
Today, I will give a brief overview of some of the best pentesting portals recognized by security experts. These training grounds enable ethical hackers to polish their skills while preserving ‘ethicality’ and exploit newly-discovered vulnerabilities while staying within the bounds of the law.
The IT industry is rapidly developing. Computers occupy more and more aspects of our everyday life. Digital systems become increasingly sophisticated, and, accordingly, the scope of the hackers’ attacks is steadily growing. As a result, the demand for security specialists, including ethical hackers, is increasing as well.
An ethical hacker must be proficient in all aspects of the Dark Side. If you know how to hack and your knowledge is up-to-date, then and only then you can provide useful security recommendations. Practice is everything, but how can you train your hacking skills without transgressing the law?
In the early 2000s, many cybersecurity enthusiasts were designated criminals even though their crimes were limited to curiosity.
Over time, hackers found many perfectly legal ways to improve their offensive security skills. Today, several online platforms are available to those willing to practice in hacking without the risk of being prosecuted.
INFO
This article is primarily focused on relatively free labs that provide access to their infrastructure without forcing you to buy a subscription. Speaking of commercial portals providing their clients, among other things, with extensive learning materials, I would like to mention Virtual Hacking Labs and PentesterLab Pro that are similar to the PWK training course.
Resource structure
Various pentesting resources are dedicated to different aspects of the hacking art. All these aspects can be divided into three large groups:
- CTF tasks – Capture the Flag exercises in the following categories: Exploit (or PWN), Web, Crypto, Stego, Forensics, OSINT, Misc, and, sometimes, PPC (Professional Programming Challenges). Many of such tasks are pretty straightforward: you download the files on your machine, find the flag, feed it to the website, and get your reward.
- Vulnerable virtual machines – these challenges are closer to the real life: you must hack a vulnerable host. The goal is to gain control over the privileged account in the system. To prove that you have seized the machine, you must be able to read files available only to users with certain privileges (and containing special ‘flags’). The hacking process depends on the portal hosting the target machine: it may be either a ‘live’ host operating on servers belonging to the portal (online lab) or downloadable images that you can run in the virtual environment on your own PC.
