it out. If not, you should study the Linux basics first.
What other knowledge and skills do you need? (If you already know the difference between LFI and LPE, you may skip this list.)
- some basic knowledge of computers: how the processor, memory, IO, buffer, heap, etc. interact with each other;
- basic understanding of Linux and Windows, including navigation and command shells;
- ability to program, at least at the simple script level;
- ability to use basic tools: Nmap, netcat, tcpdump (Wireshark), Metasploit, SearchSploit, gobuster (wfuzz, fuff), etc.;
- knowledge of various attack types, vulnerabilities, and exploitation techniques; and
- ability to escalate privileges on attacked and/or compromised machines (LPE and privesc).
I have no doubt that you can master the theory on your own. The main question is: where to practice?
The first platform where you can acquire practical hacking skills is Hack The Box. It offers numerous virtual machines with preset vulnerabilities that allow you to put your theoretical knowledge to practice. The platform has both subscription-based and free versions. The list of OSCP-like VMs on Hack The Box, compiled and maintained by TJnull, is available here.
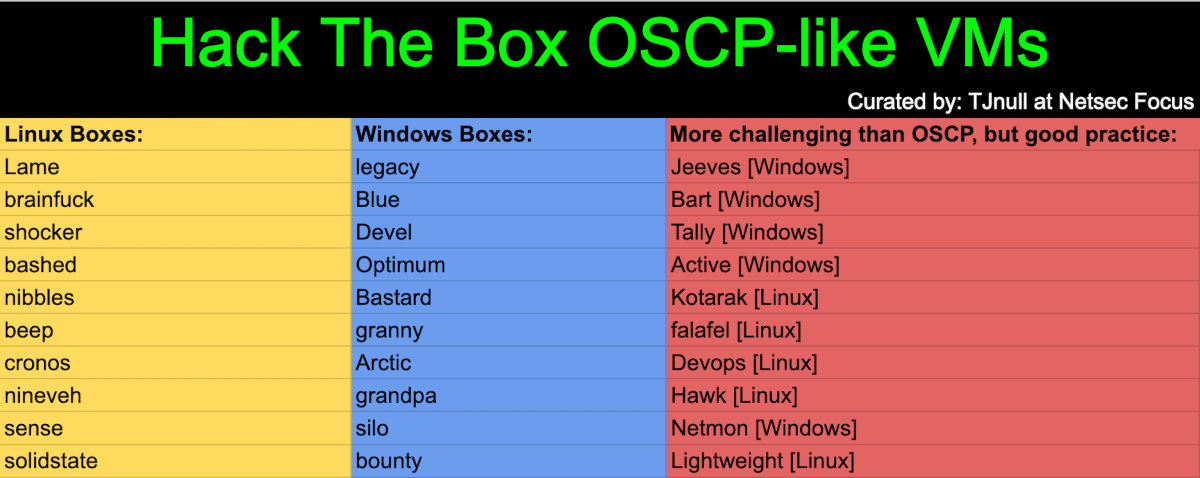
The majority of these VMs are ‘retired’ and therefore available only in the subscription-based version, which is 100% worth the money you pay for it.
Another platform you can use for practicing is VulnHub. This service also offers VMs with preset vulnerabilities, and you can deploy them on your home PC. A document available on Google Drive provides the list of OSCP-like machines on VulnHub. Some of them are pretty old, but OSCP often uses old and well-known vulnerabilities.
info
More information on Hack The Box, Root Me, and VulnHub can be found in the article entitled Where to study pentesting? An overview of training grounds for ethical hackers. In addition, HackMag publishes write-ups for various Hack The Box VMs on a regular basis.
IppSec publishes videos for all HTB machines; these videos demonstrate various exploitation techniques: recon, enumeration, privesc, etc. Furthermore, IppSec often shows how different methods can be used to achieve the same result. For instance, you can either scan ports with Nmap or quickly write a script in Bash or Python. Another example: you can use not only oldie-goodie DIRB for web content scanning, but alternative tools as well, including gobuster, fuff, and wfuzz (or even quickly write your own utility).
In fact, there are plenty of such services on the Internet: root-me, Web Security Academy, Hack this site, etc.
So, read write-ups, watch how other people hack vulnerable machines, learn, and practice. Try to hack VMs without using Metasploit; instead, search for exploits, edit them, and most importantly, get an understanding of how the things are working.
After hacking all the machines present on the above lists, you will be ready to take the PWK course.
In the lab
The course is offered in three versions; the only difference between them is the lab access period. In my opinion, if you have already hacked all machines listed by TJnull, then 60 days would the optimal variant for you. Alternatively, you can select 30 or (if you feel that this may take a while) 90 days; everything depends on your skills and financial situation.
