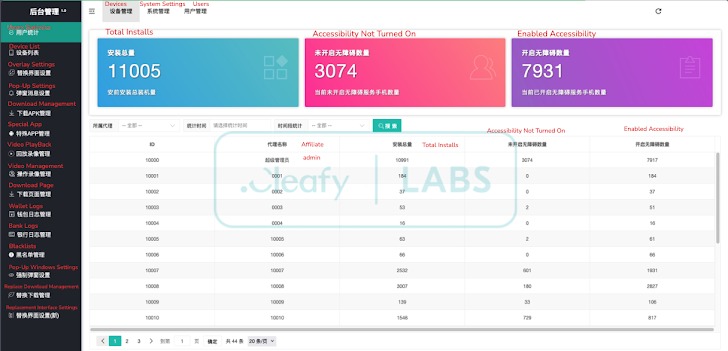
Experts from Cleafy discovered a new Android Trojan called PlayPraetor. According to their data, it has already infected over 11,000 devices, with more than 2,000 new infections recorded each week.
Currently, the malware is targeting users in Portugal, Spain, France, Morocco, Peru, and Hong Kong, but researchers report active campaigns aimed at Spanish-speaking and French-speaking audiences. This means that the operators of the malware are now attempting to shift their focus from previous victim categories.
Furthermore, in recent weeks, the malware has increasingly spread among Spanish-speaking and Arabic-speaking users, suggesting that PlayPraetor now operates under a MaaS (Malware-as-a-Service) model.
Experts report that PlayPraetor connects to a command server located in China and does not significantly differ from other Android trojans: it exploits Accessibility services to gain remote control over the device and is also capable of overlaying phishing screens on top of nearly 200 banking applications and cryptocurrency wallets to steal credentials.
PlayPraetor was first discovered by the company CTM360 in March 2025. At that time, researchers noted that attackers were using thousands of fake pages disguised as the Google Play Store to spread the malware. This scheme allows the malware operators to steal banking credentials, monitor clipboard contents, and intercept keystrokes.
“Links to fake Google Play Store pages are distributed through advertisements on social media and via SMS messages, which helps attackers reach a wider audience, researchers explained. – Fake ads and messages prompt users to click on links that lead to sites with malicious APK files.”
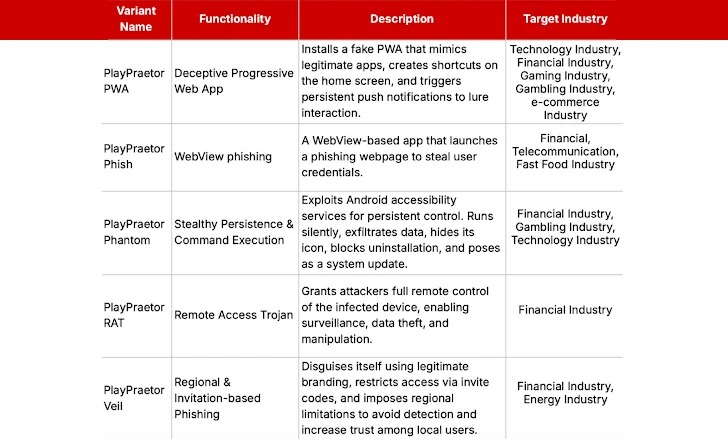
Experts report that PlayPraetor exists in five variants:
- PWA — installs fake Progressive Web Apps;
- Phish — based on WebView applications;
- Phantom — uses Accessibility services for constant device monitoring and communication with a command server;
- Veil — supports phishing via invitation codes and offers fake products;
- EagleSpy/SpyNote — variants of RAT with full remote access.
According to Cleafy, the Phantom variant carries out fraud directly on the victim’s device (on-device fraud, ODF). It is managed by two key affiliated hacker groups, controlling approximately 60% of the botnet (about 4,500 infected devices), and their activity is primarily focused on Portuguese-speaking countries.
“The primary functionality is based on the abuse of Accessibility services in Android, which gives operators extensive and almost instantaneous control over the infected device,” noted Cleafy. “This allows for fraudulent activities to be carried out directly from the victim’s device.”
After installation, the malware connects to the command server via HTTP/HTTPS and establishes a WebSocket connection for bidirectional command transmission. An RTMP session (Real-Time Messaging Protocol) is also initiated, allowing the attackers to view a live stream of everything happening on the infected device’s screen.
The list of supported commands for the Trojan is constantly expanding, indicating active development of the malware.
“The success of this campaign is based on a well-tuned operational structure and a malware-as-a-service model involving multiple affiliates,” note Cleafy researchers. “This structure enables large-scale and targeted campaigns.”