- Virtual local networks – normally, these are virtual Active Directory forests, and the users must seize the controller and entrench themselves in the network. To advance through the infrastructure, hackers may use various techniques: from open source intelligence (OSINT) and phishing to zero-day exploitation. The difficulty of such exercises is comparable to real-life cases or even exceeds them. Such laboratories usually operate on the commercial basis; their services are in high demand among people preparing for professional certification exams (e.g. OSCP).
To raise the enthusiasm of cybersecurity apprentices, owners of such resources often offer bonuses for completing tasks of various types, including fame points displayed in the user’s profile and the Hall of Fame. A high position in such a rating is a significant advantage at a job interview.
Let’s examine the largest and most famous portals where you can indulge your internal hacker.
Hack The Box
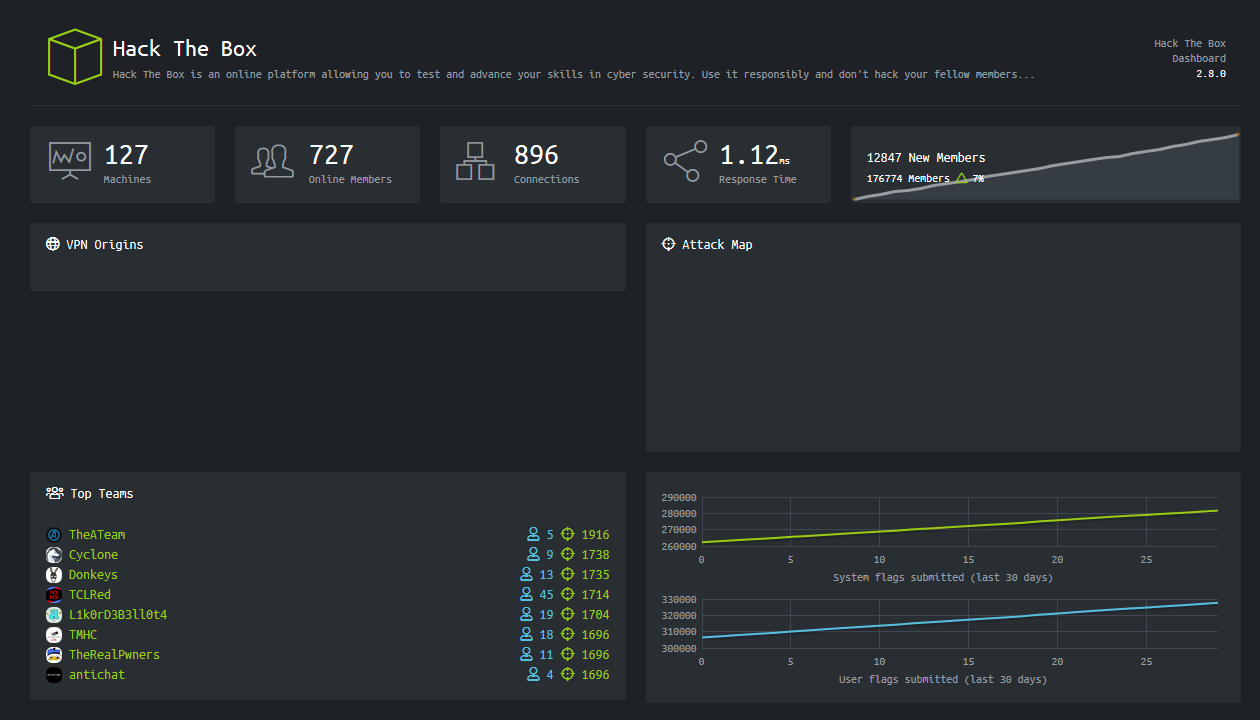
Hack The Box (HTB) is my favorite pentesting resource. This is one of the largest platforms of its kind: currently, HTB offers 127 vulnerable PCs, 65 CTF tasks, and several types of hardcore virtual AD forests. In other words, all the hacking areas listed above are present there.
In the last few years, Hack The Box became very popular among security researchers: its web interface allows to conveniently manage active instances of the virtual machines; its technical support is responsive; and, most importantly, its assortment of vulnerable hosts is renewed on a regular basis.
Every month, a new virtual PC is released, and all registered users can try to hack it. Concurrently, one of the machines previously available online goes to the pool of ‘retired’ VMs. In total, 20 virtual PCs are available online at a time… but only on the free server. After purchasing a VIP subscription (£10 per month or £100 per year), you gain access to all ‘obsolete’ machines stored in the pool and can test their vulnerabilities on a dedicated server. Furthermore, you gain access to official walkthroughs in the PDF format written by HTB specialists.
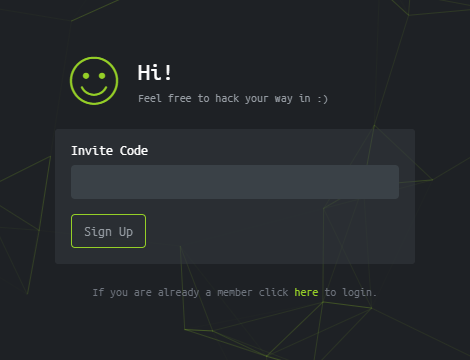
To register on Hack The Box, you have to solve a trivial web task first, and then you get an invite code. Therefore, this can be considered a semi-closed resource. Why “semi” closed? Because the task is very simple (at some point, I even wrote a one-string script to generate an invite code). I am not going to describe it in detail here; after all, it would be impolite to disclose the solution, thus, devaluating the work of the HTB team. Especially taking that plenty of guides can be found on the Internet…
The registration page is available to everybody; it welcomes you with inspiring “Congratulations!”; however, it is impossible to create an account without a previously generated invite code.
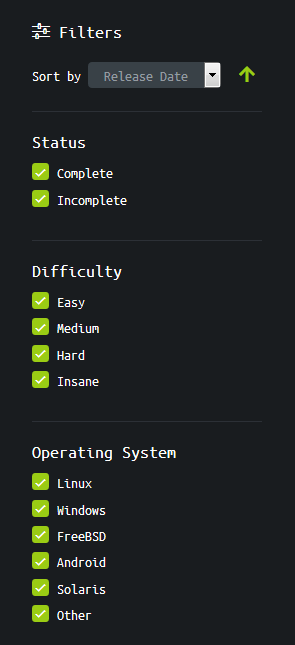
Most of the active instances are virtual machines with high difficulty levels; however, simple ‘dummies’ recommended for novice IT specialists are available as well. A flexible filtering system enables you to select an optimal machine whose difficulty matches your skill level.