After purchasing the course, you have to select the lab beginning date. You will be offered a few available dates; this is done to optimize the load on the lab. The links and logon credentials will be sent to you by email. I suggest immediately downloading the config for OpenVPN to avoid addressing the technical support and asking them to restore your access (as I had to do…). The link will be available for 72 hours.
On the selected day (in fact, night), you will be able to download the materials: the book and videos. All materials include a ‘watermark’ with your name, surname, and address that you have provided during the registration; this personal information is required to issue and receive the certificate. Therefore, I don’t recommend uploading these materials online! 🙂
The video is not different from the book; the announcer just reads it and demonstrates everything on a virtual machine.
This year, the course has been updated, significantly expanded, and refined. The following modules were added: Active Directory, PowerShell, Introduction to Buffer Overflow, and Bash scripting; the number of machines available for practice has increased. All other modules have been updated to varying degrees. However, the exam procedure remains unchanged (so far).
You will interact with the lab via VPN. For that purpose, you will need a standard OpenVPN client and a config for it with your username and password. There are 50-60 machines in the lab; some of them can be accessed only after hacking other VMs. There are no step-by-step instructions; so, everyone chooses their own way. The machines differ significantly by the difficulty level; some of them can be solved quickly and easily, while others are pretty painful. Overall, everything depends on your knowledge and practical skills.
The network is vibrant: users exchange messages, visit various websites, etc. Without exaggeration, this is an excellent place to study and have fun.
According to the course annotation, no special knowledge is required. On the one hand, this is correct: the course describes in detail the basic skills required for the exam and lab work. However, in reality (and this is also mentioned), you have to obtain most of the knowledge on your own. Therefore, it is imperative not only to take the course, but also to complete all tasks and solve the majority of machines available in the lab (if not all of them). Frankly speaking this is the main benefit of the course: you always study something, experiment, think, and develop.
I suggest to document the process from the very beginning; concurrently, you will learn how to do this. Note that you will need the writing skill during the exam. And if you write a report about your lab studies, you may be awarded additional points for that.
Make screenshots of all your actions, of the file system, ipconfig, ifconfig, and ip outputs, cat outputs, proof files, etc. For this purpose, I use two programs: CherryTree and Joplin. Handy templates (TJ-JPT and CTF_Template) are available on the Internet; use them to document the exam in the above programs. The templates include help and examples showing how to use their elements; a handy tree structure makes the navigation through them easy. But if you prefer other software, you can use it as well.
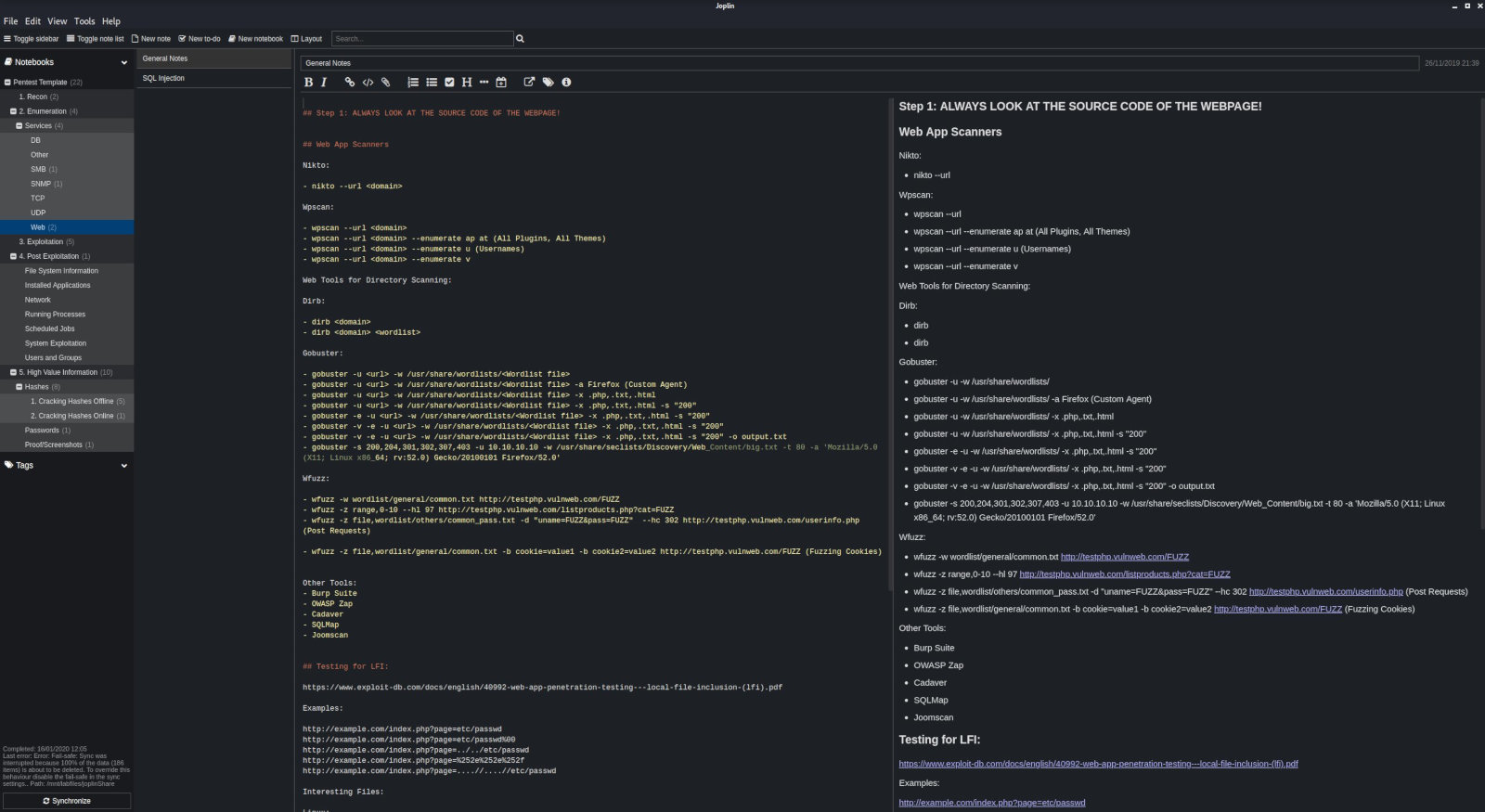
