Operators of the phishing campaign PoisonSeed have found a method to bypass FIDO (in this case — FIDO2 with WebAuthn) by exploiting the authentication mechanism between devices implemented in WebAuthn. The attackers deceive victims into approving login requests that originate from fake corporate portals.
Recall that the PoisonSeed campaign is based on phishing, with the ultimate goal of financial fraud. In the past, attackers hacked corporate accounts for email marketing and sent users emails containing pre-made seed phrases for cryptocurrency wallets.
In new attacks observed by experts from the company Expel, attackers do not exploit vulnerabilities in FIDO mechanisms; instead, they abuse a legitimate cross-device authentication feature.
This WebAuthn feature allows a user to authenticate on one device using a security key or authenticator app on another. Instead of physically connecting the key (for example, via USB), the authentication request is transmitted via Bluetooth or through a QR code.
The new PoisonSeed attacks begin by redirecting the victim to a phishing site that mimics a corporate portal for logging into Okta or Microsoft 365. After the victim enters their credentials, the phishing infrastructure uses this information in real-time to log into the actual portal.
In a typical situation, the victim would need to verify the login using their FIDO key. However, in this scheme, the phishing server initiates the login through a mechanism for logging in from another device. As a result, the real portal generates a QR code, which is then passed to the phishing page and displayed to the victim.
When a user scans this QR code with their smartphone or authenticator app, essentially, they are approving a login initiated by the attackers. This allows bypassing FIDO protection by switching to cross-device authentication, which does not require physical key connection and can be approved remotely.
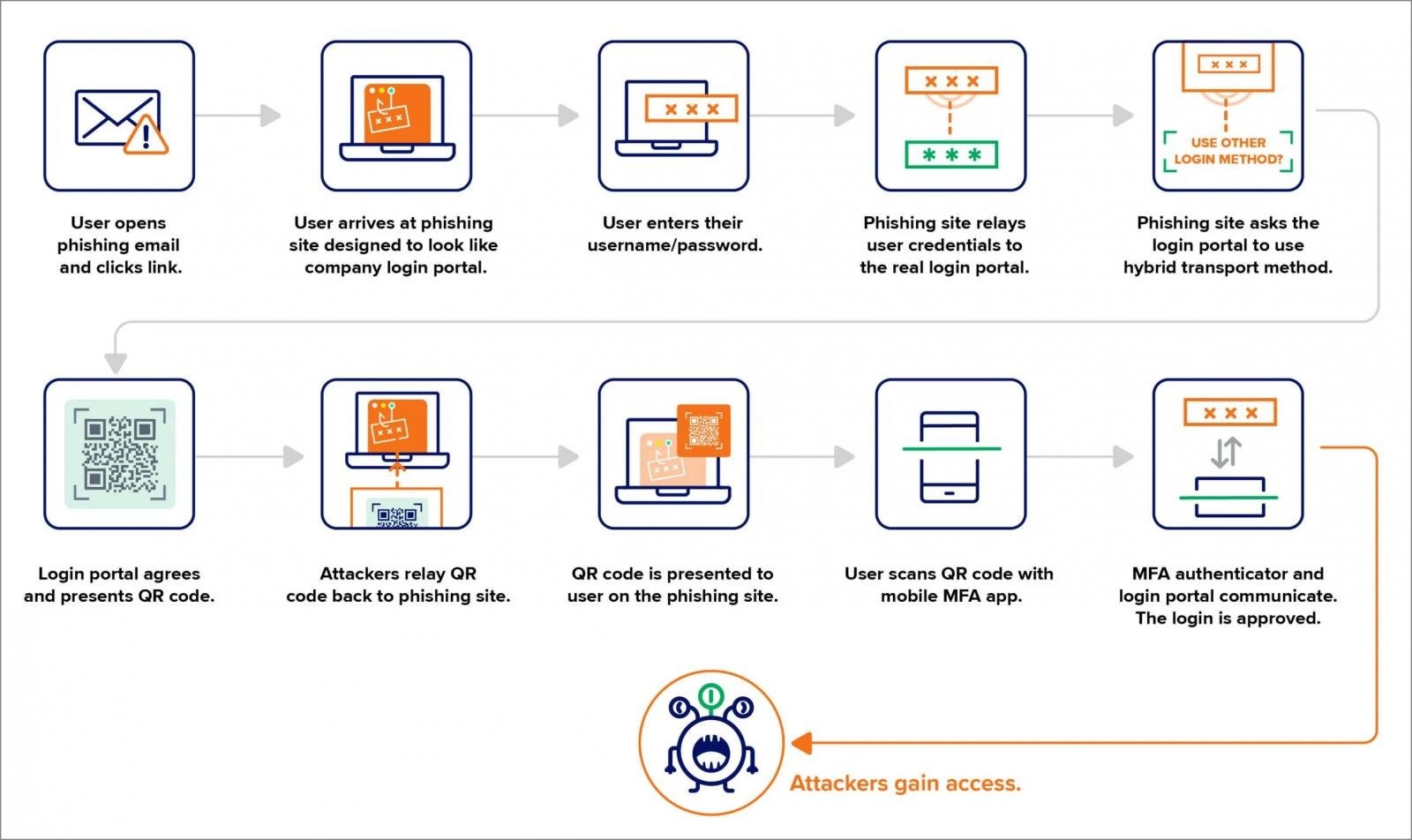
Researchers emphasize that the attack does not exploit any vulnerabilities in FIDO. Instead, the attackers misuse a standard feature that allows them to downgrade the level of protection.
To protect against such attacks, experts advise:
- limit geographical regions from which system access is allowed and implement a registration procedure for employees on business trips;
- regularly review the registration of new FIDO keys from unusual geolocations or from less-known manufacturers;
- whenever possible, require employees to use Bluetooth for inter-device authentication, which reduces the risk of remote attacks.
In their report, analysts at Expel describe another incident where an attacker registered their own FIDO key after compromising the victim’s account (presumably, through phishing). In this case, it wasn’t even necessary to spoof a QR code or interact with the victim — the login was completed entirely on the attacker’s side.
This case highlights that even phishing-resistant authentication methods can be bypassed if the user can be convinced to complete the login procedure without physical interaction with the key.