INFO
HackMag has already published walkthroughs for some virtual PCs available on Hack The Box.
- The taming of Kerberos. Seizing control over Active Directory on a HackTheBox virtual PC
- The great mischief. Working your way to the root flag through IPv6 labyrinths on a Hack the Box virtual machine
- [Epic pivoting. Polishing traffic routing skills on HackTheBox virtual machines] (https://hackmag.com/security/htb-pivoting)
Important: Hack The Box uses services of DigitalOcean, a cloud infrastructure provider. Some of its IP addresses (and accordingly, HTB services) may be unavailable in certain countries. However, in this particular case (CTF web tasks), the vulnerable hosts are ‘directly’ connected to the Internet (i.e. unlike the main lab with VMs, are not hidden behind the VPN).
Root Me
Root Me is another unique portal where you can practice pentesting skills and solve CTF-like puzzles. It offers both CTF tasks, vulnerable VMs, and virtual local networks.
The CTF section includes as many as 11 subsections with 344 tasks.
In many of these challenges, you are interacting with a remote host (as opposed to dealing with local files of the task). A convenient function: you can use WebSSH for connection directly from the browser.
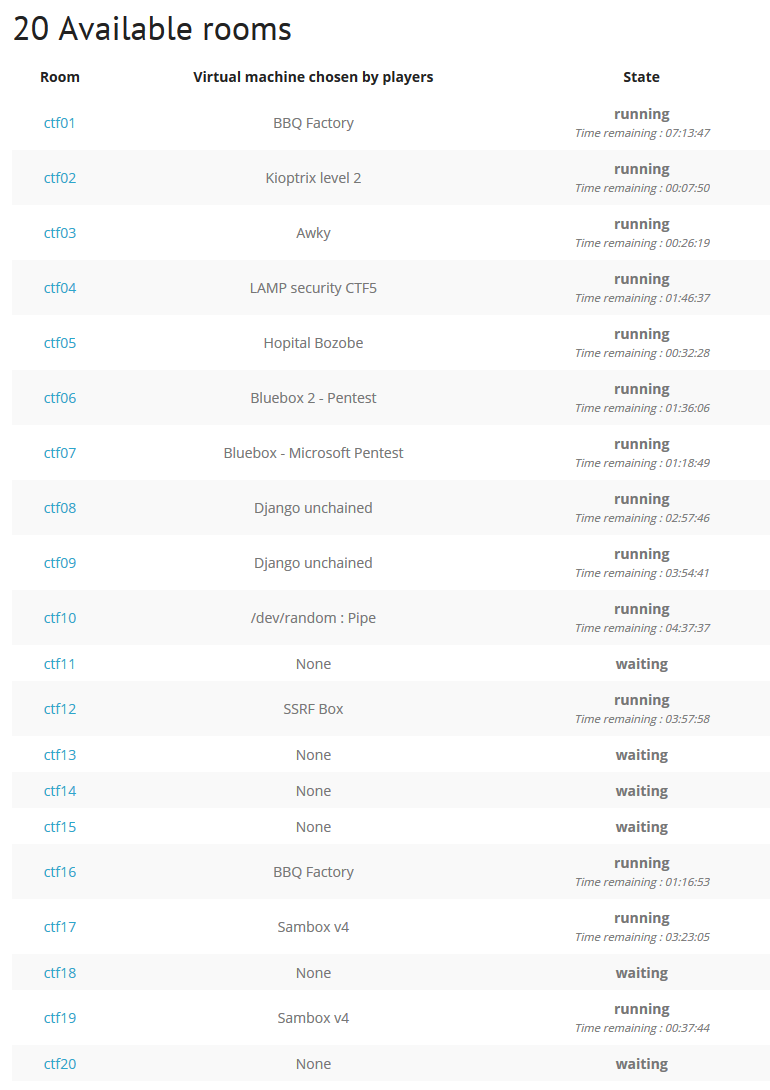
The most exciting feature of the portal is the CTF All the Day section: in this mode, you may choose one of the 20 rooms; this room remains active for four hours. Upon joining a room, you get brief information about the target and location of the flags. Some rooms are full-size labs with networks consisting of several VMs with an AD controller and a common legend. It takes plenty of effort to overcome them.