Automate all routine tasks, even simple ones: launching a web server to upload a shell on the target machine, shell generation for various purposes, etc. This saves your time as you don’t have to search the web or manually enter long commands.
After the end of the lab period, you have to select the exam date. This date must fall into a certain interval (i.e. you cannot take the exam a year after the lab).
Exam
You select the date and time of the exam using a special link sent to you along with the lab materials. After the beginning of the exam, you have 23 hours and 45 minutes to extract proof files from the required number of the test machines and gain at least 70 points required to pass the exam (the maximum possible result is 100 points plus you can gain 5 points for the lab report). The test machines are worth 10, 20, or 25 points, and their difficulty levels vary significantly.
After the exam, you have additional 24 hours to write the exam report. The result (i.e. passed or failed) comes in 10 workdays. You will need an ID understandable for the examiner.
The exam is now taken in the presence of an OS representative who watches the process through the camera. Sometimes, the examiner may ask you to rotate the camera around. Nobody else can be present in the room where you take the exam.
You cannot use at the exam:
- commercial tools (e.g. Burp Pro, Nessus Pro, and MSF Pro);
- tools automating the exploitation (e.g. sqlmap and browser_autopwn);
- vulnerability scanners (Nessus (even the essentials version), OpenVAS, etc.); and
- various spoofing techniques (IP, ARP, etc.).
It is also prohibited to use features of any other utilities falling under these restrictions.
Speaking of Metasploit, you can use it only once during the exam on one of the test machines at your choice, and you have only one attempt – even if it’s unsuccessful.
You can use without any limitations:
- exploit/multi/handler;
- pattern_create.rb;
- MSFvenom;
- pattern_offset.rb.
Offensive Security gives you 23 hours and 45 minutes taking that you need some time to eat, sleep, and visit washroom. If your Internet goes down, the time won’t be extended. Therefore, prepare a backup access point in advance.
Apart from this, the exam does not differ from a lab study. Don’t panic, even if you feel that you may fail. In the worst case scenario, all you have to do is pay for one more attempt. Therefore, enjoy your work, don’t be nervous, and everything will be fine.
And the last piece of advice: never give up! It really helped me – both at the OSCP exam and in many other real-life situations.
Conclusions
In my opinion, every person involved with practical information security should consider taking this exam. It won’t teach you everything (this is impossible, and there is no such a goal), but you will learn how to pursue a goal and study on your own. Concurrently, you will gain some valuable experience: understanding problems, working in stressful situations, and performing tasks when you are under severe restrictions.
This is not an ordinary test that requires only a good knowledge of the theory. To pass the exam, you must possess both the required skills and fundamental knowledge. The OSCP certification is an excellent proof of your mastery, and employers duly appreciate it.
Overall, there is nothing terrible or overcomplicated in the OSCP exam – provided that you have prepared well. Everything you need is easily available; so, it’s just a matter of time and desire. For me, this was a truly astonishing experience.