In my opinion, the general difficulty level on Root Me is slightly lower compared to Hack The Box. Still, the broad range of CTF tasks and possibility to practice with Active Directory on ‘lighter’ polygons make Root Me a must-have resource for pentesters.
VulnHub
VulnHub is an old dump of vulnerable VMs’ images maintained by enthusiasts. This resource if free; anyone can download a VM and start searching for the flags.
The main advantages of VulnHub are tons of write-ups about the available VMs and no limitations on their publication (Hack The Box and Root Me prohibit the publication of walkthroughs within a certain period of time; users violating this rule (and stupid enough to do this under their nicknames) may be banned).
The great selection of VMs and write-ups makes VulnHub an optimal starting point for novice hackers having no idea how to begin their pentesting experiments.
Disadvantages:
- Some machines lack meaningful descriptions. All VMs available on VulnHub can be divided into two large categories: task-based CTF and tasks resembling real-life situations. Every time you download a new image, you, in fact, take a pig in a poke and have no idea what kind of challenge you are up to.
- Absence of Windows-based VMs. This is understandable: after all, VulnHub is an open-source resource.
Apart from that, VulnHub is an excellent way to practice your skills on intriguing VM images created by security experts for security experts.
Recommendations for rookies
This section describes essentials you must be aware of if you intend to use any of the above resources.
Environment setting
- Virtualization tools are your best friends. Choose one of the solutions for work with VM images: VirtualBox or VMware for Windows or KVM for Linux, and stick to it. The ability to quickly deploy a guest operating system is a very useful skill, not only in the cybersecurity industry.
- Pentesting distributions rule. No matter what you select: Kali Linux, Parrot OS, BlackArch Linux, or Commando VM, all of them are handy and efficient. Personally, I would recommend Kali or Parrot to a novice hacker. No matter what you want to install, do it only in the virtual machine environment: otherwise, you may be exposed to malicious actions of other, not-so-ethical hackers when you connect to online labs (i.e. dedicated virtual networks) via a VPN.
- Master the console mode and reduce the usage of the GUI to the minimum; this skill is extremely useful in any IT sphere. Working in the command line, you will significantly increase your productivity, learn to focus on the current issue (as opposed to switching between windows), and won’t feel helpless in situations when the graphical interface is unavailable. Concurrently, master at least one terminal multiplexer (personally, I prefer tmux, but many hackers would likely disagree with me) to avoid switching between tabs in the terminal emulator window.
Hacking vulnerable VMs
- Along with “Try Harder!”, “Enumeration is the Key” is the most common response to calls for help on hackers’ forums. The initial collection of information about the target is the most tedious (and sometimes, most labor intensive) phase of a hacking campaign. The more initial data have been collected, the more information is available for analysis, the broader is the scope of possible attacks. Always have a reconnaissance (i.e. intel gathering) utility running in the background to check for possible attack vectors.
- Know your tools. The ability to apply the right tool in the right situation is the key to success. Extensive lists of useful pentesting programs are available online – but they are worthless is you don’t have first-hand experience with these utilities. While mastering a new program, never disregard the
mancommand and--helpoption to get a general understanding of its capacities. - Search for information online; Googling is not a shame! No one can comprehend the entire IT industry, and no one actually needs this: plenty of things can be instantly found on the Internet. Googling does not make you a script kiddie – provided that you can explain how you have achieved the required result (including technical details).
- Read blogs and write-ups of your colleagues, even if you have already conquered that particular machine. Different views on the same issue widen your horizon and enrich your knowledge. This is especially useful when your resources are limited.
- Take notes both in the course of pentesting attacks (CherryTree or KeepNote will help in this) and after a successful hack to put your newly-gained experience in order. The best way is to pen a write-up for the defeated PC: not only do you explain others how to hack it, but imprint this information in your memory as well.
Happy hacking!
WWW
Bonus: Antichat, a legendary hackers’ forum, has recently launched its own CTF playground. I hadn’t tried it yet, but can’t omit mentioning it.


Из платных аналогов, предоставляющих своим клиентам, помимо всего прочего, расширенные методические материалы, можно выделить Virtual Hacking Labs и PentesterLab Pro, схожие с курсом PWK.